Source: www.techrepublic.com – Author: Ray Fernandez Arc browser: Fast facts Key features: User-centered, highly customizable design, rich in features, integrates apps with web browsing to create...
Month: August 2023
Cisco Announces General Availability of XDR Platform – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg In alliance with Cohesity and others, Cisco is fueling near-zero latency between ransomware detection and remediation with its Extended Detection...
How Malicious Android Apps Slip Into Disguise – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Researchers say mobile malware purveyors have been abusing a bug in the Google Android platform that lets them sneak malicious code...
New Microsoft Azure AD CTS feature can be abused for lateral movement – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Microsoft’s new Azure Active Directory Cross-Tenant Synchronization (CTS) feature, introduced in June 2023, has created a new potential attack surface...
Hacktivists fund their operations using common cybercrime tactics – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hacktivist groups that operate for political or ideological motives employ a broad range of funding methods to support their operations....
Microsoft shares fix for Outlook asking to reopen closed windows – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft is investigating an issue causing Outlook Desktop to unexpectedly ask users to restore windows closed during a previous session....
Google makes it easier to remove your info, explicit images from search – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Google will soon make it easier to remove your personally identifiable information and explicit images from search results right from...
US govt contractor Serco discloses data breach after MoveIT attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Serco Inc, the Americas division of multinational outsourcing company Serco Group, has disclosed a data breach after attackers stole the...
Brave Search adds private image and video search capability – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The privacy-focused search engine Brave Search has finally introduced its own, independent image and video search capabilities, breaking free from...
Hackers can abuse Microsoft Office executables to download malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ionut Ilascu The list of LOLBAS files – legitimate binaries and scripts present in Windows that can be abused for malicious purposes,...
FBI, CISA, and NSA reveal top exploited vulnerabilities of 2022 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan In collaboration with CISA, the NSA, and the FBI, Five Eyes cybersecurity authorities have issued today a list of the...
Chrome malware Rilide targets enterprise users via PowerPoint guides – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The malicious Rilide Stealer Chrome browser extension has returned in new campaigns targeting crypto users and enterprise employees to steal...
VMConnect: Malicious PyPI packages imitate popular open source modules – Source: securityboulevard.com
Source: securityboulevard.com – Author: Karlo Zanki ReversingLabs has identified several malicious Python packages on the Python Package Index (PyPI) open source repository. In all, ReversingLabs researchers...
Tunnel Vision: CloudflareD AbuseD in the WilD – Source: securityboulevard.com
Source: securityboulevard.com – Author: Nic Finn August 3, 2023 Across the cybersecurity community, defenders are constantly finding threat actors using novel and innovative techniques to further...
BSides Leeds 2023 – Dan Cannon – Red Red Whine – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Safeguarding User Data: How Innovative Technologies Are Bolstering Client Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ainsley Lawrence As an entrepreneur, you likely know just how valuable data is in the current business landscape. Having access to vast...
Fidelis Security is now Part of Partner One. – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ingrid Kambe Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
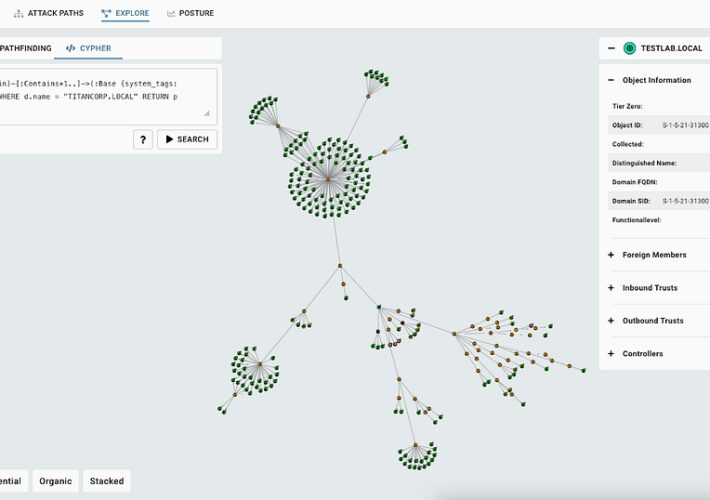
BloodHound Enterprise Learns Some New Tricks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stephen Hinck Summary The BloodHound code-convergence project brings some significant and long-desired feature enhancements to BloodHound Enterprise (BHE): Cypher search, including pre-built...
Microsoft is a “Strategic Problem in the Security Space,” Says CEO – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Yoran has had enough—and he’s not gonna take it anymore. Tenable CEO Amit Yoran says his team reported a critical...
Randall Munroe’s XKCD ‘How to Coil a Cable’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
The Impact of Bots on Airline and Travel Industries – Source: securityboulevard.com
Source: securityboulevard.com – Author: Siddharth Deb Airlines and travel industry operators, badly impacted during the Covid pandemic, are now full steam ahead catering to a growing...
Understanding social engineering and preventing account takeovers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team Account takeover attacks are one of the most prevalent forms of online fraud—and they continue to rise...
Fortinet Sales Growth Slows as Enterprise Deals Get Delayed – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Government , Industry Specific Shorter Average Contrast Duration, Deal Delays Force Fortinet to Cut Sales Forecast...
Modern-Day Hacktivist Chaos: Who’s Really Behind the Mask? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime Russia Likely Continues to Run Fake Groups, Although Regional Players Also at...
ChatGPT and Generative AI: Balancing Risks and Rewards – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Rodman Ramezanian, global threat lead, Skyhigh Security Generative AI offers productivity gains, but if deployed without due security precautions, it can...
Russian Hacking Group Shakes Up Its Infrastructure – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime ‘BlueCharlie’ Favors a New Domain Registrar and URL Structure Mihir Bagwe (MihirBagwe)...
US Man Admits to $4.5B Bitfinex Hack, Money Laundering – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cryptocurrency Fraud , Fraud Management & Cybercrime ‘Crypto Couple’ Ilya Lichenstein and Heather Morgan Plead Guilty Rashmi Ramesh (rashmiramesh_) • August...
Russian Hackers Are Pretending to Be Microsoft Tech Support – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Social Engineering Russian Foreign Intelligence Campaign Targets Around 40 Organizations Globally Prajeet Nair (@prajeetspeaks) • August...
The Need for Trustworthy AI – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier If you ask Alexa, Amazon’s voice assistant AI system, whether Amazon is a monopoly, it responds by saying it doesn’t...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...