Source: www.darkreading.com – Author: Tracy Z. Maleeff, Principal, Sherpa Intelligence LLC Depending on your perspective, Africa is either a global asset or a liability in the...
Day: September 20, 2023
What a mess! Clorox warns of “material impact” to its financial results following cyberattack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Clorox, the household cleaning product manufacturer, has admitted that its financial results for the first quarter could see a “material...
The Expel Quarterly Threat Report distills the threats and trends the Expel SOC saw in Q2. Download it now. – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Graham Cluley Security News is sponsored this week by the folks at Expel. Thanks to the great team there for...
Yikes! My sex video has been uploaded to YouPorn, apparently – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley I’ve received an email. It’s from YouPorn, and they say it’s urgent. This should be interesting. Let’s see what it...
Fake WinRAR proof-of-concept exploit drops VenomRAT malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A hacker is spreading a fake proof-of-concept (PoC) exploit for a recently fixed WinRAR vulnerability on GitHub, attempting to infect...
Expensive Investigations Drive Surging Data Breach Costs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Outpost24 The dreaded data breach is an outcome feared by companies of all sizes in today’s threat landscape, largely due...
Signal adds quantum-resistant encryption to its E2EE messaging protocol – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Signal has announced that it upgraded its end-to-end communication protocol to use quantum-resistant encryption keys to protect users from future...
Claimants in Celsius crypto bankruptcy targeted in phishing attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Scammers are impersonating the bankruptcy claim agent for crypto lender Celsius in phishing attacks that attempt to steal funds from...
Trend Micro fixes endpoint protection zero-day used in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Trend Micro fixed a remote code execution zero-day vulnerability in the Trend Micro’s Apex One endpoint protection solution that was actively exploited...
Securing the oil and gas sector: Strategic insights from an industry expert – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau With 25 years’ experience in Information Technology, Rishi has been part of many transformational initiatives. Recently, he deployed one of Canada’s...
International Criminal Court Reveals Security Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The International Criminal Court (ICC) yesterday confirmed the discovery of suspicious activity inside its IT network but revealed little else of a...
Finnish Authorities Shutter Dark Web Drugs Marketplace – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Investigators in Finland have seized and shut down a web server used to operate a local dark web marketplace. Piilopuoti opened...
Brits Lose $9.3bn to Scams in a Year – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Around 10% of British adults have lost money to fraudsters over the past year, amounting to estimated losses of £7.5bn ($9.3bn),...
International Criminal Court hit with a cyber attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini International Criminal Court hit with a cyber attack Pierluigi Paganini September 20, 2023 A cyberattack hit the International Criminal Court...
GitLab addressed critical vulnerability CVE-2023-5009 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini GitLab addressed critical vulnerability CVE-2023-5009 Pierluigi Paganini September 20, 2023 GitLab rolled out security patches to address a critical vulnerability,...
Trend Micro addresses actively exploited zero-day in Apex One and other security Products – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Trend Micro addresses actively exploited zero-day in Apex One and other security Products Pierluigi Paganini September 20, 2023 Trend Micro...
ShroudedSnooper threat actors target telecom companies in the Middle East – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini ShroudedSnooper threat actors target telecom companies in the Middle East Pierluigi Paganini September 19, 2023 ShroudedSnooper threat actors are targeting...
Recent cyber attack is causing Clorox products shortage – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Recent cyber attack is causing Clorox products shortage Pierluigi Paganini September 19, 2023 The cyber attack that hit the cleaning...
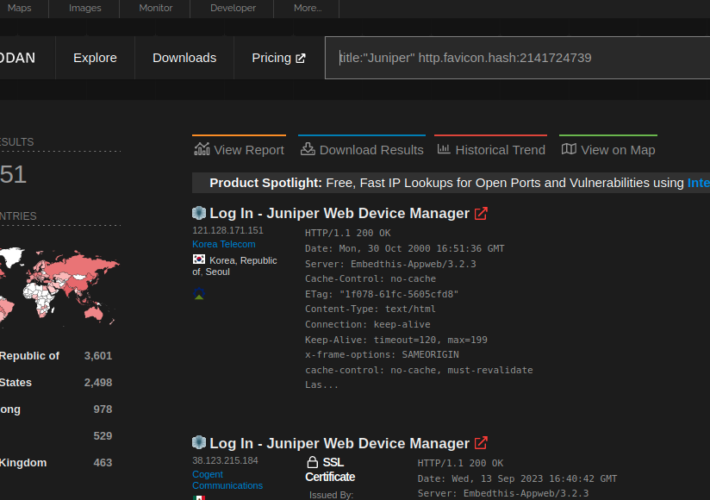
12,000 Juniper SRX firewalls and EX switches vulnerable to CVE-2023-36845 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini 12,000 Juniper SRX firewalls and EX switches vulnerable to CVE-2023-36845 Pierluigi Paganini September 19, 2023 Researchers discovered approximately 12,000 Juniper...
Signal Messenger Introduces PQXDH Quantum-Resistant Encryption – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 20, 2023THNEncryption / Privacy Encrypted messaging app Signal has announced an update to the Signal Protocol to add support for...
GitLab Releases Urgent Security Patches for Critical Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 20, 2023THNVulnerability / Software Security GitLab has shipped security patches to resolve a critical flaw that allows an attacker to...
Trend Micro Releases Urgent Fix for Actively Exploited Critical Security Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 20, 2023THNZero Day / Vulnerability Cybersecurity company Trend Micro has released patches and hotfixes to address a critical security flaw...
Detecting AI-Generated Text – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier There are no reliable ways to distinguish text written by a human from text written by an large language model....
Improper Usage of SAS Token Leads to Massive Microsoft Data Leakage – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Microsoft researchers leaked 38TB of sensitive data to a public GitHub repository while training open-source AI learning models. The Microsoft...
How to Create and Use a Docker Secret From a File – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen TechRepublic Premium TechRepublic Premium Troubleshooting Backup Routines Backup routines are the lifeblood of information technology. Protecting an organization’s data is...
How to Create and Use a Docker Secret From a File (+Video) – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen on September 19, 2023, 9:57 AM EDT How to Create and Use a Docker Secret From a File (+Video) In...
macOS Tune-Up Checklist – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Macs, like Windows computers, benefit from routine maintenance. Regular tune-ups help protect Macs, both desktop and laptop models, from potential data loss,...
Apptega Lands 39 Badges, including GRC Momentum Leader, in Fall G2 Reports – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalie Anderson Apptega, the end-to-end GRC platform for forward-thinking IT and managed service providers, earned 39 high-performer and momentum leader badges in G2’s...
LockBit Affiliates Use RMM Software in Ransomware Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Affiliates of the Russia-linked LockBit ransomware group are using remote monitoring and management (RMM) software to distribute its malicious payload...
Black Hat: Stephen Chin, JFrog – Source: securityboulevard.com
Source: securityboulevard.com – Author: Alan Shimel Speaker 1: This is Techstrong TV. Alan Shimel: Hey everyone. We’re back here live in our Mandalay Bay suite at...