The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: November 1, 2023
Q2-2023Ransomware Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Azure Defenses for Ransomware Attack by Microsoft Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ransomware Hostage Rescue Manual
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ransomware Investigation osint and hunting Overview PT1
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Ransomware, extorsion and the cyber crime ecosystem by NCSC & NCA
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Risk Mitigation , Prevention and Cutting the Kill Chain – Minimize the impact of ransomware with Akamai Guardicore Segmentation
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ISACA Ransomware Incident Response -23
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Detecting and Responding to Ransomware
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Stop Ransomware Guide May 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
A Review Ransomware Intrusion
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Countering Ransomware Financing – FATF Report March 2023
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ISACA Ransomware Incident Management Quick Reference Guide
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Ransomware Diaries – Volume 2 – A Ransomware Hacker Origin Story by Jon DiMaggio
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Splunk Queries for SOC Analyst
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
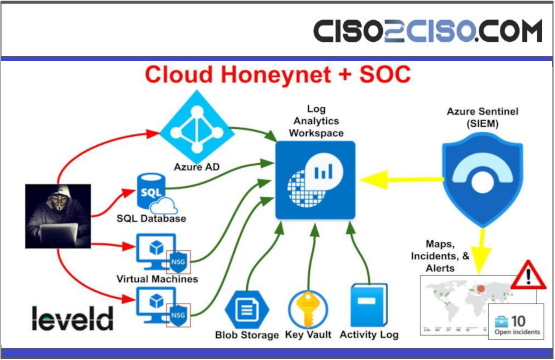
Building a SOC Honeynet in Azure
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Becoming a SOC analyst V1
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SOC Analyst Interview Questions
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
11 Estrategies a World- Class SOC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Commonly Asked SOC Analyst Interview
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Why do we compare a SOC (Security Operations Center) with the cockpit of a commercial airplane? by Marcos Jaimovich
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Operations Center (SOC) – Tools for Operations Development by Joas Antonio
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
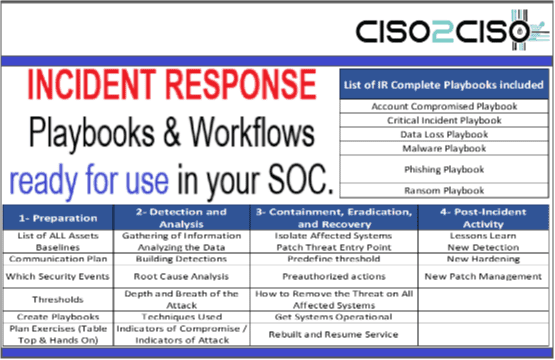
Incident Response Playbooks & Workflows Ready for use in your SOC & Redteams
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
396 Use Cases & Siem Rules Code ready for use for Mitre Attacks Events Detection in Your SOC by Logpoint
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Global Risks Report 2023 – Insight Report – 18th Edition by World Economic Forum (WEF). Economics, Environmental, Geopolitical, Societal, Technological & Cyber Risks Included in the report.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Orange Cyberdefense Security Navigator 2023 – Research-driven insights to build a safer digital society
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Adapt Or Die: XDR Is On A Collision Course With SIEM And SOAR – EDR Is Dead, Long Live XDR by Allie Mellen – Forrester
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How to Avoid Party Chaos with the Right Application-Layer DDoS Platform whitepaper by Akamai
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Solution Brief Recent Web DDoS Threats How to Stay Protected
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OSINT cheat Sheet
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...