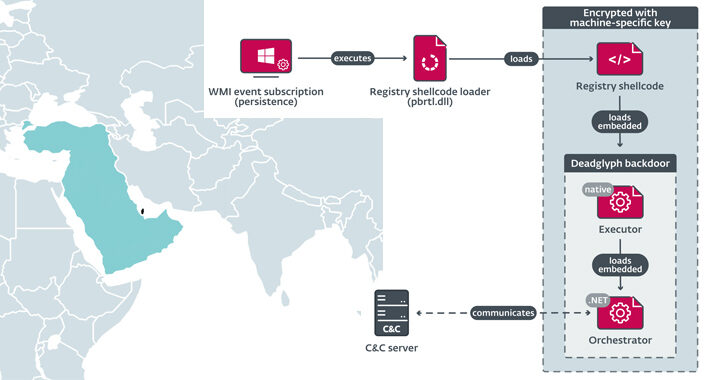
Source: thehackernews.com – Author: . Cybersecurity researchers have discovered a previously undocumented advanced backdoor dubbed Deadglyph employed by a threat actor known as Stealth Falcon as...
Day: September 23, 2023
Apple Fixes Bugs That Infected Egyptian Politician’s iPhone – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Endpoint Security , Next-Generation Technologies & Secure Development , Threat Intelligence Cytrox’s Predator Found on Device of Ahmed Eltantawy Mihir Bagwe...
Cato Networks Raises $238M on $3B Valuation to Move Upmarket – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Access Security Brokers (CASB) , Data Loss Prevention (DLP) , Endpoint Security Equity Investment Will Allow Cato Networks to Tightly...
Cloud Smart Roadshow Bellevue (Seattle): Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Data Security & Resilience , Cloud Security , DevSecOps Presented by VMware 300 Minutes Learn how...
Cloud Smart Roadshow Costa Mesa (Irvine): Practical Strategies for a Simplified and Secured Cloud Journey – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Data Security & Resilience , Cloud Security , DevSecOps Presented by VMware 300 Minutes Learn how...
Chinese, North Korean Nation-State Groups Target Health Data – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Healthcare HHS Report Lists APT41, APT43 and Lazarus Among Top Threat...
Google CISO Phil Venables on Building Strong CIO-CISO Bonds – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Leadership & Executive Communication , Training & Security Leadership , Video CIO, CISO Must Join Forces to Upgrade Organization to More...
Evasive Gelsemium hackers spotted in attack against Asian govt – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A stealthy advanced persistent threat (APT) tracked as Gelsemium was observed in attacks targeting a Southeast Asian government that spanned...
National Student Clearinghouse data breach impacts 890 schools – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan U.S. educational nonprofit National Student Clearinghouse has disclosed a data breach affecting 890 schools using its services across the United...
Air Canada discloses data breach of employee and ‘certain records’ – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Image Credit: John McArthur (Unsplash) Air Canada, the flag carrier and the largest airline of Canada, disclosed a cyber security incident...
MGM, Caesars Cyberattack Responses Required Brutal Choices – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Twin cyberattacks on MGM Resorts and Caesars Entertainment have provided a singular view into what happens when...
Bot Swarm: Attacks From Middle East & Africa Are Notably Up – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading The number of reported bot attacks originating from the Middle East and Africa increased over the...
Guardians of the Cyberverse: Building a Resilient Security Culture – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dr. Sean Costigan, Director of Cyber Policy, Red Sift Amid relentless cyberattacks and mounting regulatory pressures, security culture has been thrust into...
Do CISOs Have to Report Security Flaws to the SEC? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Evan Schuman, Contributing Writer, Dark Reading Now that the SEC wants to know about any material security incidents within four days of...
Mastering Defense-in-Depth and Data Security in the Cloud Era – Source: www.darkreading.com
Source: www.darkreading.com – Author: Liat Hayun, Co-Founder & CEO, Eureka Security Defense-in-depth is not a new concept in cybersecurity. Borrowed from military terminology, it was created...
BBTok Banking Trojan Impersonates 40+ Banks to Hijack Victim Accounts – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Threat actors are targeting hundreds of banking customers in Latin America with a new variant of an...
Hikvision Intercoms Allow Snooping on Neighbors – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading A concerning Internet of Things cyberattack vector has been uncovered — one that can turn the neighboring...
Understanding the Differences Between On-Premises and Cloud Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Oliver Tavakoli, Chief Technology Officer, Vectra AI The difference between managing cybersecurity in on-premises and cloud environments is not unlike playing traditional...
Friday Squid Blogging: New Squid Species – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier An ancient squid: New research on fossils has revealed that a vampire-like ancient squid haunted Earth’s oceans 165 million years...
Security Service Edge (SSE): Defined, explained, explored – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau With more than 15 years of experience in cyber security, Manuel Rodriguez is currently the Security Engineering Manager for the North...
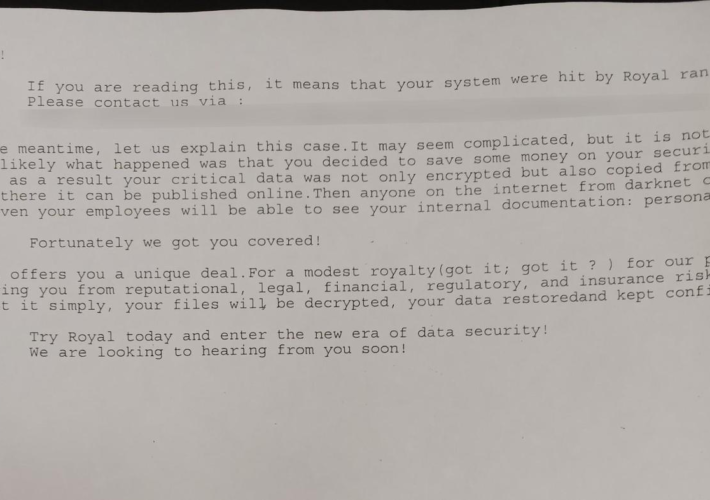
City of Dallas has set a budget of $8.5 million to mitigate the May Royal ransomware attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini City of Dallas has set a budget of $8.5 million to mitigate the May Royal ransomware attack Pierluigi Paganini September...
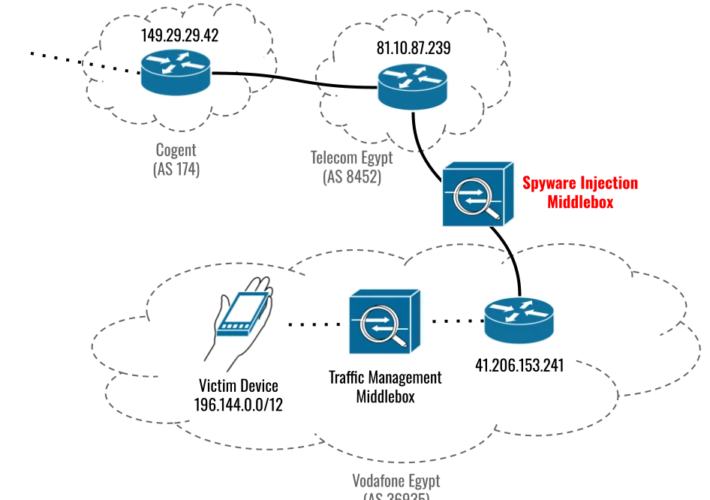
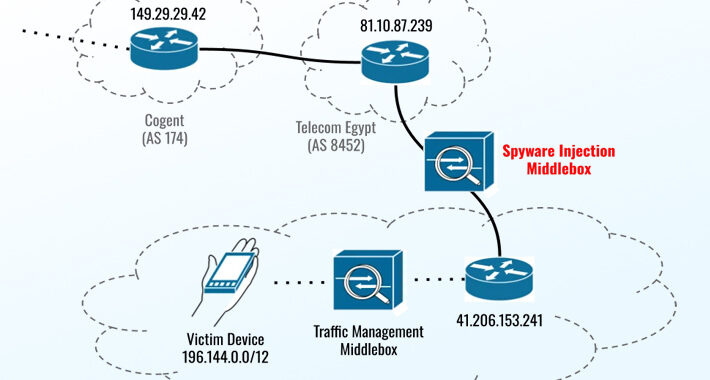
Recently patched Apple and Chrome zero-days exploited to infect devices in Egypt with Predator spyware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Recently patched Apple and Chrome zero-days exploited to infect devices in Egypt with Predator spyware Pierluigi Paganini September 22, 2023...
CISA adds Trend Micro Apex One and Worry-Free Business Security flaw to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds Trend Micro Apex One and Worry-Free Business Security flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini September...
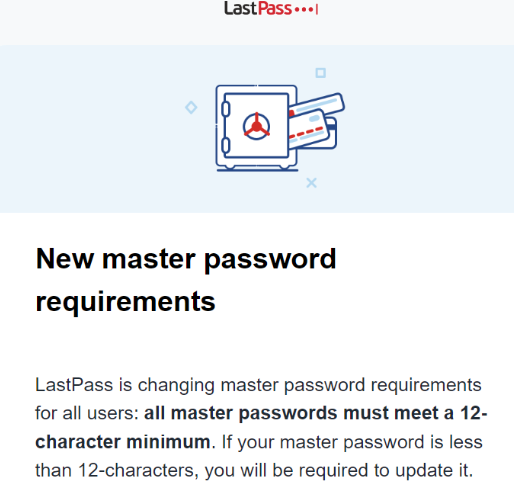
LastPass: ‘Horse Gone Barn Bolted’ is Strong Password – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The password manager service LastPass is now forcing some of its users to pick longer master passwords. LastPass says the changes...
Weekly Update 366 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Well that’s it, Europe is done! I’ve spent the week in Prague with highlights including catching up with Josef Prusa,...
New Apple Zero-Days Exploited to Target Egyptian ex-MP with Predator Spyware – Source:thehackernews.com
Source: thehackernews.com – Author: . The three zero-day flaws addressed by Apple on September 21, 2023, were leveraged as part of an iPhone exploit chain in...
LastPass: ‘Horse Gone Barn Bolted’ is Strong Password – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs The password manager service LastPass is now forcing some of its users to pick longer master passwords. LastPass says the changes...
The Threat Landscape for Healthcare Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland The threat landscape for healthcare organizations has shifted tremendously since the outset of COVID-19. The means, opportunities, and motives for...
Cyber Week 2023 & The Israel National Cyber Directorate Presents – Guarding the Cyber Galaxy: Electronic-Cyber Defense in Space – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/cyber-week-2023-the-israel-national-cyber-directorate-presents-guarding-the-cyber-galaxy-electronic-cyber-defense-in-space/ Category & Tags: CISO Suite,Governance, Risk &...
Cybersecurity Insights with Contrast CISO David Lindner | 9/22 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Insight #1 There will always be a balance in the psychological acceptability of any security controls put...