Source: www.techrepublic.com – Author: Ray Fernandez OneTrust: Fast facts Pricing: OneTrust does not offer transparent pricing details on its website. Those interested can test its 14-day...
Day: September 11, 2023
Vietnamese Hackers Deploy Python-Based Stealer via Facebook Messenger – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 11, 2023THNMalware / Social Media A new phishing attack is leveraging Facebook Messenger to propagate messages with malicious attachments from...
Charming Kitten’s New Backdoor ‘Sponsor’ Targets Brazil, Israel, and U.A.E. – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 11, 2023THNCyber Espionage / Malware The Iranian threat actor known as Charming Kitten has been linked to a new wave...
How to Prevent API Breaches: A Guide to Robust Security – Source:thehackernews.com
Source: thehackernews.com – Author: . With the growing reliance on web applications and digital platforms, the use of application programming interfaces (APIs) has become increasingly popular....
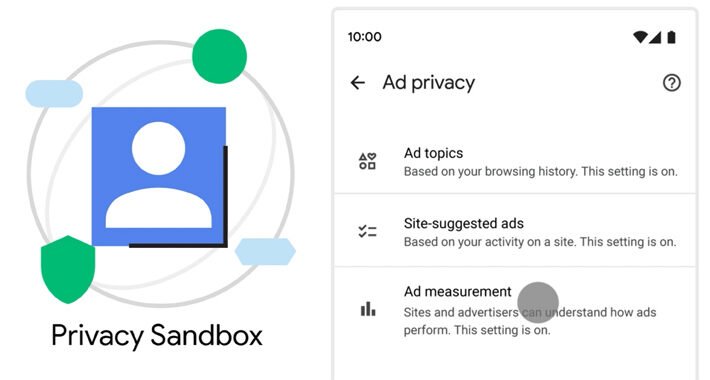
Google Chrome Rolls Out Support for ‘Privacy Sandbox’ to Bid Farewell to Tracking Cookies – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 11, 2023THNPrivacy / Online Security Google has officially begun its rollout of Privacy Sandbox in the Chrome web browser to...
New WiKI-Eve attack can steal numerical passwords over WiFi – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new attack dubbed ‘WiKI-Eve’ can intercept the cleartext transmissions of smartphones connected to modern WiFi routers and deduce individual...
Google fixes another Chrome zero-day bug exploited in attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google released emergency security updates to fix the fourth Chrome zero-day vulnerability exploited in attacks since the start of the...
Microsoft will block 3rd-party printer drivers in Windows Update – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Image: Midjourney Microsoft will block third-party printer driver delivery in Windows Update as part of a substantial and gradual shift...
MGM Resorts shuts down IT systems after cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu MGM Resorts International disclosed today that it is dealing with a cybersecurity issue that impacted some of its systems, including...
CISA warns govt agencies to secure iPhones against spyware attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan The U.S. Cybersecurity and Infrastructure Security Agency (CISA) ordered federal agencies today to patch security vulnerabilities abused as part of...
Iranian hackers backdoor 34 orgs with new Sponsor malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A nation-state threat actor known as ‘Charming Kitten’ (Phosphorus, TA453, APT35/42) has been observed deploying a previously unknown backdoor malware...
Square: Last week’s outage was caused by DNS issue, not a cyberattack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Payment processing firm Square says a widespread outage that took down a large part of the company’s infrastructure last week...
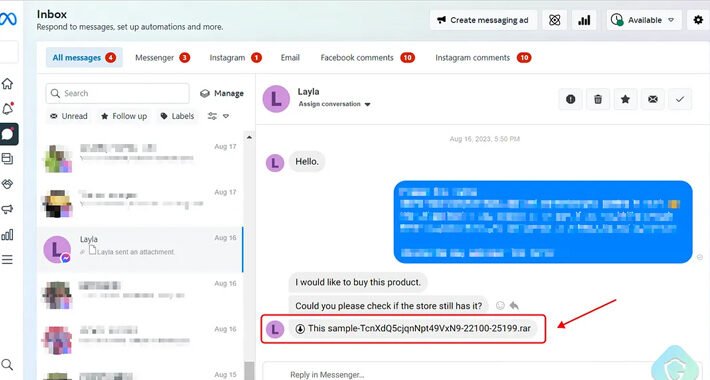
Facebook Messenger phishing wave targets 100K business accounts per week – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers use a massive network of fake and compromised Facebook accounts to send out millions of Messenger phishing messages to...
Iranian APT Hits US Aviation Org via ManageEngine, Fortinet Bugs – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading State-sponsored threat actors have exploited a US aeronautical organization, using known vulnerabilities in Zoho ManageEngine software...
Navigating Rwanda’s New Data Protection Law – Source: www.darkreading.com
Source: www.darkreading.com – Author: Diamaka Aniagolu, Cybersecurity Writer & Content Strategist Data protection and privacy laws can enable legal safety for citizens’ personal information, prevent unauthorized...
Attackers Abuse Google Looker Studio to Evade DMARC, Email Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Cyberthreat actors are abusing Google’s Looker Studio data-visualization tool to deliver phishing-lure pages that ultimately steal both money and...
Overcoming the Rising Threat of Session Hijacking – Source: www.darkreading.com
Source: www.darkreading.com – Author: Trevor Hilligoss, Senior Director of Security Research, SpyCloud From passkeys to multifactor authentication (MFA), most businesses are embracing solutions that protect sensitive information to...
From Caribbean shores to your devices: analyzing Cuba ransomware – Source: securelist.com
Source: securelist.com – Author: Alexander Kirichenko, Gleb Ivanov Introduction Knowledge is our best weapon in the fight against cybercrime. An understanding of how various gangs operate...
Cybercriminals Using PowerShell to Steal NTLMv2 Hashes from Compromised Windows – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 11, 2023THNEndpoint Security / Malware A new cyber attack campaign is leveraging the PowerShell script associated with a legitimate red...
New HijackLoader Modular Malware Loader Making Waves in the Cybercrime World – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 11, 2023THNCyber Crime / Malware A new malware loader called HijackLoader is gaining traction among the cybercriminal community to deliver...
Powerful Ethnic Militia in Myanmar Repatriates 1,200 Chinese Suspected of Involvement in Cybercrime – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press One of Myanmar’s biggest and most powerful ethnic minority militias has arrested and repatriated more than 1,200 Chinese nationals allegedly...
Associated Press warns that AP Stylebook data breach led to phishing attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams The Associated Press is warning of a data breach impacting AP Stylebook customers where the attackers used the stolen data...
‘Evil Telegram’ Android apps on Google Play infected 60K with spyware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Several malicious Telegram clones for Android on Google Play were installed over 60,000 times, infecting people with spyware that steals...
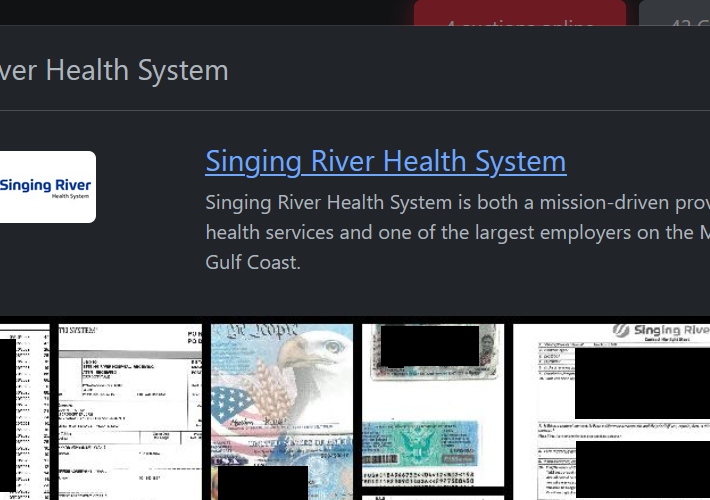
Rhysida Ransomware gang claims to have hacked three more US hospitals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Rhysida Ransomware gang claims to have hacked three more US hospitals Pierluigi Paganini September 10, 2023 Rhysida Ransomware group added...
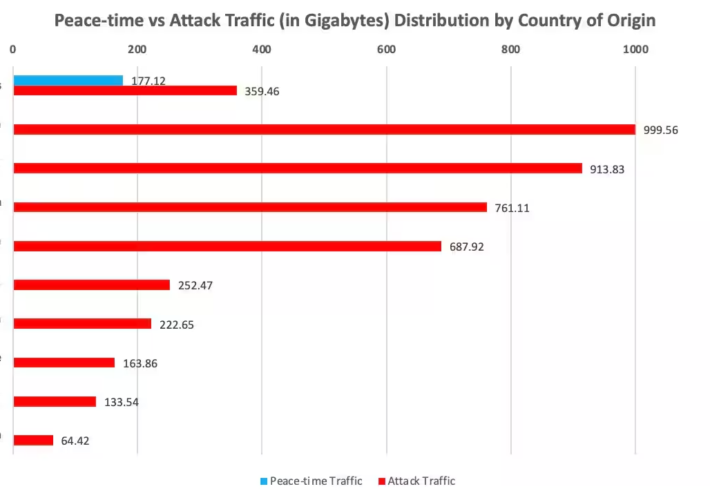
Akamai prevented the largest DDoS attack on a US financial company – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Akamai prevented the largest DDoS attack on a US financial company Pierluigi Paganini September 10, 2023 Akamai announced it has...
Security Affairs newsletter Round 436 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
BSides Buffalo 2023 – Jonathan D. Lawrence – Digital Possibilities For Research And Communication In The Humanities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/bsides-buffalo-2023-jonathan-d-lawrence-digital-possibilities-for-research-and-communication-in-the-humanities/ Category & Tags: CISO Suite,Governance, Risk &...
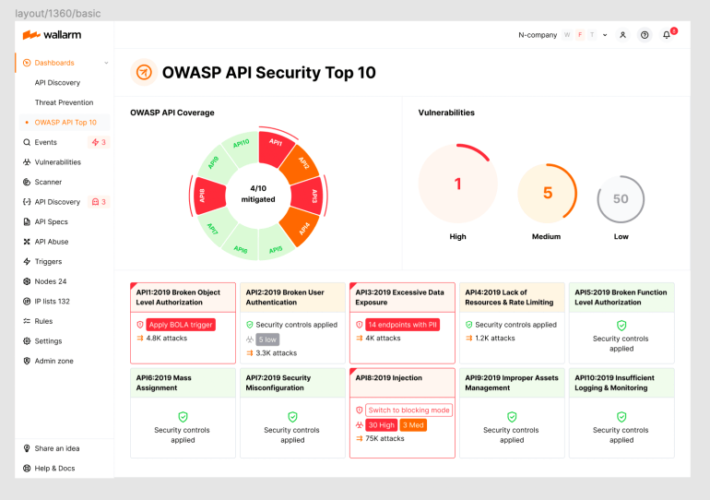
2023 OWASP Top-10 Series: API7:2023 Server Side Request Forgery – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Welcome to the 8th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...