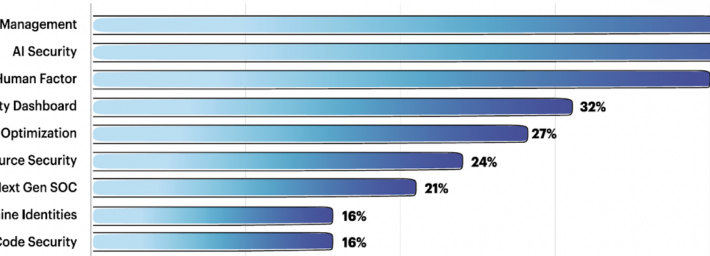
Source: www.securityweek.com – Author: Kevin Townsend Team8 regularly consults with its CISO Village of around 350 enterprise CISOs over startup investments. AI security, 3rd party risk...
Day: September 8, 2023
See Tickets Alerts 300,000 Customers After Another Web Skimmer Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Ticketing services agency See Tickets has notified more than 300,000 individuals that their payment card data was stolen in a...
CISA Releases Guidance on Adopting DDoS Mitigations – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Cybersecurity and Infrastructure Security Agency (CISA) has released new guidance to help federal agencies adopt distributed denial-of-service (DDoS)...
‘Atomic macOS Stealer’ Malware Delivered via Malvertising Campaign – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A piece of malware named Atomic macOS Stealer, or AMOS, has been delivered by cybercriminals through a malvertising campaign, Malwarebytes...
Cisco Patches Critical Vulnerability in BroadWorks Platform – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cisco on Wednesday announced patches for a critical-severity vulnerability in the BroadWorks Application Delivery Platform and BroadWorks Xtended Services Platform....
Tenable to Acquire Cloud Security Firm Ermetic for $240 Million – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Exposure management solutions provider Tenable announced on Thursday that it has entered into a definitive agreement to acquire Israeli cloud...
Apple Patches Two Zero-Days Exploited in Pegasus Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Apple has patched two critical zero-day vulnerabilities exploited in the wild to deliver eavesdropping malware from a notorious commercial spyware maker....
Patch ‘Em or Weep: Study Reveals Most Vulnerable IoT, Connected Assets – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg on September 7, 2023, 2:36 PM EDT Patch ‘Em or Weep: Study Reveals Most Vulnerable IoT, Connected Assets Phones, tablets...
Vendor Comparison: DIY Home Security Systems – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: When it comes to DIY home security, there are many systems and components to consider and many decisions to make. This vendor...
Spoofing attacks: What they are & how to protect your business – Source: securityboulevard.com
Source: securityboulevard.com – Author: Scott Wright Spoofing attacks often happen through email or online messaging services and rely on the victim to provide sensitive information, such...
Wallarm Presenting at BSides Albuquerque – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog If you’re in the Albuquerque area this Friday and/or Saturday, we hope you’re planning on going to BSides ABQ – it...
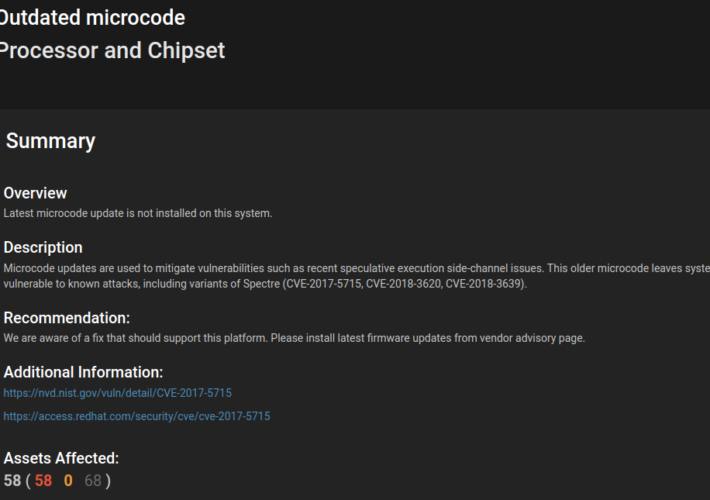
Demystifying CPU Microcode: Vulnerabilities, Updates, and Remediation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Asadoorian Attacks against low-level CPU architecture popped up on most tech people’s radar after the introduction of the Spectre and Meltdown...
High-Profile California Bill Regulating Data Brokers Heads for Key Vote – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt California lawmakers later this month are expected to vote on a highly debated bill that would make it easier for...
BSides Buffalo 2023 – Paul Robinson – If You Build It, They Will Come – A Guide To Building A Cybersecurity Program – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/bsides-buffalo-2023-paul-robinson-if-you-build-it-they-will-come-a-guide-to-building-a-cybersecurity-program/ Category & Tags: CISO Suite,Governance, Risk &...
Diving in to Day 2 Ops, Stateful Apps, & more with Kubernetes Experts – Source: securityboulevard.com
Source: securityboulevard.com – Author: Danielle Cook We had so many great questions about Kubernetes in the Enterprise in our recent Cloud Native Now webinar that I...
Ransomware and the Supply Chain – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland This white paper discusses the increasing threat of ransomware attacks on the technology supply chain and provides insights on how...
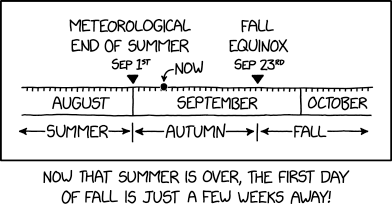
Randall Munroe’s XKCD ‘*Autumn And Fall’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/randall-munroes-xkcd-autumn-and-fall/ Category & Tags: Humor,Security Bloggers Network,Randall Munroe,Sarcasm,satire,XKCD...
BSides Buffalo 2023 – Kelsey Seymour – Dispelling The Myth Of “Maturity” In Threat Hunting – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/09/bsides-buffalo-2023-kelsey-seymour-dispelling-the-myth-of-maturity-in-threat-hunting/ Category & Tags: CISO Suite,Governance, Risk &...
Trail of Errors Led to Chinese Hack of Microsoft Cloud Email – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Encryption & Key Management , Fraud Management & Cybercrime Crash Dump Snapshot Included Active Signing Key...
5 Simple Ways to Improve Your Cybersecurity Posture – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Matt Wiseman Sr. Product manger, OPSWAT Matt Wiseman is a Sr. Product Manager at OPSWAT managing the OT product line. Matt’s...
Tattletale Ransomware Gangs Threaten to Reveal GDPR Breaches – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Repeat Shakedown Tactic: Victims Told to Pay Up or Else They’ll Face Massive Fines Mathew...
Why Connected Devices Are Such a Risk to Outpatient Care – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 The number of connected devices used in healthcare is growing as manufacturers constantly introduce new types of IoT equipment. The ever-evolving...
California Executive Order Hopes to Ensure ‘Trustworthy AI’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Government , Industry Specific Governor Sets 2-Year Deadline for Policies on AI Use, Risks at...
Keeping Your Side of the Street Clean: 5 Cyber-Hygiene Facts You Wish You Knew Earlier – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Brian Reed Chief Mobility Officer, NowSecure Brian Reed brings decades of experience in mobile, apps, security, dev and operations helping Fortune...
Breach Roundup: Swedish Insurer Fined $3M for GDPR Breach – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Incident & Breach Response , Ransomware Also, Google Fitbit Faces Privacy Complaints From Schrems Anviksha More...
Experts Probe AI Risks Around Malicious Use, China Influence – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Senate Hearing Examines Misuse of Advanced AI Systems, Risks With...
Damaging hack? Compensation could be in the balance – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Key highlights In 2022, a small number of public companies (86 total) linked chief executive pay to cyber security....
Microsoft ID Security Gaps That Let Threat Actor Steal Signing Key – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Several security missteps on Microsoft’s part allowed a China-based threat actor to forge authentication tokens and...
North Korean Hackers Target Security Researchers — Again – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading North Korean state-supported threat actors are targeting security researchers — the second such campaign in the...
Apple Hit By 2 No-Click Zero-Days in Blastpass Exploit Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Citizen Lab discovered two no-click zero-day vulnerabilities while checking an unidentified individual’s device, which was delivering mercenary...