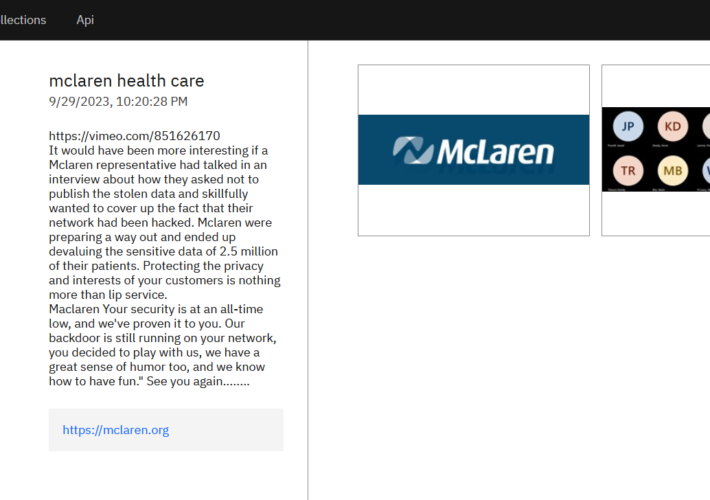
Source: securityaffairs.com – Author: Pierluigi Paganini BlackCat gang claims they stole data of 2.5 million patients of McLaren Health Care The ALPHV/BlackCat ransomware gang added McLaren...
Day: October 1, 2023
Security Affairs newsletter Round 439 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Meet LostTrust ransomware — A likely rebrand of the MetaEncryptor gang – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The LostTrust ransomware operation is believed to be a rebrand of MetaEncryptor, utilizing almost identical data leak sites and encryptors....
New Marvin attack revives 25-year-old decryption flaw in RSA – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A flaw related to the PKCS #1 v1.5 padding in SSL servers discovered in 1998 and believed to have been...
Cloudflare DDoS protections ironically bypassed using Cloudflare – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cloudflare’s Firewall and DDoS prevention can be bypassed through a specific attack process that leverages logic flaws in cross-tenant security...
Microsoft fixes Outlook prompts to reopen closed windows – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has resolved a known issue that caused Outlook Desktop to unexpectedly prompt users to reopen previously closed windows. “This...
A Closer Look at the Snatch Data Ransom Group – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and...
Hackers Impersonate Meta Recruiter to Target Aerospace Firm – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Lazarus Deploys New Backdoor to Target Aerospace Firm Vasudevan...
Avoid libwebp Electron Woes On macOS With positron – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr If you’ve got on this blog (directly, or via syndication) you’d have to have been living under a rock to not...
A Closer Look at the Snatch Data Ransom Group – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs Earlier this week, KrebsOnSecurity revealed that the darknet website for the Snatch ransomware group was leaking data about its users and...
Discover Endpoint VPN in 2023: Unlocking Secure Remote Access – Source: securityboulevard.com
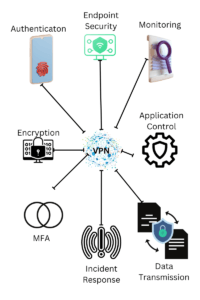
Source: securityboulevard.com – Author: Michael Toback Introduction In today’s interconnected world, the need for secure remote access to networks and data has never been more crucial....
DEF CON 31 – Lorenzo Cococcia ‘s ‘War Stories – Finding Foes And Yourself With Latency Trilateration’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/def-con-31-lorenzo-cococcia-s-war-stories-finding-foes-and-yourself-with-latency-trilateration/ Category & Tags: Security Bloggers Network,Cybersecurity,cybersecurity education,DEF...
2023 OWASP Top-10 Series: API10:2023 Unsafe Consumption of APIs – Source: securityboulevard.com
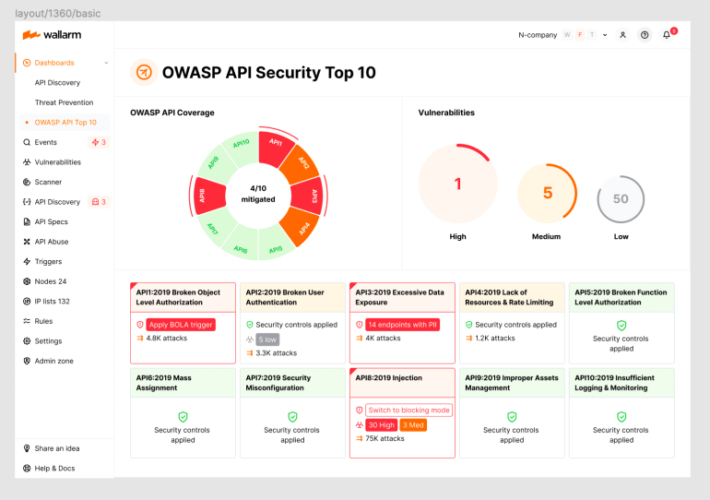
Source: securityboulevard.com – Author: wlrmblog Welcome to the 11th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...
ITU – Mortal Fatality! – Latin America bombed in the Global Cybersecurity Index
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Good practices for security OIT by enisa
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Applying Cyber Kill Chain® Methodology to Network Defense by Lockheed Martin
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
90 DAYS A CISO´s Journey to Impact define your role !!
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
100 Security Operation Tools for SOCs by Joas Antonio
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The Red Team Guide by Peerlyst – A practical guide for Red Teams and Offensive Security
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Verizon 2022 DBIR Data Breach Investigations Report
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
IBM Security – Cost of a Data Breach Report 2021
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Cybersecurity CISOs priorities in 2021: focus and return to the basics
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
RSA Conference 2022 Compendium: 150+ Interviews and More by SMG
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
GIR – The Guide to Cyber Investigations.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
cisomag – Hardening Cyber Insurance Market Makes Cybersecurity More than a Tech Problem
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
CISO2CISO VIDEO SERIES – ¿What is Your Password ?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
How Can We Structure Cybersecurity Teams To Better Integrate Security In Agile At Scale?
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
“CISO Mind Map”, an interesting approach to talk about cyber & CISOs responsibilities in our organizations.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Sleeping with the enemy – A best practice guide for attacker engagement by Nick Klein.
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
The State of API Security Q1 2022 Report from Salt Labs
The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...