Source: www.bleepingcomputer.com – Author: Lawrence Abrams The Knight ransomware is being distributed in an ongoing spam campaign that pretends to be TripAdvisor complaints. Knight ransomware is a recent rebrand...
Month: August 2023
Ford says cars with WiFi vulnerability still safe to drive – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Ford is warning of a buffer overflow vulnerability in its SYNC3 infotainment system used in many Ford and Lincoln vehicles,...
Guarding Against Evolving Threats: Insights from the Q2 Email Threat Trends Report – Source: securityboulevard.com
Source: securityboulevard.com – Author: Stefanie Shank Stefanie Shank Stefanie Shank. Having spent her career in various capacities and industries under the “high tech” umbrella, Stefanie is...
Enhancing Identity Security and Permission Management with ConductorOne – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tony Bradley In today’s digital landscape, ensuring robust identity security and effective permission management is essential for businesses of all sizes, regardless...
BSides Leeds 2023 – Sara Anstey – Educating Your Guesses: How To Quantify Risk And Uncertainty – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsides-leeds-2023-sara-anstey-educating-your-guesses-how-to-quantify-risk-and-uncertainty/ Category & Tags: CISO Suite,Governance, Risk &...
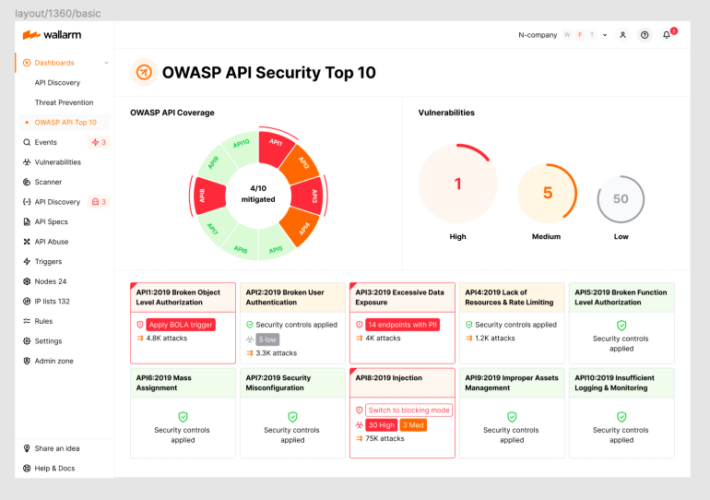
2023 OWASP Top-10 Series: API3:2023 Broken Object Property Level Authorization – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Welcome to the 4th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...
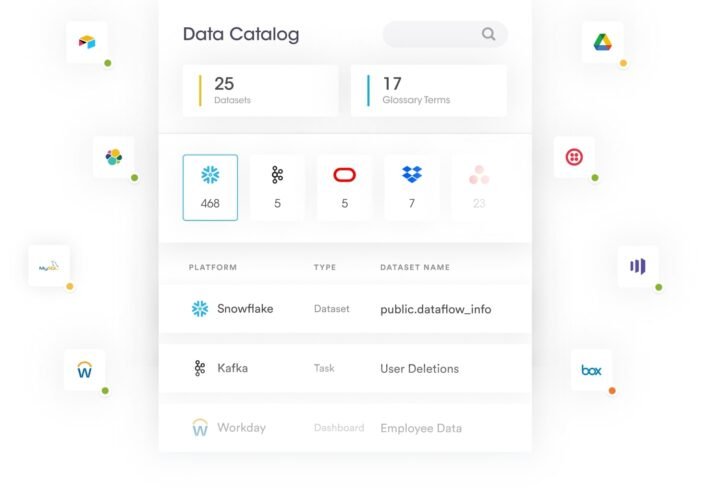
Improve Data Understanding, Accessibility, & Control With an Automated Data Catalog – Source: securityboulevard.com
Source: securityboulevard.com – Author: Securiti Research Team With the rapid expansion of data across multiple clouds, it is extremely difficult for companies to manually track all...
Multiple Flaws in CyberPower and Dataprobe Products Put Data Centers at Risk – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 12, 2023THNServer Security / Cyber Threat Multiple security vulnerabilities impacting CyberPower’s PowerPanel Enterprise Data Center Infrastructure Management (DCIM) platform and...
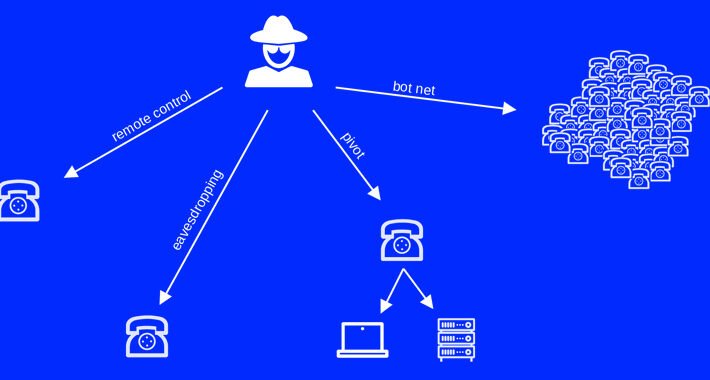
Zoom ZTP & AudioCodes Phones Flaws Uncovered, Exposing Users to Eavesdropping – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 12, 2023THNVulnerability / Privacy Multiple security vulnerabilities have been disclosed in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP)...
CISA makes two key security recommendations to stop SIM swapping – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: According to CISA, telecommunications firms are not adequately protecting consumers from SIM swapping. The agency recommends that public and...
Police dismantled bulletproof hosting service provider Lolek Hosted – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A joint operation conducted by European and U.S. law enforcement agencies dismantled the bulletproof hosting service provider Lolek Hosted. Lolek Hosted...
Python URL parsing function flaw can enable command execution – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A severe vulnerability in the Python URL parsing function can be exploited to gain arbitrary file reads and command execution....
UK govt contractor MPD FM leaks employee passport data – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini UK govt contractor MPD FM left an open instance that exposed employee passports, visas, and other sensitive data MPD FM,...
Power Generator in South Africa hit with DroxiDat and Cobalt Strike – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors employed a new variant of the SystemBC malware, named DroxiDat, in attacks aimed at African critical infrastructure. Researchers from...
Cybersecurity: It’s Time to Trust the Machines – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ori Arbel, Chief Technology Officer, CYREBRO I was driving home from work the other day, the same route I drive every evening....
Navigating Cybersecurity’s Seas: Environmental Regulations, OT & the Maritime Industry’s New Challenges – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jeffrey Wells, Partner, Sigma7 The International Maritime Organization (IMO) introduced the Energy Efficiency Design Index (EEDI) in 2011 to reduce CO2 emissions...
New LLM Tool Seeks and Remediates Vulnerabilities – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading BLACK HAT USA – Wednesday, Aug. 9 — A new large language model based on ChatGPT that...
It’s Time for Cybersecurity to Talk About Climate Change – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9 – In a summer where extreme...
‘Downfall’ Bug in Billions of Intel CPUs Reveals Major Design Flaw – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading BLACK HAT USA – Las Vegas – Wednesday, Aug. 9 Billions of computers running on Intel processors...
Major Police Breach Endangers Safety of Officers & Civilians – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A data leak may put the safety of 10,000 serving police officers in Northern Ireland in peril. The...
Attacker Breakout Time Shrinks Again, Underscoring Need for Automation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Attackers are getting quicker. New research reveals they have shaved a few more minutes off of...
Analyzing Network Chaos Leads to Better DDoS Detection – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading The Internet is a chaotic medium — packets tend to flow from a uniformly distributed set...
10 Key Controls to Show Your Organization Is Worthy of Cyber Insurance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Paul Trulove, CEO, SecureAuth Increasing concerns about ransomware and other breaches, especially at the credentials level, are likely why organizations are investing...
How to Prepare for ChatGPT’s Risk Management Challenges – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 The risks around ChatGPT are already here — and compliance officers need to prepare for battle against them immediately. In many...
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...