Source: securityboulevard.com – Author: Joe Breen Hot Topics Advancing SOAR Technology: Key 2023 Updates in Incident Response Automation Unlocking CAPTCHAs: Moving Beyond Deterrence to Detection USENIX...
Month: December 2023
International Investigations Target Financial Cybercrime – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt International authorities took two big swipes at cybercriminals this week, with Interpol and others rounding up almost 3,500 suspects in...
Connectivity Enhancements and New Bulk Actions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi Product Update: Version 4.2 We’re wrapping up the year with one last release, adding a few more goodies. 4.2 comes...
Google Flags 8th Chrome Zero-Day of the Year – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Exploit for WebRTC Exists in the Wild Mihir Bagwe (MihirBagwe) • December 21, 2023...
Live Webinar | Maximizing OT Server Uptime in Automated Factory Floor Environments – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Operational Technology (OT) Presented by Acronis 60 minutes Register now to reserve...
NIST Report Spotlights Cyber, Privacy Risks in Genomic Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Healthcare , Industry Specific A Multitude of Considerations for Entities As Use of Genomic Data Advances...
Webinar | Securing Skies: Network Firewalls and the Battle Against Zero-Day Threats in the Cloud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Cisco Announces Isovalent Acquisition to Boost Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Security Operations Cisco Continues Investments in New Cloud Security Offerings With Isovalent Deal Chris Riotta (@chrisriotta) • December...
Breach Roundup: MongoDB Blames Phishing Email for Breach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Every week, Information Security Media Group rounds up cybersecurity incidents and breaches around the world. This week:, MongoDB said a phishing...
Ransomware Attacks in November Rise 67% From 2022 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Total ransomware cases up 30% from October Industrials (33%), Consumer Cyclicals (18%), Healthcare (11%), remain most targeted sectors North America (50%), Europe...
New DMARC Data Shows 75% Increase in Suspicious Emails Hitting Inboxes – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE 20 December 2023 – New data from EasyDMARC has revealed the increasing threat of phishing as emails intercepted by the...
‘BattleRoyal’ Hackers Deliver DarkGate RAT Using Every Trick – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Karel Tupy via Alamy Stock Photo This fall, an unidentified threat actor executed dozens of varied social...
Russian Water Utility Hacked in Retaliation for Kyivstar Hit – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading 1 Min Read Source: Andrii Dragan via Alamy Stock Photo According to reports, operations at Moscow-based water...
8 Strategies for Defending Against Help Desk Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: John A. Smith Source: Andriy Popov via Alamy Stock Photo COMMENTARY Defensive security techniques often lag offensive attack tactics, opening companies to...
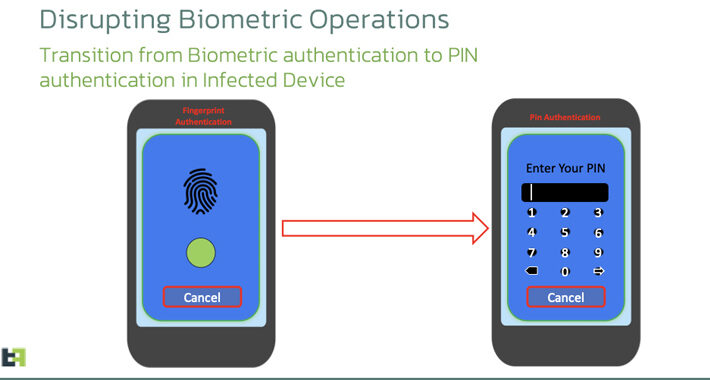
Chameleon Android Trojan Offers Biometric Bypass – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributing Writer A new variant of an Android banking Trojan has appeared that can bypass biometric security to break into...
How AI Is Shaping the Future of Cybercrime – Source: www.darkreading.com
Source: www.darkreading.com – Author: Richard De La Torre Source: marcos alvarado via Alamy Stock Photo COMMENTARY As cybersecurity experts predicted a year ago, artificial intelligence (AI) has...
As Namibians Rush to Register SIMs, Major Telco Hoards Biometric Data – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer Source: Universal Images Group North America LLC via Alamy Stock Photo This December, citizens of Namibia are faced...
5 Essential Insights From the ‘Microsoft Digital Defense Report 2023’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security Source: Ihor Svetiukha via Alamy Stock Since 2005, Microsoft has released annual security intelligence reports, now known as the “Microsoft...
Experts Detail Multi-Million Dollar Licensing Model of Predator Spyware – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 21, 2023NewsroomZero-Day / Mobile Security A new analysis of the sophisticated commercial spyware called Predator has revealed that its ability...
Chameleon Android Banking Trojan Variant Bypasses Biometric Authentication – Source:thehackernews.com
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered an updated version of an Android banking malware called Chameleon that has expanded its targeting to include...
New JavaScript Malware Targeted 50,000+ Users at Dozens of Banks Worldwide – Source:thehackernews.com
Source: thehackernews.com – Author: . A new piece of JavaScript malware has been observed attempting to steal users’ online banking account credentials as part of a...
The Four Layers of Antivirus Security: A Comprehensive Overview – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Valentin Rusu MACHINE LEARNING RESEARCH ENGINEER The antivirus software stands as a critical defense line against cyber-attacks. To fully understand how it...
Senate Confirms Biden’s Pick to Lead NSA and CYBERCOM – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Government , Industry Specific Senate Approves Pentagon Nominees After Republican Lawmaker Drops 10-Month Blockade Chris Riotta (@chrisriotta) • December 21, 2023...
Live Webinar | Enterprise Passkey Implementations: Key Considerations and Tradeoffs – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Cryptohack Roundup: Ledger to Reimburse Hack Victims – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Blockchain & Cryptocurrency , Cryptocurrency Fraud , Fraud Management & Cybercrime Also: $3M NFT Trader Theft; Binance’s CTFC Settlement Rashmi Ramesh...
Live Webinar | A Master Class on IT Security: Roger Grimes Teaches Ransomware Mitigation – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware , Video Presented by KnowBe4 60 mins Cyber-criminals have become thoughtful...
Webinar | Securing Skies: Network Firewalls and the Battle Against Zero-Day Threats in the Cloud – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
NIST Seeks Public Comment on Guidance for Trustworthy AI – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Agency Calls for Information on Gen AI Risk Management, Red-Teaming...
CISA Plans to Improve Threat Data-Sharing Approaches in 2024 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Government , Industry Specific , Next-Generation Technologies & Secure Development US Cyber Agency to Begin 2-Year Major Overhaul of Its Legacy...