Source: www.schneier.com – Author: Bruce Schneier HomeBlog Friday Squid Blogging: Cleaning Squid Two links on how to properly clean squid. I learned a few years ago,...
Day: September 16, 2023
TikTok Faces Massive €345 Million Fine Over Child Data Violations in E.U. – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 16, 2023THNPrivacy / Technology The Irish Data Protection Commission (DPC) slapped TikTok with a €345 million (about $368 million) fine...
The Week in Ransomware – September 15th 2023 – Russian Roulette – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams This week’s big news is the extortion attacks on the Caesars and MGM Las Vegas casino chains, with one having...
6 most common cyber security vulnerabilities you should know in 2023 – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Contributed by George Mack, Content Marketing Manager, Check Point Software. Nearly all security incidents stem from cyber security vulnerabilities. What is...
Dariy Pankov, the NLBrute malware author, pleads guilty – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Dariy Pankov, the NLBrute malware author, pleads guilty Pierluigi Paganini September 15, 2023 The Russian national Dariy Pankov, aka dpxaker,...
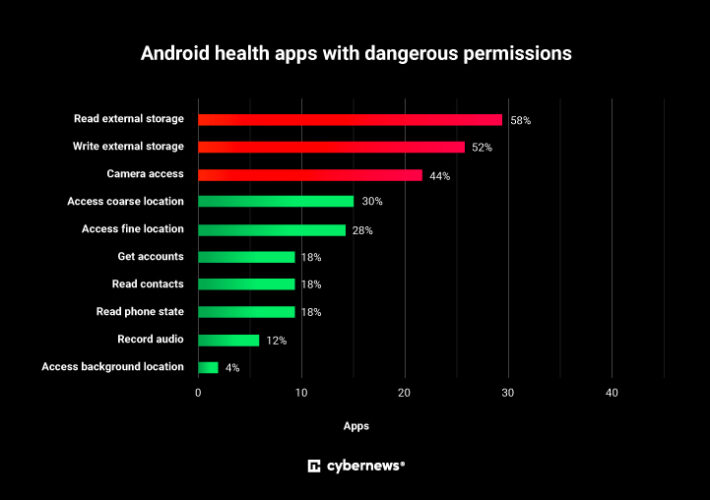
Dangerous permissions detected in top Android health apps – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Dangerous permissions detected in top Android health apps Pierluigi Paganini September 15, 2023 Leading Android health apps expose users to...
Caesars Entertainment paid a ransom to avoid stolen data leaks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Caesars Entertainment paid a ransom to avoid stolen data leaks Pierluigi Paganini September 15, 2023 Caesars Entertainment announced it has...
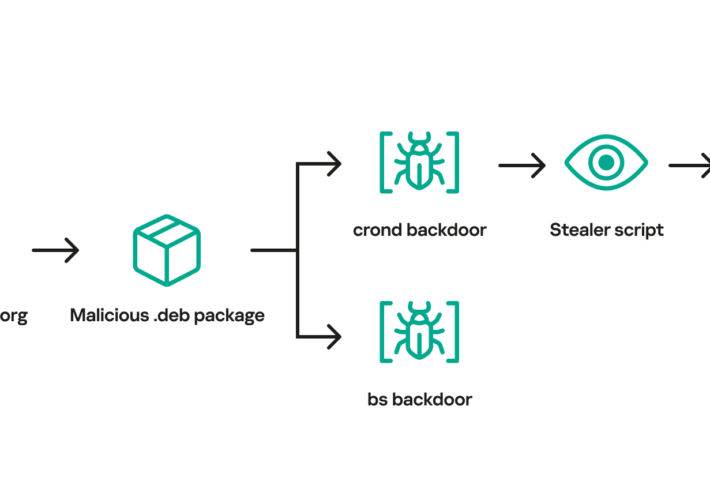
Free Download Manager backdoored to serve Linux malware for more than 3 years – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Free Download Manager backdoored to serve Linux malware for more than 3 years Pierluigi Paganini September 15, 2023 Researchers discovered...
DoD: China’s ICS Cyber Onslaught Aimed at Gaining Kinetic Warfare Advantage – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading China’s onslaught of cyberattacks on critical infrastructure is likely a contingency move designed to gain...
Microsoft Flushes Out ‘Ncurses’ Gremlins – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A widely used programming library called “ncurses” is infested by malicious gremlins — in the form...
Enea Qosmos Threat Detection SDK Launched to Boost the Performance of Network-Based Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Enea, a leading provider of telecom and cybersecurity solutions, today launched the Enea Qosmos Threat Detection SDK. This revolutionary threat detection system...
CISO Global Deepens Capabilities With Integrated Threat Intelligence Feed – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Scottsdale, Ariz. September 13, 2023 – CISO Global (NASDAQ: CISO), an industry leader as a managed cybersecurity and compliance provider, is expanding its capabilities...
Why Shared Fate is a Better Way to Manage Cloud Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Anton Chuvakin, Security Advisor at Office of the CISO, Google Cloud Cloud security breaches happen, and when they do, it’s common for...
Armis Launches Armis Centrix™, the AI-powered Cyber Exposure Management Platform – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 SAN FRANCISCO – September 13, 2023 – Armis, the asset intelligence cybersecurity company, today announced the launch of Armis Centrix™, the AI-powered cyber...
Okta Agent Involved in MGM Resorts Breach, Attackers Claim – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Note: This story has been updated to include comments from Okta chief security officer David Bradbury. The...
Greater Manchester Police Hack Follows Third-Party Supplier Fumble – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kristina Beek, Associate Editor, Dark Reading Thousands of pieces of Greater Manchester Police (GMP) officer data used for ID badge details, such as...
Microsoft: ‘Peach Sandstorm’ Cyberattacks Target Defense, Pharmaceutical Orgs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading A global cyber-espionage campaign conducted by the Iranian nation-state actor known as Peach Sandstorm (aka Holmium)...
NCSC: Why Cyber Extortion Attacks No Longer Require Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading 44CON 2023 – London – Cyber attackers are becoming less reliant on ransomware to get victims...
Two New York Hospitals Breached by the LockBit Ransomware Group – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu The notorious LockBit ransomware group claims to have breached two major hospitals from upstate New York, the Carthage Area Hospital...
What Effect Does Firm Size Have on Ransomware Threats? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Gabriella Antal In an increasingly digital world, the threat of ransomware looms large over organizations of all sizes. However, the impact of...
5 Examples of DNS IoCs That Are Red Flags for Cyberattacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși In the increasingly digitalized world that we live in, doing business without being connected 24/7 is almost unthinkable. Any medium...
ISMG Editors: Are Frequently Used Usernames a Security Risk? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Access Management , Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Also; The ‘Quantum Divide’; Global AI Regulatory...
Enhancing Cloud Security on AWS – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Security Operations Why You Should Consider a Cloud-Native Firewall Service Frederick Harris, Senior Director, Products & Solutions Marketing,...
Critical Considerations for Generative AI Use in Healthcare – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Healthcare , Industry Specific Barbee Mooneyhan of Woebot Health on the Need for Strong AI...
Iranian Hackers Gain Sophistication, Microsoft Warns – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Noisy ‘Peach Sandstorm’ Password Spraying Campaign Is Followed by Stealth Mihir Bagwe...
Live Webinar | Protecting Devices and Software from Next-Generation Cyberthreats – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Device Identification , Endpoint Security , Hardware / Chip-level Security Presented by DigiCert 60 mins IoT devices,...
Live Webinar | Leveraging MITRE’s 2023 ATT&CK Evaluation to Supercharge Your Security Strategy – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Caesars Confirms Ransomware Payoff and Customer Data Breach – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Critical Infrastructure Security , Cybercrime MGM Resorts Continuing to Be Extorted by the Same Alphv/BlackCat Ransomware Group Mathew...
Lessons to Learn From Clop’s MOVEit Supply-Chain Attacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Governance & Risk Management Data Minimization and Encryption Mitigate Fallout, Says FS-ISAC’s Teresa Walsh Mathew J....
LLM Summary of My Book Beyond Fear – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Claude (Anthropic’s LLM) was given this prompt: Please summarize the themes and arguments of Bruce Schneier’s book Beyond Fear. I’m...