Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The governments of the United Kingdom and Kuwait have agreed on a deal whereby the UK will...
Month: September 2023
Another data breach at Forever 21 leaks details of 500,000 current and former employees – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Fashion chain Forever 21 has suffered what it has described as a “data security incident” that saw a hacker gain...
Paramount, Forever 21 Data Breaches Set Stage for Follow-on Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A pair of breaches have hit media giant Paramount Global and fashion purveyor Forever 21,...
Apple iPhone 14 Pro Offered Up to the Hacking Masses – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Apple has designated the iPhone 14 Pro as the target device to be used for research conducted in...
BadBazaar espionage tool targets Android users via trojanized Signal and Telegram apps – Source:
Source: – Author: 1 ESET researchers have discovered active campaigns linked to the China-aligned APT group known as GREF, distributing espionage code that has previously targeted...
Recovering from a supply-chain attack: What are the lessons to learn from the 3CX hack? – Source:
Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 2
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 15
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 15
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 12
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 1
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Weaknesses in Cisco ASA SSL VPNs Exploited Through Brute-Force Attacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In a recent surge of cyber threats, hackers have targeted Cisco Adaptive Security Appliance (ASA) SSL VPNs using a combination...
Heimdal’s MXDR Adapt: World’s First Tailored SOC Service – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Heimdal® unveils MXDR Adapt, a transformative evolution of its Managed Extended Detection and Response (MXDR) solution. This revolutionary adaptive control...
Notorious QakBot Malware Dismantled: $8.6M Seized and 700K Computers Freed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa On Tuesday, the U.S. Department of Justice announced the disruption of an international law enforcement operation that targeted the QakBot...
Own Your Own Government Surveillance Van – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier A used government surveillance van is for sale in Chicago: So how was this van turned into a mobile spying...
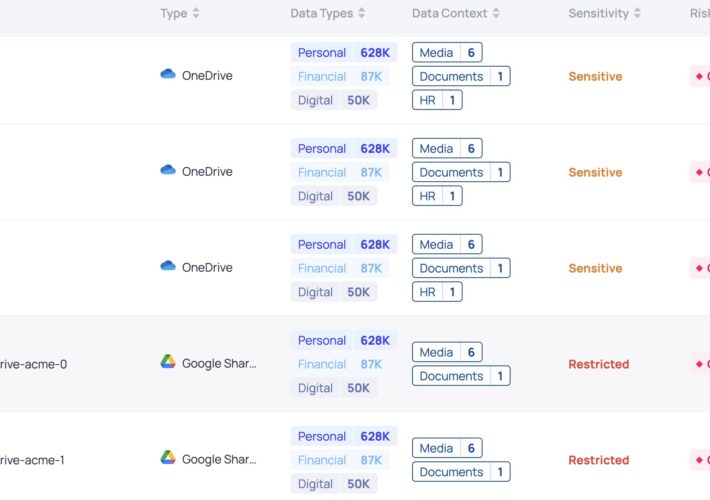
Laminar strengthens cloud data security with Microsoft OneDrive and Google Drive integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dave Stuart New cloud file share integrations mark a pivotal moment for holistic data security posture management in the cloud In today’s...
The Gig Economy: 6 Attack Scenarios to Remember – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers While the primary goal of gig economy platforms is to facilitate connections between users and service providers, threat actors can...
Tips and Tools for Open Source Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: AJ Starita You don’t need us to tell you that open source software is becoming a very significant percentage of commercial software...
APT Group Earth Estries Runs Espionage Campaigns Against US, Others – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A newly discovered cyber-espionage threat group for at least three years has been using advanced and novel tools to steal...
News alert: Voxel AI increases funding to $30M, aims to transform industrial workplace safety – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido San Francisco, Calif., Aug. 30, 2023 — Every year over 340m workers suffer a workplace injury: slips and falls, strains and...
BSides Cheltenham 2023 – Gert-Jan Bruggink – Reimagining The Intelligence Deliverables Using Structured Threat Content – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsides-cheltenham-2023-gert-jan-bruggink-reimagining-the-intelligence-deliverables-using-structured-threat-content/ Category & Tags: CISO Suite,Governance, Risk &...
SANS 2023 DevSecOps Survey – Source: securityboulevard.com
Source: securityboulevard.com – Author: Synopsys Editorial Team Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/sans-2023-devsecops-survey/ Category & Tags: DevOps,Security Bloggers Network,DevSecOps,Security...