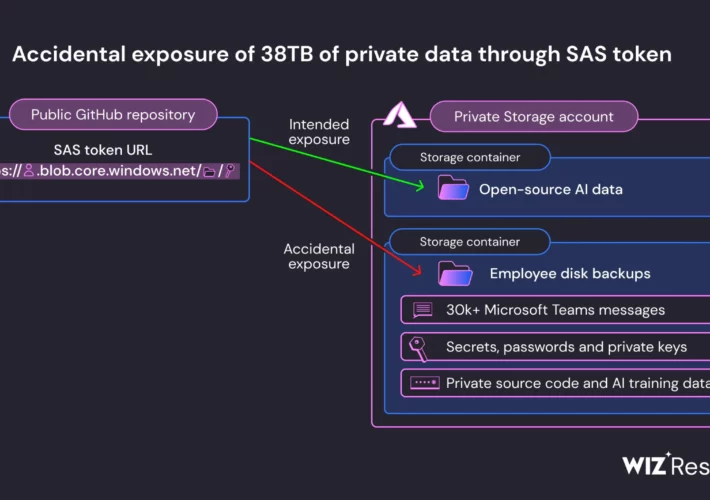
Source: www.securityweek.com – Author: Ryan Naraine Researchers at Wiz have flagged another major security misstep at Microsoft that caused the exposure of 38 terabytes of private...
Day: September 18, 2023
Google Extends Chromebook Lifespan, Promises 10 Years of Automatic Updates – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Google has announced that it is committed to provide regular automatic updates, with security patches, for all recent Chromebook iterations...
OT/IoT and OpenTitan, an Open Source Silicon Root of Trust – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend OpenTitan is a project aimed at bringing the success of open source software to the silicon design space – specifically...
Canadian Government Targeted With DDoS Attacks by Pro-Russia Group – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The pro-Russian cybercrime group named NoName057(16) has been observed launching distributed denial-of-service (DDoS) attacks against Canadian organizations, a fresh government...
Fortinet Patches High-Severity Vulnerabilities in FortiOS, FortiProxy, FortiWeb Products – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Fortinet has released patches for a high-severity cross-site scripting (XSS) vulnerability impacting multiple FortiOS and FortiProxy versions. Tracked as CVE-2023-29183...
Two Vegas Casinos Fell Victim to Cyberattacks, Shattering the Image of Impenetrable Casino Security – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A persistent error message greeted Dulce Martinez on Monday as she tried to access her casino rewards account to book...
CISA Releases New Identity and Access Management Guidance – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Cybersecurity and Infrastructure Security Agency (CISA) has released new guidance on how federal agencies can integrate identity and...
TikTok Is Hit With $368 Million Fine Under Europe’s Strict Data Privacy Rules – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press European regulators slapped TikTok with a $368 million fine on Friday for failing to protect children’s privacy, the first time...
ICS Security Firm Dragos Raises $74 Million in Series D Extension – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Dragos, a company that specializes in protecting industrial control systems (ICS) and other operational technology (OT) against cyber threats, on...
Imagine Making Shadowy Data Brokers Erase Your Personal Info. Californians May Soon Live the Dream – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press You may not know it, but thousands of often shadowy companies routinely traffic in personal data you probably never agreed...
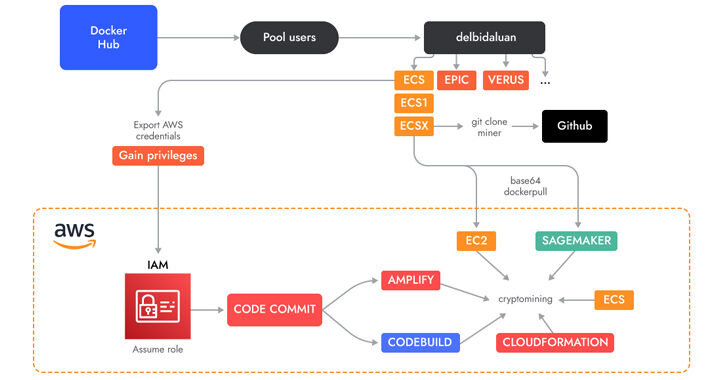
New AMBERSQUID Cryptojacking Operation Targets Uncommon AWS Services – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 18, 2023THNCloud Security / Cryptocurrecy A novel cloud-native cryptojacking operation has set its eyes on uncommon Amazon Web Services (AWS)...
Think Your MFA and PAM Solutions Protect You? Think Again – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 18, 2023The Hacker NewsIdentity Threat / Attack Surface When you roll out a security product, you assume it will fulfill...
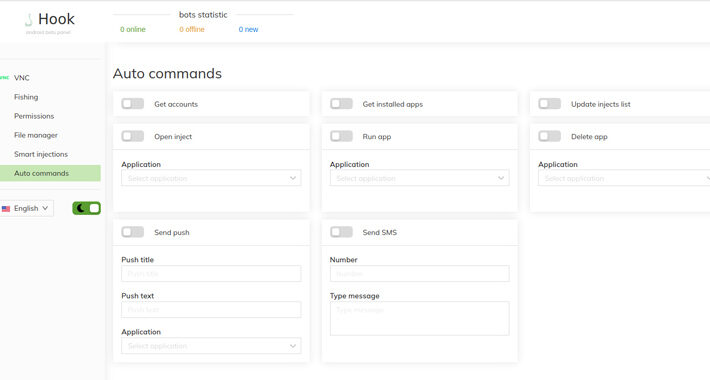
Hook: New Android Banking Trojan That Expands on ERMAC’s Legacy – Source:thehackernews.com
Source: thehackernews.com – Author: . A new analysis of the Android banking trojan known as Hook has revealed that it’s based on its predecessor called ERMAC....
Fraudsters Steal Over $1m in Three Weeks Through ‘Pig Butchering’ Crypto Scam – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Malicious actors have stolen more than $1m in a ‘pig butchering’ cryptocurrency scam in just three months, researchers from Sophos have...
Weekly Update 365 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt It’s another week of travels, this time from our “second home”, Oslo. That’s off the back of 4 days in...
Cryptocurrency Scams to Heavily Target TikTok Users – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Cybercriminals heavily target TikTok users with cryptocurrency giveaway scams. The vast majority of the posts impersonate Elon Musk and relate...
EDR for Banking: 6 Ways EDR Can Help Financial Organizations – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac There are financial advantages to investing in cybersecurity, especially in Endpoint Detection and Response (EDR) solutions. Breaching one financial institution...
AI in Software Development: The Good, the Bad, and the Dangerous – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Artificial intelligence (AI) is good for a lot more than writing term papers, songs, and poems. In the tech world, its...
Evaluating New Partners and Vendors From an Identity Security Perspective – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Effective identity management is crucial to enterprise security, enablement, and — ultimately — success. But despite its importance, business leaders outside...
Retool Falls Victim to SMS-Based Phishing Attack Affecting 27 Cloud Clients – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 18, 2023THNCyber Attack / Data Breach Software development company Retool has disclosed that the accounts of 27 of its cloud...
Financially Motivated UNC3944 Threat Actor Shifts Focus to Ransomware Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 18, 2023THNThreat Intelligence / Ransomware The financially motivated threat actor known as UNC3944 is pivoting to ransomware deployment as part...
Another $40m Dispersed to Western Union Fraud Victims – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A further multimillion-dollar distribution of funds from Western Union to victims of fraud perpetrated via its payment network has begun, following...
Illegal Betting Ring Used Satellite Tech to Get Scoop on Results – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Police are celebrating after busting a suspected illegal betting and match-fixing ring which used advanced technology to find out the results...
TikTok Fined $368m For Child Data Privacy Offenses – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 TikTok has been fined hundreds of millions of dollars after Ireland’s data protection regulator found it infringed the GDPR with regards...
FBI hacker USDoD leaks highly sensitive TransUnion data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini FBI hacker USDoD leaks highly sensitive TransUnion data Pierluigi Paganini September 18, 2023 Researchers from vx-underground reported that FBI hacker...
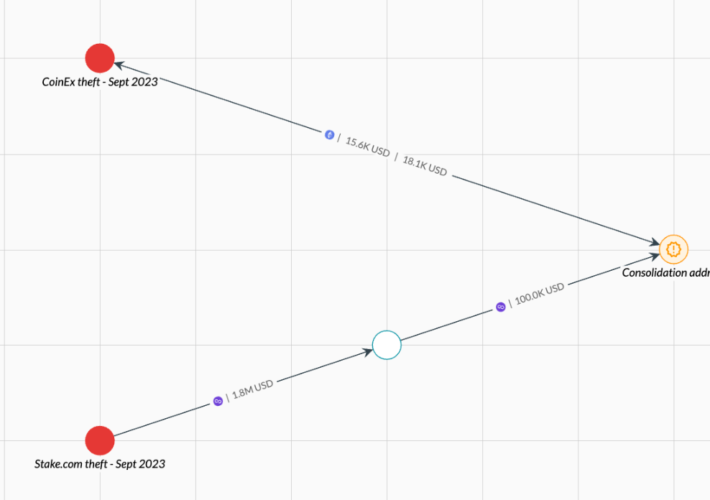
North Korea’s Lazarus APT stole almost $240 million in crypto assets since June – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea’s Lazarus APT stole almost $240 million in crypto assets since June Pierluigi Paganini September 18, 2023 The North...
Clop gang stolen data from major North Carolina hospitals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Clop gang stolen data from major North Carolina hospitals Pierluigi Paganini September 17, 2023 Researchers at healthcare technology firm Nuance blame...
CardX released a data leak notification impacting their customers in Thailand – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CardX released a data leak notification impacting their customers in Thailand Pierluigi Paganini September 17, 2023 One of Thailand’s major...
TikTok flooded by ‘Elon Musk’ cryptocurrency giveaway scams – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams TikTok is flooded by a surge of fake cryptocurrency giveaways posted to the video-sharing platform, with almost all of the...
Understanding the Cyber Kill Chain: A Comprehensive Guide to Cybersecurity – Source: securityboulevard.com
Source: securityboulevard.com – Author: CyB3rBEA$T In today’s interconnected digital world, cyberattacks have become an ever-present threat to individuals, businesses, and governments. To defend against these threats...