Source: www.infosecurity-magazine.com – Author: 1 Generative AI tools are the most effective way to tackle financial crime, but also a number one threat, according to a...
Month: August 2023
PSNI: Leaked Data Will be Used to Target Police Officers – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Sensitive details of 10,000 Northern Ireland police officers and staff are in the hands of paramilitary groups, the Police Service of...
Over 100,000 Users of Hacking Forums Infected With Malware – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have discovered over 140,000 breached passwords associated with accounts on hacking forums after their owners were infected with info-stealing...
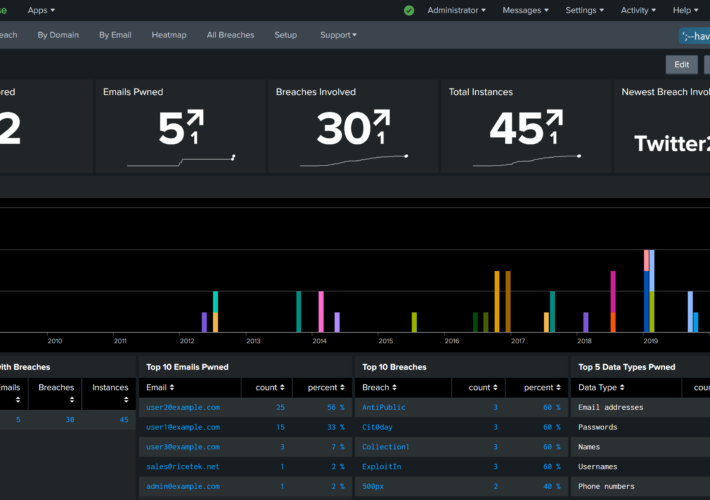
All New Have I Been Pwned Domain Search APIs and Splunk Integration – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I’ve been teaching my 13-year old son Ari how to code since I first got him started on Scratch many...
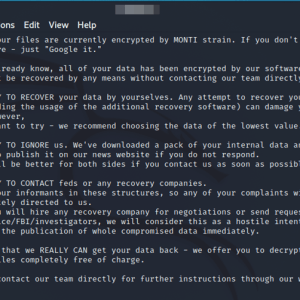
Monti Ransomware gang launched a new Linux encryptor – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Monti Ransomware operators returned, after a two-month pause, with a new Linux variant of their encryptor. The Monti ransomware operators...
Hacking ATMs by exploiting flaws in ScrutisWeb ATM fleet software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers found several flaws in the ScrutisWeb ATM fleet monitoring software that can expose ATMs to hack. Researchers from the...
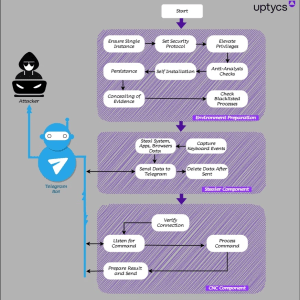
QwixxRAT, a new Windows RAT appears in the threat landscape – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini QwixxRAT is a new Windows remote access trojan (RAT) that is offered for sale through Telegram and Discord platforms. The...
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Quantum computing: Will it break crypto security within a few years? – Source:
Source: – Author: 1 Current cryptographic security methods watch out – quantum computing is coming for your lunch. Original Post URL: Category & Tags: – Views:...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
Cybercriminals Abusing Cloudflare R2 for Hosting Phishing Pages, Experts Warn – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023THNHosting / Phishing Threat actors’ use of Cloudflare R2 to host phishing pages has witnessed a 61-fold increase over...
Multiple Flaws Found in ScrutisWeb Software Exposes ATMs to Remote Hacking – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023THNCyber Threat / Software Security Four security vulnerabilities in the ScrutisWeb ATM fleet monitoring software made by Iagona could...
Monti Ransomware Returns with New Linux Variant and Enhanced Evasion Tactics – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023THNLinux / Ransomware The threat actors behind the Monti ransomware have resurfaced after a two-month break with a new...
Malware Unleashed: Public Sector Hit in Sudden Surge, Reveals New Report – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 15, 2023The Hacker NewsThreat Intelligence / Cyber Attacks The just-released BlackBerry Global Threat Intelligence Report reveals a 40% increase in...
Bolstering Africa’s Cybersecurity – Source: www.darkreading.com
Source: www.darkreading.com – Author: Bill Carter, Cyber Security Engineer, Cato Networks According to recent data, African nations faced a significantly larger number of cyberattacks in 2022...
Microsoft Cloud Security Woes Inspire DHS Security Review – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The US Department of Homeland Security (DHS) late last week kicked off an investigation into the...
How & Why Cybercriminals Fabricate Data Leaks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Yuliya Novikova, Head of Digital Footprint Intelligence, Kaspersky Data leaks pose a significant and escalating challenge for companies globally, particularly due to...
How to Choose a Managed Detection and Response (MDR) Solution – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Managed detection and response (MDR) has emerged as a crucial solution for organizations looking to bolster their security measures. MDR allows...