Source: www.bleepingcomputer.com – Author: Sponsored by Criminal IP In today’s ever-evolving digital landscape, the significance of effective malware detection remains paramount. With the escalating threat of...
Month: August 2023
Colorado warns 4 million of data stolen in IBM MOVEit breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney The Colorado Department of Health Care Policy & Financing (HCPF) is alerting more than four million individuals of a...
MaginotDNS attacks exploit weak checks for DNS cache poisoning – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A team of researchers from UC Irvine and Tsinghua University has developed a new powerful cache poisoning attack named ‘MaginotDNS,’...
Top 10 Key Takeaways on Navigating End-User Computing (EUC) Risks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kimberly Rose In today’s digital age, as businesses heavily rely on End-User Computing (EUC) tools, the landscape of risks they face has...
Diligere, Equity-Invest Are New Firms of U.K. Con Man – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs John Clifton Davies, a convicted fraudster estimated to have bilked dozens of technology startups out of more than $30 million through...
Blameless Locks Down Security Incident Management Over Slack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Blameless is making it simpler for security operations (SecOps) teams to manage multiple conversations across the Slack instant messaging platform...
BSides Leeds 2023 – Samantha Humphries – Destination Unknown: Career Musings Of A Former [Redacted] Agent – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Monti Returns From 2-Month Break with Revamped Ransomware Variant – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The Monti ransomware group that emerged in June 2022 used source code, tools, and tactics – not to mention an...
The Price of Convenience: How Security Vulnerabilities in Global Transportation Payment Systems Can Cost You – Source: securityboulevard.com
Source: securityboulevard.com – Author: Omer Attias Public transportation payment systems have undergone significant changes over the years. Mobile payment solutions have become increasingly popular, allowing passengers...
Randall Munroe’s XKCD ‘Perseids Pronunciation’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Mitigating Human Errors in Cybersecurity & Compliance: Practical Tips for Organizations – Source: securityboulevard.com
Source: securityboulevard.com – Author: Adar Givoni, Director of Compliance, Scytale The Importance of Cybersecurity Cybersecurity is of paramount importance in today’s digital world. With the increasing...
OWASP researcher: Supply chain attacks show organizations must shift beyond vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Carolynn van Arsdale It’s not news that software supply chain attacks have become a pervasive threat. They have increased greatly — while...
Activist Investor Directs OneSpan to Pursue ‘Immediate Sale’ – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Identity & Access Management , Security Operations Legion Partners Calls on Identity Verification Provider to Reduce Costs, Find Buyer Michael Novinson...
Live Webinar | Security Leaders: How to Achieve SEC Compliance – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
How to Block API Attacks in Real Time – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 API Security The Different Types of API Attacks and Best Practices for API Security Shay Levi • August 3, 2023 ...
Multiple Flaws Uncovered in Data Center Systems – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Vulnerabilities Found in CyberPower and Dataprobe Products Prajeet Nair (@prajeetspeaks) • August 14, 2023...
Live Webinar | Government Intervention: The Rise of the SBOM and the Evolution of Software Supply Chain Security – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Ilkka Turunen Field CTO, Sonatype lkka Turunen is Field CTO at Sonatype, working with leading companies across the globe to understand...
Data Theft Via MOVEit: 4.5 Million More Individuals Affected – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Security Operations Latest Tally of Clop Campaign Victims: 670 Organizations, 46 Million Individuals Mathew J. Schwartz (euroinfosec) •...
Healthcare System Notifies 180,000 People 1 Year After Hack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Breach Notification , Healthcare , Industry Specific Multiple Challenges Can Delay Breach Response and Notification, Experts Say Marianne Kolbasuk McGee (HealthInfoSec)...
Women in CyberSecurity (WiCyS) Hosting Fifth Annual Virtual Career Fair – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 COOKEVILLE, Tenn., Aug. 14, 2023 /PRNewswire-PRWeb/ — Women in CyberSecurity (WiCyS) is hosting its next Virtual Career Fair on Wednesday, Aug. 16, 11 a.m.- 5 p.m. CT, which is...
Phishing Operators Make Ready Use of Abandoned Websites for Bait – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Attackers are increasingly targeting abandoned and barely maintained websites for hosting phishing pages, according to a...
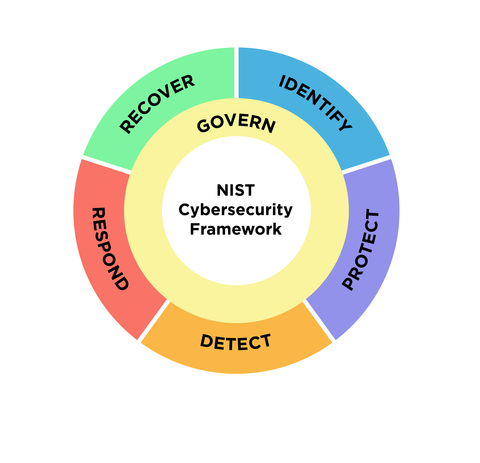
What’s New in the NIST Cybersecurity Framework 2.0 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading First introduced nearly a decade ago as technical cybersecurity guidance for critical infrastructure interests like energy, banking,...
Russian-African Security Gathering Exposes Kremlin’s Reduced Influence – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Heads of government from the Russian Federation and African states, along with representatives from the African Union and Africa’s integration...
Health Data of 4M Stolen in Cl0p MOVEit Breach of Colorado Department – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A government department in Colorado is the latest victim of a third-party attack by Russia’s Cl0p ransomware...
Following Pushback, Zoom Says It Won’t Use Customer Data to Train AI Models – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Zoom says it will walk back a recent change to its terms of service that allowed...
Lock Down APIs to Prevent Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Web and mobile application developers need to take more care in creating secure applications, as attackers...
Interpol Shuts Down Phishing Service ’16shops’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Three individuals in Indonesia and Japan were arrested for their alleged roles in “16shop,” a notorious phishing-as-a-service...
7 Reasons People Don’t Understand What You Tell Them – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joshua Goldfarb, Security and Fraud Architect, F5 I’ve been fascinated by the difference between what one person writes, says, or does and...
5 Ways CISA Can Help Cyber-Poor Small Businesses & Local Governments – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kevin O’Connor, Director of Threat Research, Adlumin For far too long, the cybersecurity industry has primarily focused on protecting the largest organizations...
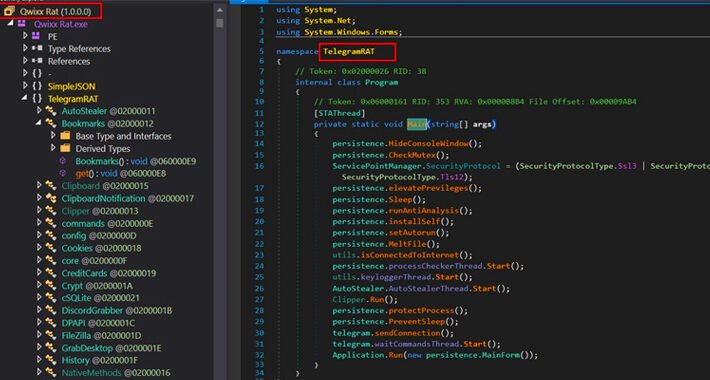
QwixxRAT: New Remote Access Trojan Emerges via Telegram and Discord – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 14, 2023THNCyber Threat / Malware A new remote access trojan (RAT) called QwixxRAT is being advertised for sale by its...






![bsides-leeds-2023-–-samantha-humphries-–-destination-unknown:-career-musings-of-a-former-[redacted]-agent-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2023/08/74074/bsides-leeds-2023-samantha-humphries-destination-unknown-career-musings-of-a-former-redacted-agent-source-securityboulevard-com-710x500.jpg)