Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
Month: August 2023
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
Ransomware Victims Surge as Threat Actors Pivot to Zero-Day Exploits – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading The number of organizations that became victims of ransomware attacks surged 143% between the first quarter...
Apple Users See Big Mac Attack, Says Accenture – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Schwartz, Contributing Writer, Dark Reading It’s no surprise that Apple Mac computers have become prize attack targets in recent years, but...
SecurityScorecard Launches Managed Cyber Risk Services to Mitigate Zero-Day and Critical Supply Chain Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 BLACK HAT 2023, LAS VEGAS – August 7, 2023 — SecurityScorecard today announced new partner-focused Managed Cyber Risk Services designed to help customers of all types...
Akamai Research: Rampant Abuse of Zero-Day and One-Day Vulnerabilities Leads to 143% Increase in Victims of Ransomware – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 CAMBRIDGE, Mass., Aug. 7, 2023 /PRNewswire/ — Akamai Technologies, Inc. (NASDAQ: AKAM), the cloud company that powers and protects life online, today released a new State...
SANS Teaches Cybersecurity Leadership in Saudi Arabia – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading SANS Institute will hold a training course for industry professionals in Riyadh, Saudi Arabia later this month....
Mallox Ransomware Group Revamps Malware Variants, Evasion Tactics – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading The Mallox ransomware group is stepping up its game in targeted attacks against organizations with vulnerable SQL...
Colorado Dept. of Higher Education Hit With Massive Data Breach – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading On Aug. 4, the Colorado Department of Higher Education (CDHE) learned that an authorized actor had accessed...
Selling Software to the US Government? Know Security Attestation First – Source: www.darkreading.com
Source: www.darkreading.com – Author: Donald Fischer, CEO & Co-Founder, Tidelift Over the past several months, the US government has introduced several new requirements affecting organizations that...
Name That Edge Toon: How Now? – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist Come up with an udderly amusing cybersecurity-related caption to explain the scene above, send it over, and our favorite...
Building Digital Trust in an Untrusting World – Source: securityboulevard.com
Source: securityboulevard.com – Author: Keyfactor Team Modern life depends on the integrity of critical infrastructure like railroads, ports, highways, power plants, water treatment facilities, and others....
Threat of Side-Channel Attacks Increases with Deep-Learning Model – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The rapid innovations in deep learning, expanding use of laptops, and growing number of smartphones with microphones are creating an...
Credential Security Enhances Privacy and Equity – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stan Bounev Last month we collaborated with Botcopy to enhance the security of their latest new authentication chat skill, adding massive value...
CISA Outlines Plan to Get Ahead of Cyberthreat Groups – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The nation’s top cybersecurity agency is envisioning a future where the federal government and private companies alike set the rules...
SEC Cybersecurity Ruling – What to Know and How to Prepare – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kayla Kinney On July 26, 2023, the Securities and Exchange Commission (SEC) voted to adopt new rules on cybersecurity disclosures for publicly...
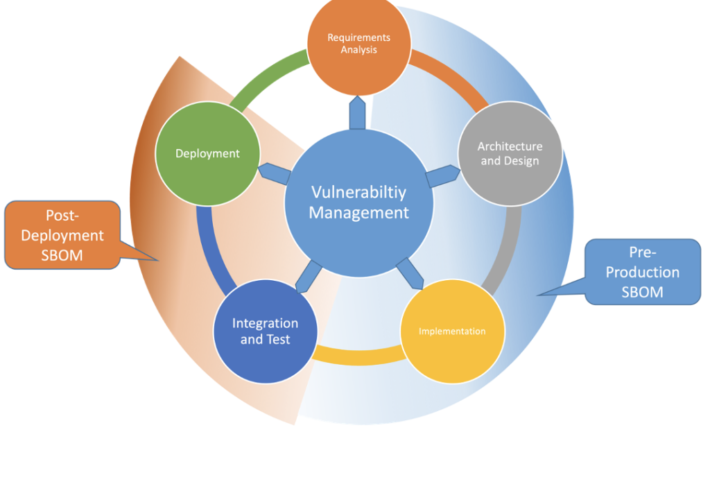
The Power of Post-Production SBOMs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Hermeling The use cases and lifecycle of Software Bills of Materials (SBOM) are starting to coalesce as software organizations begin making...
Leap into Hybrid Environments and Modern Enterprise Asset Analysis with JupiterOne – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley Tony Bradley I have a passion for technology and gadgets–with a focus on Microsoft and security–and a desire to help...
Netography to Showcase Cloud-Native Network Defense Platform at Black Hat USA – Source: securityboulevard.com
Source: securityboulevard.com – Author: Netography As network security shifts to the cloud, Netography delivers first platform to address the entire network – cloud, on-prem, and the...