Source: www.securityweek.com – Author: Ryan Naraine Hospitality and entertainment giant MGM Resorts on Monday said a “cybersecurity issue” forced the shutdown of certain computer systems, including...
Day: September 12, 2023
US Marks 22 Years Since 9/11 Terrorist Attacks – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News On Monday, Americans commemorated the 22nd anniversary of the 9/11 attacks through solemn silences, emotional reflections, and calls to educate...
After Microsoft and X, Hackers Launch DDoS Attack on Telegram – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The hacker group Anonymous Sudan has launched a distributed denial-of-service (DDoS) attack against Telegram in retaliation to the messaging platform’s...
Bookstore Chain Dymocks Discloses Data Breach Possibly Impacting 800k Customers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Bookstore chain Dymocks Booksellers is informing hundreds of thousands of individuals that their personal information might have been stolen in...
Associated Press Stylebook Users Targeted in Phishing Attack Following Data Breach – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Associated Press is informing some AP Stylebook customers that their information has been compromised as a result of a...
FBI Blames North Korean Hackers for $41 Million Stake.com Heist – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The FBI says that the North Korea-linked hacking group Lazarus is responsible for the theft of $41 million in cryptocurrency...
Spies, Hackers, Informants: How China Snoops on the West – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP British authorities have arrested a man who reportedly spied for China at the heart of the government in London, sparking fresh fears over...
A 10-point checklist: Owning your cloud security assessment – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Nearly 90% of businesses have taken a multi-cloud approach, and 97% of IT leaders intend to expand cloud systems....
Vulnerabilities Allow Hackers to Hijack, Disrupt Socomec UPS Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Some uninterruptible power supply (UPS) products made by Socomec are affected by several vulnerabilities that can be exploited to hijack...
News Alert: Traceable AI report exposes true scale of API-related data breaches, top challenges – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Francisco, Calif. —Traceable AI, the industry’s leading API security company, today released its comprehensive research report – the 2023 State of API...
Cuba Ransomware Group Unleashes Undetectable Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers at Kaspersky have unveiled research into the activities of the notorious ransomware group known as Cuba. According to a...
Lazarus Group Targets macOS in Supply Chain Assault – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity firm ESET has detected a significant supply chain attack targeting macOS devices. The Lazarus Group, known for its advanced cyber...
Pentagon Urges Collaboration in Cyber Defense – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 In a discussion at the FedTalks event in Washington last Thursday, Leslie A. Beavers, principal deputy chief information officer at the...
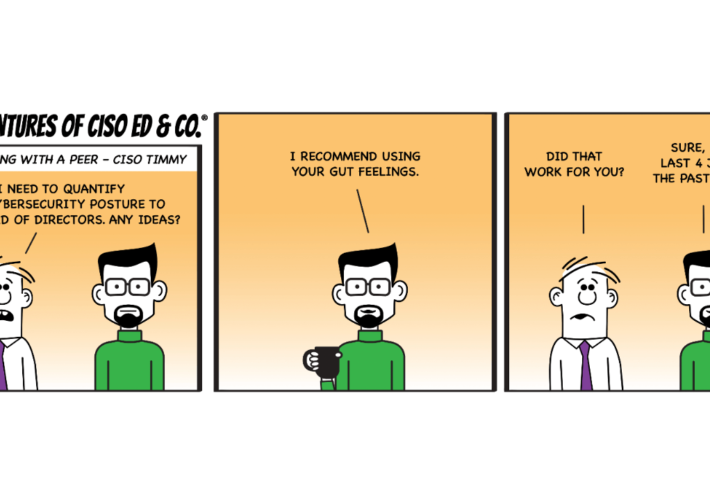
Board Members Struggling to Understand Cyber Risks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Board members frequently struggle to understand cyber risks, putting businesses at higher risk of attacks, a new report from cybersecurity consultancy...
Ransomware Attack Wipes Out Four Months of Sri Lankan Government Data – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Investigations have begun into a massive ransomware attack that has affected Sri Lanka’s government cloud system, Lanka Government Cloud (LGC). The...
IT Systems Encrypted After UK School Hit By Ransomware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A spate of cyber-attacks against UK schools has claimed its latest victim after a Maidstone secondary school suffered a serious security...
AP Stylebook Breach May Have Hit Hundreds of Journalists – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Associated Press (AP) has warned that users of a popular writing style guide have been hit by phishing attacks after...
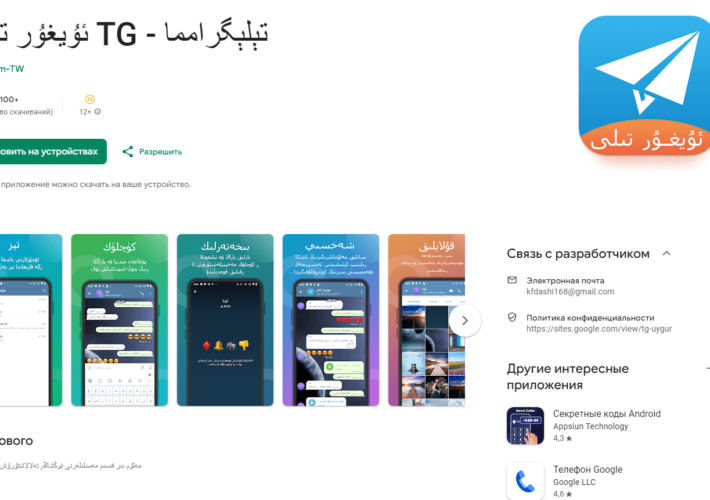
Evil Telegram Mods Removed From Google Play – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have revealed a number of lookalike Telegram apps on the official Play store which were modified to contain spyware....
GOOGLE FIXED THE FOURTH CHROME ZERO-DAY OF 2023 – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini GOOGLE FIXED THE FOURTH CHROME ZERO-DAY OF 2023 Pierluigi Paganini September 11, 2023 Google rolled out emergency security updates to...
CISA adds recently discovered Apple zero-days to Known Exploited Vulnerabilities Catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini CISA adds recently discovered Apple zero-days to Known Exploited Vulnerabilities Catalog Pierluigi Paganini September 11, 2023 U.S. CISA adds vulnerabilities...
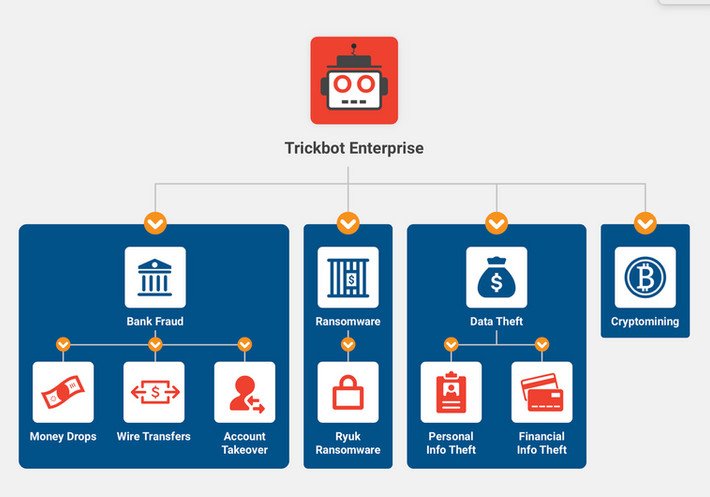
UK and US sanctioned 11 members of the Russia-based TrickBot gang – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini UK and US sanctioned 11 members of the Russia-based TrickBot gang Pierluigi Paganini September 11, 2023 The U.K. and U.S....
New HijackLoader malware is rapidly growing in popularity in the cybercrime community – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini New HijackLoader malware is rapidly growing in popularity in the cybercrime community Pierluigi Paganini September 11, 2023 Zscaler ThreatLabz detailed...
Some of TOP universities wouldn’t pass cybersecurity exam: left websites vulnerable – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Some of TOP universities wouldn’t pass cybersecurity exam: left websites vulnerable Pierluigi Paganini September 11, 2023 CyberNews researchers discovered that...
Evil Telegram campaign: Trojanized Telegram apps found on Google Play – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Evil Telegram campaign: Trojanized Telegram apps found on Google Play Pierluigi Paganini September 11, 2023 Evil Telegram: a Trojanized version...
Building Compliance from Scratch with a Culture of Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalie Anderson For managed service providers (MSPs), building a compliance program from the ground up for an organization is a welcome challenge....
Why Cyber Risk Quantification Needs a Trust Makeover? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Anuj Magazine With this blog, we begin the series dedicated to exploring the nuances of cyber risk quantification. In the fast-evolving world...
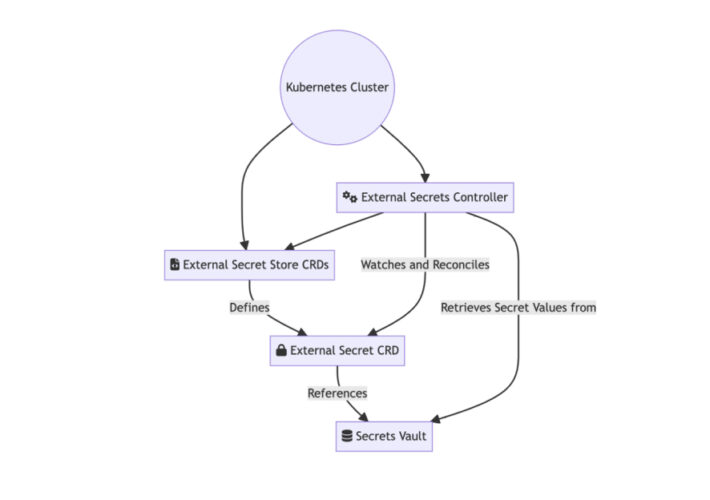
Best Practices of Secrets Management with Kubernetes – Source: securityboulevard.com
Source: securityboulevard.com – Author: Itzik Alvas. Co-founder & CEO, Entro Unlock the potential of your Kubernetes deployments by mastering the best practices for managing secrets, as...
Do you really need to tell FedEx your Social Security number? How to avoid package-delivery scams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog Do you order cartons of strawberries, flat-screen TVs, running shoes, and light bulbs online? You’re far from alone. Oberlo reported...
Designed to Be Breached – Automated Document Consumption – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team By David Neuman, Senior Analyst, TAG Cyber The use of automated document consumption and data extraction processes presents the opportunity...