Source: www.bleepingcomputer.com – Author: Bill Toulas The China-aligned APT (advanced persistent threat) group known as ‘Bronze Starlight’ was seen targeting the Southeast Asian gambling industry with...
Month: August 2023
Weekly Update 361 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt This week hasd been manic! Non-stop tickets related to the new HIBP domain subscription service, scrambling to support invoicing and...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker’s convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the convention due to a...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 10
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 3
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 0
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 2
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
Foreign Intelligence Entities Eyeing US Space Agencies – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Standards, Regulations & Compliance China, Russia Are Leading Foreign Intelligence Threats...
App Security Posture Management Improves Software Security, Synopsys Says – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Jim Ivers and Natasha Gupta of Synopsys discuss customer challenges with application security. They talk about consolidation...
Cyderes Dives In On Working Safely With AI and Upping Your IAM Game – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading John Ayers and Mike Wyatt weigh in on how artificial intelligence has already been weaponized against businesses...
Tel Aviv Stock Exchange CISO: Making Better Use of Your SIEM – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading For Gil Shua, getting the most out of the security information event management (SIEM) system for...
Time To Address What’s Undermining SaaS Security, AppOmni Says – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading SaaS security is battling numerous excesses, according to AppOmni CEO Brendan O’Connor: entitlement inflation, over-provisioned accounts, and...
PKI Maturity Model Aims to Improve Crypto Infrastructure – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Creating and deploying public key infrastructure is notoriously difficult. However, a group of encryption vendors, consultancies,...
African Cybercrime Operations Shut Down in Law Enforcement Operation – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading In a months-long joint operation by Interpol and Afripol, 14 suspected cybercriminals have been arrested and more...
Researchers Trick an iPhone Into Faking Airplane Mode – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Researchers have figured out how to manipulate the iPhone user interface to feign airplane mode, while...
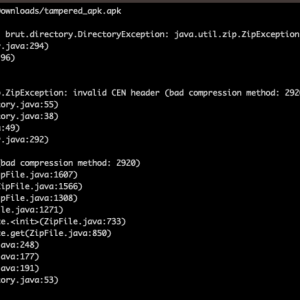
Over 3,000 Android Malware spotted using unsupported/unknown compression methods to avoid detection – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Threat actors are using Android Package (APK) files with unsupported compression methods to prevent malware analysis. On June 28th, researchers...
An Overview of Dubai’s First and Second Cybersecurity Strategy – Source: www.darkreading.com
Source: www.darkreading.com – Author: Diamaka Aniagolu, Cybersecurity Writer and Content Strategist In 2019, Binu Manaf, the CEO and managing director of Dubai’s Cheers Exhibition, received an...
LinkedIn Suffers ‘Significant’ Wave of Account Hacks – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Hackers are on a spree of hijacking LinkedIn accounts, in some cases monetizing the attacks by demanding...
BSidesTLV 2023 – Ofir Balassiano & Ofir Shaty – The Dark Side Of Cloud-Based Database Engines – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/08/bsidestlv-2023-ofir-balassiano-ofir-shaty-the-dark-side-of-cloud-based-database-engines/ Category & Tags: CISO Suite,Governance, Risk &...
2023 OWASP Top-10 Series: API4:2023 Unrestricted Resource Consumption – Source: securityboulevard.com
Source: securityboulevard.com – Author: wlrmblog Welcome to the 5th post in our weekly series on the new 2023 OWASP API Security Top-10 list, with a particular...