Source: thehackernews.com – Author: . Sep 08, 2023THNCybercrime / Malware The U.K. and U.S. governments on Thursday sanctioned 11 individuals who are alleged to be part...
Day: September 8, 2023
Cisco Issues Urgent Fix for Authentication Bypass Bug Affecting BroadWorks Platform – Source:thehackernews.com
Source: thehackernews.com – Author: . Cisco has released security fixes to address multiple security flaws, including a critical bug, that could be exploited by a threat...
Protecting Your Microsoft IIS Servers Against Malware Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Microsoft Internet Information Services (IIS) is a web server software package designed for Windows Server. Organizations commonly use Microsoft IIS servers...
‘Evil Telegram’ Spyware Campaign Infects 60K+ Mobile Users – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading Dangerous spyware masquerading as a set of legitimate Telegram “mods” inside the official Google Play...
Kenya Initiates Public Sector Digital Skills Training, No Mention of Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Kenya plans to open a center of excellence to better train public sector staff in digital...
Trickbot, Conti Sanctions Affect Top Cybercrime Brass – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The Russia-based Trickbot and Conti cybercrime syndicates are facing increased pressure from the United States and the...
3 Strategies to Defend Against Resurging Infostealers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ganesh Pai, Founder & CEO, Uptycs Most enterprise chief information security officers (CISOs) are very familiar with infostealers, a pervasive breed of...
Software Supply Chain Strategies to Parry Dependency Confusion Attacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Liad Cohen, Security Researcher & Developer, OX Security “What’s in a name? That which we call a rose By any other name...
Securing Your Legacy: Identities, Data, and Processes – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dirk Schrader, Resident CISO (EMEA) & VP of Security Research, Netwrix Legacy systems are the bane of IT pros everywhere. “Legacy” generally...
Overcoming Open Source Vulnerabilities in the Software Supply Chain – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft As workforces grow increasingly digital, developers are looking for new ways to streamline their workloads. Currently, 78% of businesses report using...
Dymocks Booksellers suffers data breach impacting 836k customers – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Dymocks Booksellers is warning customers their personal information was exposed in a data breach after the company’s database was shared...
Cisco warns of VPN zero-day exploited by ransomware gangs – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Cisco is warning of a CVE-2023-20269 zero-day vulnerability in its Cisco Adaptive Security Appliance (ASA) and Cisco Firepower Threat Defense...
Microsoft Paint in Windows 11 gets a background removal tool – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Microsoft is rolling out a new version of the Paint application on Windows 11 Insider builds that can remove the...
Cisco BroadWorks Is Affected by a Critical-Severity Vulnerability – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu The Cisco BroadWorks Application Delivery Platform and Cisco BroadWorks Xtended Services Platform are both affected by a serious vulnerability that...
Warning: RocketMQ Vulnerability Actively Exploited by Threat Actors – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu The U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds a new critical-severity vulnerability to its KEV catalog. The issue is...
Evil Telegram doppelganger attacks Chinese users – Source: securelist.com
Source: securelist.com – Author: Igor Golovin A while ago we discovered a bunch of Telegram mods on Google Play with descriptions in traditional Chinese, simplified Chinese...
Feds Urge Immediately Patching of Zoho and Fortinet Products – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Attack Surface Management , Critical Infrastructure Security , Cyberwarfare / Nation-State Attacks Multiple Nation-State Hacking Groups Actively Exploiting Known Vulnerabilities Mathew...
5 Simple Ways to Improve Your Cybersecurity Posture – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Matt Wiseman Sr. Product manger, OPSWAT Matt Wiseman is a Sr. Product Manager at OPSWAT managing the OT product line. Matt’s...
Tattletale Ransomware Gangs Threaten to Reveal GDPR Breaches – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware Repeat Shakedown Tactic: Victims Told to Pay Up or Else They’ll Face Massive Fines Mathew...
Why Connected Devices Are Such a Risk to Outpatient Care – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 The number of connected devices used in healthcare is growing as manufacturers constantly introduce new types of IoT equipment. The ever-evolving...
Trail of Errors Led to Chinese Hack of Microsoft Cloud Email – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Encryption & Key Management , Fraud Management & Cybercrime Crash Dump Snapshot Included Active Signing Key...
Keeping Your Side of the Street Clean: 5 Cyber-Hygiene Facts You Wish You Knew Earlier – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Brian Reed Chief Mobility Officer, NowSecure Brian Reed brings decades of experience in mobile, apps, security, dev and operations helping Fortune...
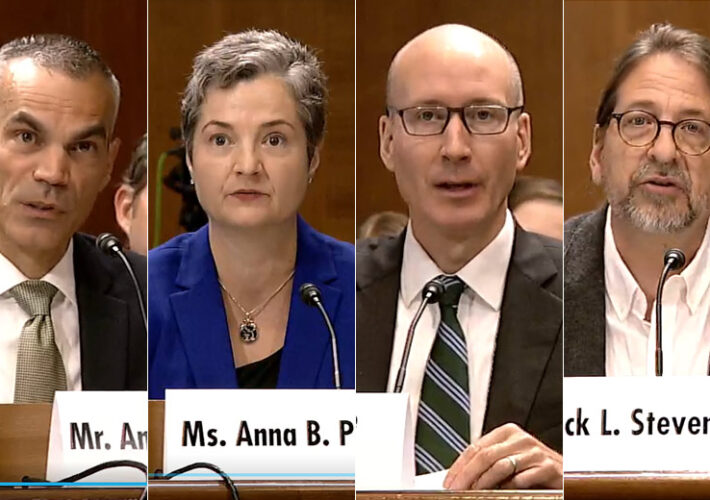
Experts Probe AI Risks Around Malicious Use, China Influence – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development Senate Hearing Examines Misuse of Advanced AI Systems, Risks With...
California Executive Order Hopes to Ensure ‘Trustworthy AI’ – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Government , Industry Specific Governor Sets 2-Year Deadline for Policies on AI Use, Risks at...
North Korean Hackers Exploit Zero-Day Bug to Target Cybersecurity Researchers – Source:thehackernews.com
Source: thehackernews.com – Author: . Threat actors associated with North Korea are continuing to target the cybersecurity community using a zero-day bug in unspecified software over...
CISA Warning: Nation-State Hackers Exploit Fortinet and Zoho Vulnerabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 08, 2023THNEndpoint Security / Exploit The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday warned that multiple nation-state actors...
Apple Rushes to Patch Zero-Day Flaws Exploited for Pegasus Spyware on iPhones – Source:thehackernews.com
Source: thehackernews.com – Author: . Sep 08, 2023THNSpyware / Vulnerability Apple on Thursday released emergency security updates for iOS, iPadOS, macOS, and watchOS to address two...
Apple Patches Actively Exploited iOS, macOS Zero-Days – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Apple on Thursday pushed out an urgent point-update to its flagship iOS and macOS platforms to fix a pair of...
Rigged Software and Zero-Days: North Korean APT Caught Hacking Security Researchers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Google’s threat hunting unit has again intercepted an active North Korean APT actor sliding into the DMs of security researchers...
Wealthy Russian With Kremlin Ties Gets 9 Years in Prison for Hacking and Insider Trading Scheme – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press A wealthy Russian businessman with ties to the Kremlin was sentenced Thursday to nine years in prison for his role...