Source: securityaffairs.com – Author: Pierluigi Paganini Spotify music converter TuneFab puts users at risk Pierluigi Paganini December 30, 2023 TuneFab converter, used to convert copyrighted music...
Day: December 30, 2023
Cyber attacks hit the Assembly of the Republic of Albania and telecom company One Albania – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cyber attacks hit the Assembly of the Republic of Albania and telecom company One Albania Pierluigi Paganini December 29, 2023...
Russia-linked APT28 used new malware in a recent phishing campaign – Source: securityaffairs.com
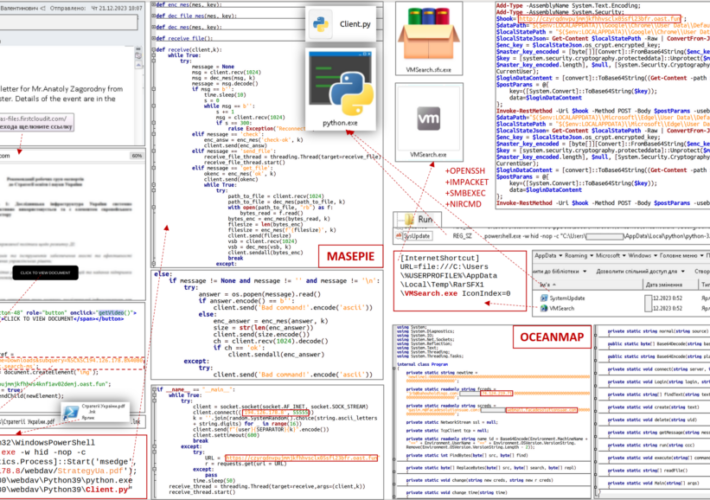
Source: securityaffairs.com – Author: Pierluigi Paganini Russia-linked APT28 used new malware in a recent phishing campaign Pierluigi Paganini December 29, 2023 Ukraine’s CERT (CERT-UA) warned of...
Beware: Scam-as-a-Service Aiding Cybercriminals in Crypto Wallet-Draining Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Dec 30, 2023NewsroomCryptocurrency / Phishing Scam Cybersecurity researchers are warning about an increase in phishing attacks that are capable of draining...
In Other News: Ubisoft Hack, NASA Security Guidance, TikTok Requests iPhone Passcode – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News Noteworthy stories that might have slipped under the radar: Ubisoft investigating alleged hack, NASA releases security guidance, TikTok scares iPhone...
Pentagon Wants Feedback on Revised Cybersecurity Maturity Model Certification Program – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire DoD is requesting public opinion on proposed changes to the Cybersecurity Maturity Model Certification program rules. The post Pentagon Wants...
Vulnerabilities in Google Kubernetes Engine Could Allow Cluster Takeover – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Two flaws in Google Kubernetes Engine could be exploited to escalate privileges and take over the Kubernetes cluster. The post...
‘Operation Triangulation’ Spyware Attackers Bypass iPhone Memory Protections – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: leonello calvetti via Alamy Stock Photo A previously undocumented hardware feature within Apple’s iPhone System on a...
Palo Alto Networks Closes Talon Cybersecurity Acquisition – Source: www.darkreading.com
Source: www.darkreading.com – Author: PRESS RELEASE SANTA CLARA, Calif., Dec. 28, 2023 /PRNewswire/ — Palo Alto Networks (NASDAQ: PANW), the global cybersecurity leader, today announced that it has completed...
I Securely Resolve: CISOs, IT Security Leaders Share 2024 Resolutions – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer Source: cn0ra via Alamy Stock Photo With the aim of fortifying defenses and navigating changing risks, IT security...
The Week in Ransomware – December 29th 2023 – LockBit targets hospitals – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams It’s been a quiet week, with even threat actors appearing to take some time off for the holidays. We did...
Hospitals ask courts to force cloud storage firm to return stolen data – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Two not-for-profit hospitals in New York are seeking a court order to retrieve data stolen in an August ransomware attack...
Malware abuses Google OAuth endpoint to ‘revive’ cookies, hijack accounts – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Multiple information-stealing malware families are abusing an undocumented Google OAuth endpoint named “MultiLogin” to restore expired authentication cookies and log...
Steam game mod breached to push password-stealing malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Downfall, a fan expansion for the popular Slay the Spire indie strategy game, was breached on Christmas Day to push...
Data Breach Impacts LoanCare Customers – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Over 1.3 million customers across the U.S. are being alerted by mortgage servicing company LoanCare that a data breach at...
Lockbit Ransomware Attack Affects Three German Hospitals – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Katholische Hospitalvereinigung Ostwestfalen (KHO), a German hospital network, has confirmed that a cyberattack launched by the Lockbit ransomware group is...
USENIX Security ’23 – ‘Tubes Among Us: Analog Attack on Automatic Speaker Identification’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Authors/Presenters: Shimaa Ahmed, Yash Wani, Ali Shahin Shamsabadi, Mohammad Yaghin, Ilia Shumailov, Nicolas Papernot, Kassem Fawaz Many thanks to USENIX...
Randall Munroe’s XKCD ‘Hydrothermal Vents’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
USENIX Security ’23 – Xinghui Wu, Shiqing Ma, Chao Shen, Chenhao Lin, Qian Wang, Qi Li, Yuan Rao ‘KENKU: Towards Efficient And Stealthy Black-box Adversarial Attacks Against ASR Systems’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Cloud Security, Governance and Skills in 2024 Step 1 of 6 16% Who in your organization is responsible for cloud...
Billion times emptiness – Source: securityboulevard.com
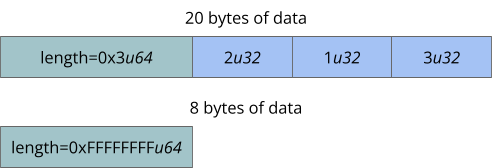
Source: securityboulevard.com – Author: Trail of Bits By Max Ammann Behind Ethereum’s powerful blockchain technology lies a lesser-known challenge that blockchain developers face: the intricacies of...
Best of 2023: Combo Lists & the Dark Web: Understanding Leaked Credentials – Source: securityboulevard.com
Source: securityboulevard.com – Author: Yuzuka As we close out 2023, we at Security Boulevard wanted to highlight the most popular articles of the year. Following is...
MQTT vs AMQP – Source: securityboulevard.com
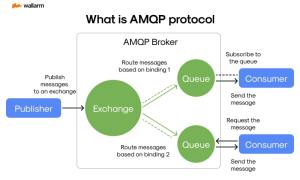
Source: securityboulevard.com – Author: Ivan Novikov The Initial Overview: Learning about MQTT & AMQP In the dynamic arenas of Internet of Things (IoT) and cloud computing,...
Weekly Blog Wrap-Up (December 25- December 28 , 2023) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tim Walker Welcome to the TuxCare Weekly Blog Wrap-Up – your go-to resource for the latest insights on cybersecurity strategy, Linux security,...
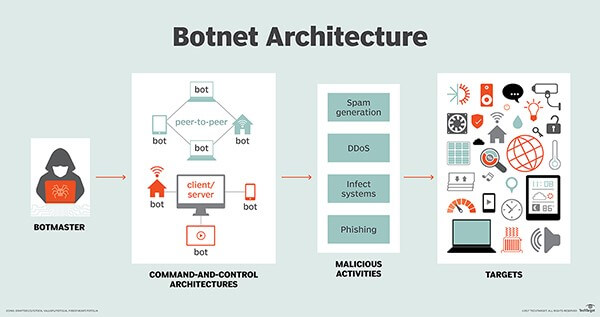
10 Botnet Detection and Removal Best Practices – Source: securityboulevard.com
Source: securityboulevard.com – Author: Venkatesh Sundar If your device suddenly behaves like a re-animated zombie, you might be under a Botnet attack. Also known as a...
Indian IT Leaders Identify Security Gap in Data Policies – Source: securityboulevard.com
Source: securityboulevard.com – Author: Shikha Dhingra A recent study by Rubrik, a US-based data security firm, has bare concerning reality within the Indian IT sector: an...
Info-Stealing Malware Now Includes Google Session Hijacking – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Access Management , Cybercrime , Cybercrime as-a-service Google OAuth2 Vulnerability Being Actively Abused by Attackers, Researchers Warn Chris Riotta (@chrisriotta) •...
How One University Is Beefing Up Cyber Defenses, Programs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Business Continuity Management / Disaster Recovery , Critical Infrastructure Security , Cybercrime Steve Zuromski, CIO at Bridgewater State University, on New...
Russian Military Intelligence Blamed for Blitzkrieg Hacks – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Ukrainian Cyber Defenders Trace Government Agency Hits to Phishing Campaign Mihir Bagwe...
OpenAI and Microsoft Face New York Times Copyright Lawsuit – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Legislation & Litigation , Standards, Regulations & Compliance Media Giant Alleges ‘Billions of Dollars in Statutory and Actual Damages’ Rashmi Ramesh...
Microsoft Disables Abused Application Installation Protocol – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Attackers Have Been Exploiting App Installer to Evade Malware Defenses in Windows Mihir Bagwe...