The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Month: October 2023
The Coming AI Hackers – Council for the responsible use of AI by Bruce Schneier
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ChatGPT for Cybersecurity by Joas Antonio dos Santos – malwareanalysis #reverseengineering
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Digest of Cyber Organized Crime by UNODC – United Nations Office on Drugs and Crime
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity in a Digital Era by McKinsey. Digital McKinsey and Global Risk Practice.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Threat Hunting Survival Guide by Microsoft Security Experts
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CROWDSTRIKE 2023 GLOBAL THREAT REPORT
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Reporte sobre el desarrollo de la FUERZA LABORAL DE CIBERSEGURIDAD 2023 by OEA, CIC y CISCO en una era de escasez de talento y habilidades.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Top Risk in Cybersecurity 2023 by Bipartisan Policy Center
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ESSET THREAT REPORT T2 2022
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
SECURITY OF THE DOMAIN NAME SYSTEM (DNS) – AN INTRODUCTION FOR POLICY MAKERS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
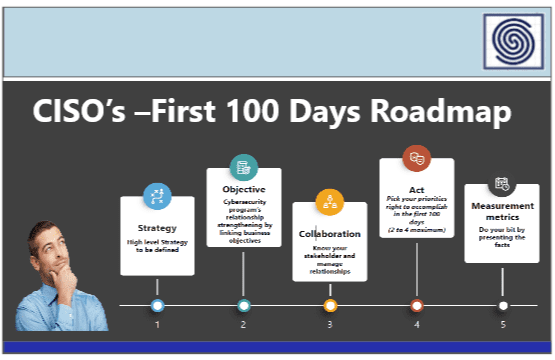
CISO’s – First 100 Days Roadmap – Your success as a security leader is determined largely by your first 100 days in the role.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Organising a Cyber Crisis Management Exercise – Positioning Cyber Resilience at the Highest Level by French National Cyber Security Agency (ANSSI) – CCA France
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
ILLUMINATING DARKSIDE – TTPs, Tools, and the Trend Towards Defense Evasion by PICUS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
OPEN SOURCE SOC TOOLS BY BONI YEAMIN
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Definitive Guide to SOC as a Service – The Essential Elements of Advanced Threat Detection and Response by Crystal Bedell and Mark Bouchard – ARCTIC WOLF
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Pentesting Active Directory Environments by VARONIS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CYBERSECURITY – BLUE TEAM TOOLKIT – A practical cybersecurity handbook for both tech and non-tech professionals by Nadean Tanner
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
2022 PRIVACY TECH VENDOR REPORT by IAPP
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
13 Questions for boards to ask about cyber security by Australian Cyber Security Centre – ACSC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Arms Watch An Analysis of Stated & Perceived Offensive Cyber Capabilities by The Hague Centre for Strategic Studies
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
DISTRIBUTED DENIAL OF SERVICE (DDOS) ATTACKS – Classification, Attacks, Challenges and Countermeasures – CRC Press Book
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Telecom Cybersecurity – 5G Protection Use Cases by SecurityGen
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
THE 2022 HORNETSECURITY RANSOMWARE ATTACKS ANALYSIS
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
11 STRATEGIES OF A WORLD-CLASS CYBERSECURITY OPERATIONS CENTERS HIGHLIGHTS BY MITRE
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cyber Security Toolkit for Boards – Helping board members to get to grips with cyber security by NCSC
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Security Protocols – SSL vs TLS – ALL YOU NEED TO KNOW.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
#EKOPARTY2022 – Ekoparty is a technical security conference born in 2001. +3000 guests, single track, workshops, trainings + ❤ – World-class experts, new breakthroughs, and professional training taught by the most recognized infosec professionals.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO2CISO Toolbox Series – Cyber Security Blogs / Cyber Security RSS Feeds List –
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
BASELINE CYBER SECURITY CONTROLS FOR SMALL AND MEDIUM ORGANIZATIONS V1.2 by Canadian Centre for CYBERSECURITY
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...