Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer Source: Peter Kovac via Alamy Stock Photo Faced with numerous cybersecurity threats and challenges, but lacking adequate cyber...
Day: December 27, 2023
GenAI Tools Will Permeate All Areas of the Enterprise – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff Source: The State of Generative AI in the Enterprise, Dark Reading Research, 2023 There is significant interest among organizations...
Security Pros Grapple With Ways to Manage GenAI Risk – Source: www.darkreading.com
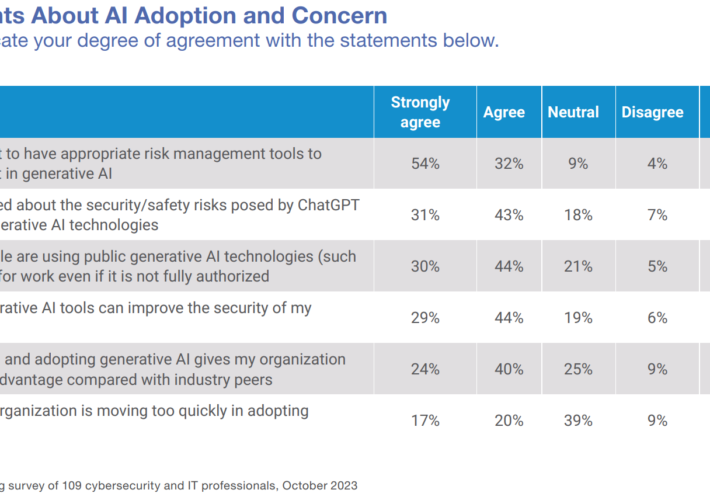
Source: www.darkreading.com – Author: Edge Editors Source: The State of Generative AI in the Enterprise, Dark Reading, 2023 While security professionals are generally enthusiastic about the...
USENIX Security ’23 – Carter Slocum, Yicheng Zhang, Nael Abu-Ghazaleh, Jiasi Chen ‘Going Through The Motions: AR/VR Keylogging From User Head Motions’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnaravi – #272 — Product Ops – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Wrapping up Q4 2023 : new detectors, your favorite features, and what’s coming next in GitGuardian – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ziad Ghalleb GitGuardian Secrets Detection More detectors = more secrets caught This quarter, our dedicated security research team has unveiled 14 new...
USENIX Security ’23 – Zhuolin Yang, Yuxin Chen, Zain Sarwar, Hadleigh Schwartz, Ben Y. Zhao, Haitao Zheng ‘Towards A General Video-Based Keystroke Inference Attack’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
We’ve added more content to ZKDocs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Trail of Bits By Jim Miller We’ve updated ZKDocs with four new sections and additions to existing content. ZKDocs provides explanations, guidance,...
Twas the day after Christmas, and this family was smart… – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog No one specifically Someone on our general security team A dedicated person/team that handles cloud security Cloud architects and developers...
Best of 2023: Detecting CVE-2023-23397: How to Identify Exploitation of the Latest Microsoft Outlook Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security As we close out 2023, we at Security Boulevard wanted to highlight the most popular articles of the year. Following...
How to Unsend an Email and Save Yourself from Oops Moments? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ahona Rudra You drafted an email, hit the ‘send’ button, but forgot to attach the file, or got the recipient’s name wrong-...
SLAM Attack: New Vulnerability Targets Intel, AMD, Arm CPUs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rohan Timalsina In a groundbreaking revelation, researchers from Vrije Universiteit Amsterdam have uncovered a formidable side-channel attack known as SLAM, posing a...
UEFI Failing: What to Know About LogoFAIL Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Joao Correia Multiple UEFI vulnerabilities can lead to Linux, Windows, and Mac exploits LogoFAIL persists across operating system reinstallations It also extends...
The CyberSherpas guide on Generative Al Security It’s a Generative Al World
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Vendor Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
GitHub warns users to enable 2FA before upcoming deadline – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar GitHub is warning users that they will soon have limited functionality on the site if they do not enable two-factor...
Integris Health patients get extortion emails after cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Integris Health patients in Oklahoma are receiving blackmail emails stating that their data was stolen in a cyberattack on the...
Kazakhstan to Extradite Russian Hacker to Moscow – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime Nikita Kislitsin Has Twice Been Indicted in the United States Mihir Bagwe (MihirBagwe) • December...
Fighting AI-Fueled Attacks With AI-Based Cyber Tools – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Healthcare , Industry Specific Troy Hawes of Moss Adams on How Healthcare Entities Can Bolster...
Panel Discussion featuring Forrester Analyst | A CISO Guide to Calculating the ROI of Prisma Cloud – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Luca Son Consultant, Total Economic Impact, Forrester Luca Son is a consultant with Forrester’s Total Economic Impact™ (TEI) practice. In this...
NASA Releases First Space Cybersecurity Best Practices Guide – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific Agency Set to Bolster Space Cybersecurity Efforts Across Public and Private Sectors...
CYBERSECURITY TOOLKIT FOR ENTERPRISE LEADERS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity of Artificial Intelligence in the AI Act
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity for Fire Protection Systems
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CYBER SECURITY AWARENESS HANDBOOK
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity Awareness for Kids Age 10 to 15
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Managing Cyber Risk
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Chief
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...