Source: www.darkreading.com – Author: Dark Reading Staff Source: John Sirlin via Alamy Stock Photo Microsoft has observed the Iranian nation-state cyberattackers known as Peach Sandstorm attempting...
Month: December 2023
5 Tips for Strengthening the Developer-Security Team Relationship – Source: www.darkreading.com
Source: www.darkreading.com – Author: Aviv Mussinger Source: ronstik via Alamy Stock Photo COMMENTARY In the ever-evolving realm of software development, the interaction between developers and security...
Key Building Blocks to Advance American Leadership in AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jake Crisp Source: Kittipong Jirasukhanont via Alamy Stock Photo The AI era is set to be a time of significant change for...
How States Help Municipalities Build Their Cyber Defenses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Stephen Lawton, Contributing Writer Source: Image Professionals GmbH via Alamy Stock Photo As CISO for the state of North Dakota, Michael Gregg...
Bugcrowd Announces Vulnerability Ratings for LLMs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Source: Wavebreak Media Ltd via Alamy Stock Photo Bugcrowd has updated its Vulnerability Rating Taxonomy (VRT) with a new rating system to...
Comcast’s Xfinity Breached: Data of 36 Million Users Exposed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Citrix bugs caused a lot of problems throughout the year, and as we’re closing down 2023, it seems it’s not...
NSA Releases 2023 Cybersecurity Year in Review Report – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici The National Security Agency (NSA) has unveiled its ‘2023 Cybersecurity Year in Review’. This document highlights the agency’s achievements in...
Major Data Breach at ESO Solutions Affects 2.7 Million Patients – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici ESO Solutions, a key software provider for healthcare and emergency services, was the victim of a ransomware attack. This cyberattack...
UAC-0099 Using WinRAR Exploit to Target Ukrainian Firms with LONEPAGE Malware – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomMalware / Cyber Attack The threat actor known as UAC-0099 has been linked to continued attacks aimed at Ukraine,...
Microsoft Warns of New ‘FalseFont’ Backdoor Targeting the Defense Sector – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 22, 2023NewsroomThreat Intelligence / Supply Chain Attack Organizations in the Defense Industrial Base (DIB) sector are in the crosshairs of...
Google Cloud’s Cybersecurity Predictions of 2024 and Look Back at 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Google Cloud’s team recently spoke about the most notable cybersecurity threats of 2023 — multi-faceted extortion and zero-day exploitation —...
Third-Party Supply Chain Risk a Challenge for Cyber Security Professionals in Australia – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Ben Abbott Third-party supply chain risk is a key concern from Australian cyber security professionals. With enterprises typically relying on an expanding...
The future of AI and ML (in 2024) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In businesses everywhere, mention of Artificial Intelligence (AI) simultaneously evokes a sense of optimism, enthusiasm and skepticism, if not...
Crypto drainer steals $59 million from 63k people in Twitter ad push – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google and Twitter ads are promoting sites containing a cryptocurrency drainer named ‘MS Drainer’ that has already stolen $59 million...
Lapsus$ hacker behind GTA 6 leak gets indefinite hospital sentence – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Lapsus$ cybercrime and extortion group member, Arion Kurtaj has been sentenced indefinitely in a ‘secure hospital’ by a UK judge. Kurtaj...
Microsoft: Hackers target defense firms with new FalseFont malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says the APT33 Iranian cyber-espionage group is using recently discovered FalseFont backdoor malware to attack defense contractors worldwide. “Microsoft has...
First American takes IT systems offline after cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan First American Financial Corporation, the second-largest title insurance company in the United States, took some of its systems offline today...
Microsoft deprecates Defender Application Guard for some Edge users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is deprecating Defender Application Guard (including the Windows Isolated App Launcher APIs) for Edge for Business users. Microsoft Defender...
OpenAI rolls out imperfect fix for ChatGPT data leak flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas OpenAI has mitigated a data exfiltration bug in ChatGPT that could potentially leak conversation details to an external URL. According...
BidenCash darkweb market gives 1.9 million credit cards for free – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The BidenCash stolen credit card marketplace is giving away 1.9 million credit cards for free via its store to promote...
Android malware Chameleon disables Fingerprint Unlock to steal PINs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Chameleon Android banking trojan has re-emerged with a new version that uses a tricky technique to take over devices...
ESET fixed a high-severity bug in the Secure Traffic Scanning Feature of several products – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini ESET fixed a high-severity bug in the Secure Traffic Scanning Feature of several products Pierluigi Paganini December 21, 2023 ESET...
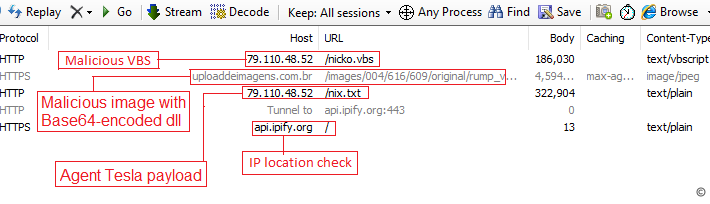
Phishing attacks use an old Microsoft Office flaw to spread Agent Tesla malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Phishing attacks use an old Microsoft Office flaw to spread Agent Tesla malware Pierluigi Paganini December 21, 2023 Threat actors...
Data leak exposes users of car-sharing service Blink Mobility – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Data leak exposes users of car-sharing service Blink Mobility Pierluigi Paganini December 21, 2023 More than 22,000 users of Blink...
Advancing SOAR Technology: Key 2023 Updates in Incident Response Automation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pierre Noujeim In 2023, we’ve achieved a remarkable milestone in the cybersecurity landscape by securing 70% of our new business from security...
Unlocking CAPTCHAs: Moving Beyond Deterrence to Detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ayan Halder Over the last six days alone, Arkose Labs identified and thwarted 189 million attacks for our customers alone. By tracking...
USENIX Security ’23 – Domien Schepers, Aanjhan Ranganathan, Mathy Vanhoef – ‘Framing Frames: Bypassing Wi-Fi Encryption By Manipulating Transmit Queues’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, December 21, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...
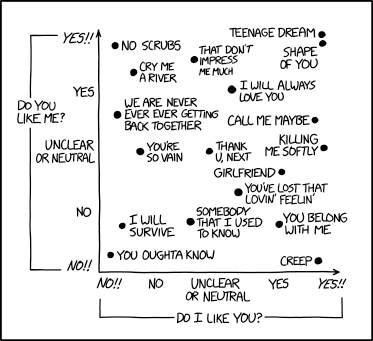
Randall Munroe’s XKCD ‘Love Songs’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/12/randall-munroes-xkcd-love-songs/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
Unraveling the Struts2 security vulnerability: A deep dive – Source: securityboulevard.com
Source: securityboulevard.com – Author: Aaron Linskens Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/12/unraveling-the-struts2-security-vulnerability-a-deep-dive/ Category & Tags: Security Bloggers Network,Vulnerabilities,Apache Struts2,DevZone,Security...
USENIX Security ’23 – Min Shi, Jing Chen, Kun He, Haoran Zhao, Meng Jia, and Ruiying Du – Formal Analysis And Patching Of BLE-SC Pairing – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Thursday, December 21, 2023 Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News...