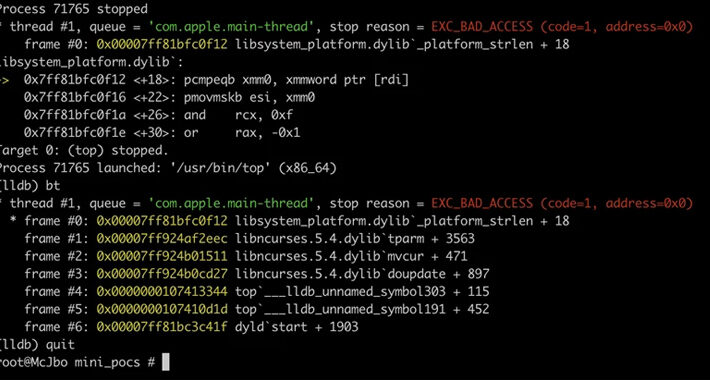
Source: thehackernews.com – Author: . Sep 14, 2023THNEndpoint Security / Vulnerability A set of memory corruption flaws have been discovered in the ncurses (short for new...
Day: September 14, 2023
Free Download Manager Site Compromised to Distribute Linux Malware to Users for 3+ Years – Source:thehackernews.com
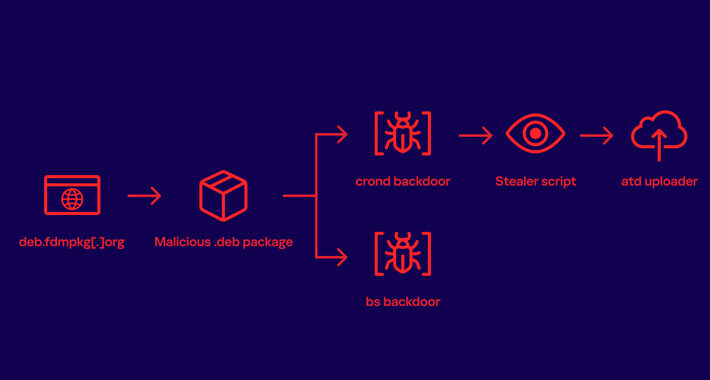
Source: thehackernews.com – Author: . Sep 14, 2023THNSupply Chain / Malware A download manager site served Linux users malware that stealthily stole passwords and other sensitive...
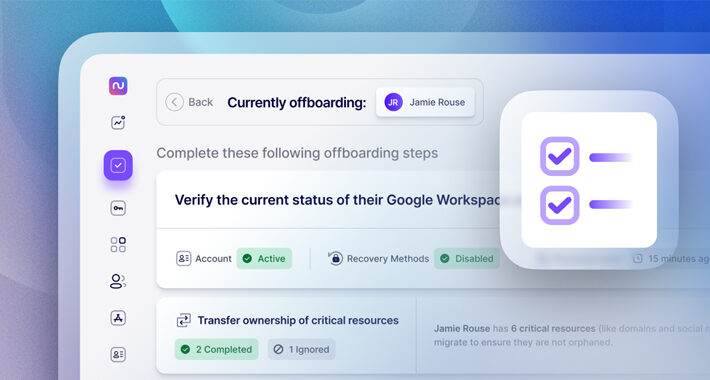
Avoid These 5 IT Offboarding Pitfalls – Source:thehackernews.com
Source: thehackernews.com – Author: . Employee offboarding is no one’s favorite task, yet it is a critical IT process that needs to be executed diligently and...
Stealer Thugs Behind RedLine & Vidar Pivot to Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Two cybercriminal groups well-established in the business of spreading infostealers are diversifying their capabilities, abusing code-signing certificates...
How to Transform Security Awareness Into Security Culture – Source: www.darkreading.com
Source: www.darkreading.com – Author: Perry Carpenter, Chief Evangelist and Strategy Officer, KnowBe4 Time and again, whenever a company is breached, people say: “They were phished. Did...
Mideast Retailers Dogged by Scam Facebook Pages Offering ‘Investment’ Opportunities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Facebook scammers have been targeting users in the Middle East with ads that include purported “investment opportunities”...
Cybersecurity and Compliance in the Age of AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Katherine Schmidt, Geopolitics of Technology Associate, Institute for Security and Technology Flip the script on the traditional hacking scene in a movie:...
Professional Sports: The Next Frontier of Cybersecurity? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Professional sports has a cybersecurity problem. Last year, the National Cyber Security Centre found that 70% of sports organizations experience at...
‘Scattered Spider’ Behind MGM Cyberattack, Targets Casinos – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading A threat group called “Scattered Spider” is reportedly behind the Sept. 10 MGM Resorts cyberattack, which days...
Upcoming Speaking Engagements – Source: www.schneier.com
Source: www.schneier.com – Author: Schneier.com Webmaster About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Fake Signal and Telegram Apps in the Google Play Store – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Google removed fake Signal and Telegram apps from its Play store. An app with the name Signal Plus Messenger was...
Conversational AI Company Uniphore Leverages Red Box Acquisition for New Data Collection Tool – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Red Box provides the open architecture for data capture. Uniphore then feeds that data into U-Capture, its conversational AI automation...
P2P File Sharing Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: The purpose of this policy from TechRepublic Premium is to provide guidelines for the proper use of peer-to-peer file sharing. It includes...
Access Management Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Without appropriate access management controls, businesses are at significant risk from the loss or theft of both physical and digital assets. Access...
Banking Cybersecurity: The Risks Faced by Financial Institutions – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac A data breach in the financial sector is one of the most impactful events in the cybersecurity landscape. That is...
How to Use DNS IoCs to Prevent Ransomware Attacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși As malware and attack techniques continue to evolve in sophistication, DNS IoCs help threat hunting teams to prevent ransomware attacks....
N-Able’s Take Control Agent Vulnerability Exposes Windows Systems to Privilege Escalation – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 14, 2023THNVulnerability / Hacking A high-severity security flaw has been disclosed in N-Able’s Take Control Agent that could be exploited...
Russian Journalist’s iPhone Compromised by NSO Group’s Zero-Click Spyware – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 14, 2023THNSpyware / Malware The iPhone belonging to Galina Timchenko, a prominent Russian journalist and critic of the government, was...
Cloud security monitoring: Benefits, best practices and more – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: What is cloud security monitoring? Cloud security monitoring refers to the practice of overseeing both virtual and physical servers...
Black Hat Fireside Chat: The impactful role crowdsourced security intelligence must play – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido From Kickstarter to Wikipedia, crowdsourcing has become a part of everyday life. Sharing intel for a greater...
Rollbar discloses data breach after hackers stole access tokens – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Software bug-tracking company Rollbar disclosed a data breach after unknown attackers hacked its systems in early August and gained access...
New Windows 11 feature blocks NTLM-based attacks over SMB – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft added a new security feature to Windows 11 that lets admins block NTLM over SMB to prevent pass-the-hash, NTLM...
France demands Apple pull iPhone 12 due to high RF radiation levels – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Agence Nationale des Fréquences (ANFR) has asked Apple to withdraw iPhone 12 smartphones from the French market because the...
Microsoft Teams down: Ongoing outage behind message failures, delays – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is investigating an ongoing outage preventing customers from sending or receiving messages using the company’s Microsoft Teams communication platform....
Hackers steal $53 million worth of cryptocurrency from CoinEx – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Global cryptocurrency exchange CoinEX announced that someone hacked its hot wallets and stole large amounts of digital assets that were used...
How end-user phishing training works (and why it doesn’t) – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Specops Software It always takes two for a phishing attack to work – an attacker to send the bait and...
Smashing Security podcast #339: Bitcoin boo-boo, deepfakes for good, and time to say goodbye to usernames? – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Deepfakes are being used for good (perhaps), common usernames could pose a security threat, and someone has paid a $500,000...
Hackers use new 3AM ransomware to save failed LockBit attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu A new ransomware strain called 3AM has been uncovered after a threat actor used it in an attack that failed...
DOD Cyber Strategy Aims to Disrupt Hackers, Deepen Ally Work – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Active Defense & Deception , Fraud Management & Cybercrime , Next-Generation Technologies & Secure Development Defense Department Will Conduct Defensive Ops...
Journey to the Cloud: Navigating the Transformation – Part 1 – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cloud Security , Security Operations Nikko Asset Management’s Marcus Rameke Defines the Requirements CyberEdBoard • September 13, 2023 Marcus,...