Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 15
Day: September 1, 2023
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 12
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 1
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Weaknesses in Cisco ASA SSL VPNs Exploited Through Brute-Force Attacks – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa In a recent surge of cyber threats, hackers have targeted Cisco Adaptive Security Appliance (ASA) SSL VPNs using a combination...
Heimdal’s MXDR Adapt: World’s First Tailored SOC Service – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac Heimdal® unveils MXDR Adapt, a transformative evolution of its Managed Extended Detection and Response (MXDR) solution. This revolutionary adaptive control...
Notorious QakBot Malware Dismantled: $8.6M Seized and 700K Computers Freed – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Popa On Tuesday, the U.S. Department of Justice announced the disruption of an international law enforcement operation that targeted the QakBot...
Own Your Own Government Surveillance Van – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier A used government surveillance van is for sale in Chicago: So how was this van turned into a mobile spying...
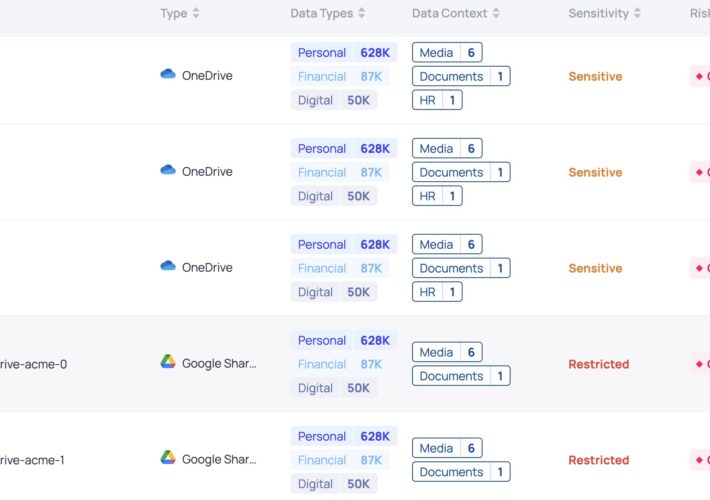
Laminar strengthens cloud data security with Microsoft OneDrive and Google Drive integration – Source: securityboulevard.com
Source: securityboulevard.com – Author: Dave Stuart New cloud file share integrations mark a pivotal moment for holistic data security posture management in the cloud In today’s...
The Gig Economy: 6 Attack Scenarios to Remember – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers While the primary goal of gig economy platforms is to facilitate connections between users and service providers, threat actors can...
Tips and Tools for Open Source Compliance – Source: securityboulevard.com
Source: securityboulevard.com – Author: AJ Starita You don’t need us to tell you that open source software is becoming a very significant percentage of commercial software...
APT Group Earth Estries Runs Espionage Campaigns Against US, Others – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt A newly discovered cyber-espionage threat group for at least three years has been using advanced and novel tools to steal...
News alert: Voxel AI increases funding to $30M, aims to transform industrial workplace safety – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido San Francisco, Calif., Aug. 30, 2023 — Every year over 340m workers suffer a workplace injury: slips and falls, strains and...
BSides Cheltenham 2023 – Gert-Jan Bruggink – Reimagining The Intelligence Deliverables Using Structured Threat Content – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsides-cheltenham-2023-gert-jan-bruggink-reimagining-the-intelligence-deliverables-using-structured-threat-content/ Category & Tags: CISO Suite,Governance, Risk &...
SANS 2023 DevSecOps Survey – Source: securityboulevard.com
Source: securityboulevard.com – Author: Synopsys Editorial Team Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/sans-2023-devsecops-survey/ Category & Tags: DevOps,Security Bloggers Network,DevSecOps,Security...
Discovering Unknown Problems in the Alert Pipeline – Source: securityboulevard.com
Source: securityboulevard.com – Author: SafeBreach Financial services institutions (FSIs) have become an increasingly common target for malicious actors. According to Boston Consulting Group, FSIs are 300...
BadBazaar: Chinese Spyware Shams Signal, Telegram Apps – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings After sneaking into Google and Samsung app stores, “GREF” APT targets Uyghurs and other PRC minorities. China stands accused of...
All Alarms, No Time: What My Training as a Black Hawk Pilot Taught Me About Privileged Access Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: James Hauswirth August 31, 2023 In 2013, I began training in the Army to be a Black Hawk pilot. The requirements I...
Chinese APT Uses Fake Messenger Apps to Spy on Android Users – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Fraud Management & Cybercrime , Social Engineering Trojanized Apps Impersonate Signal and Telegram Mihir Bagwe (MihirBagwe) • August...
Forever 21 Breach Notification Leaves Unanswered Questions – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Security Operations 539,207 Employees Warned This Week About 8-Week Breach Discovered in March Mathew J. Schwartz (euroinfosec) •...
SentinelOne CEO on Wiz M&A: ‘Pure Speculation on Their Part’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cloud Security , Endpoint Detection & Response (EDR) , Endpoint Protection Platforms (EPP) Tomer Weingarten Nixes Wiz Reselling Agreement After Not...
Webinar | Understanding Privacy Issues with Generative AI – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Proof of Concept: Securing Digital Government Services – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific The Panelists Also Discuss Improving the User Experience and Verifying Identities Anna...
UK Lawmakers Call For Swift Adoption of AI Policy – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development , Standards, Regulations & Compliance UK Risks Falling Behind EU...