Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Month: August 2023
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 12
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 0
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 0
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 0
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
N. Korean Kimsuky APT targets S. Korea-US military exercises – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked APT Kimsuky launched a spear-phishing campaign targeting US contractors working at the war simulation centre. North Korea-linked APT...
Four Juniper Junos OS flaws can be chained to remotely hack devices – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Juniper Networks addressed multiple flaws in the J-Web component of Junos OS that could be chained to achieve remote code...
Security Affairs newsletter Round 433 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Cybersecurity: CASB vs SASE – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Understanding cybersecurity aspects addressed by Cloud Access Security Broker (CASB) and Secure Access Service Edge (SASE) In an increasingly digital...
Suspected N. Korean Hackers Target S. Korea-US Drills – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Suspected North Korean hackers have attempted an attack targeting a major joint military exercise between Seoul and Washington that starts on...
BSidesTLV 2023 – Paz Hameiri – Barcode Scanners Are Disguised Windows To Your Windows – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
2023 Cybersecurity Awareness Month Appeal: Make Online Security Easier – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Surveys show that most Americans think online security is too hard, confusing and frustrating. So as we prepare for Cybersecurity...
Using JupyterLab to Manage Password Cracking Sessions (A CMIYC 2023 Writeup) Part 1 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Matt Weir This year I didn’t compete in the Defcon Crack Me If You Can password cracking competition. It was my wife’s...
CISA Releases Cyber Defense Plan For Remote Monitoring And Management (RMM) Software – Source: securityboulevard.com
Source: securityboulevard.com – Author: Smit Kadakia RMM tools are the easy targets for cyber attackers, and the related news over past year has highlighted several breaches...
‘Play’ Ransomware Group Targeting MSPs Worldwide in New Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading The fast-rising Play ransomware group that targeted the City of Oakland earlier this year is now...
How Innovation Accelerators Are at Work on the Dark Side – Source: www.darkreading.com
Source: www.darkreading.com – Author: Paul Fabara, Chief Risk Officer, Visa The digital revolution has given rise to incredible innovation in consumer experiences, but the same innovation...
Cyber Defenders Lead the AI Arms Race for Now – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading Cyber defenders so far are winning the war over artificial intelligence: AI tools have yet to...
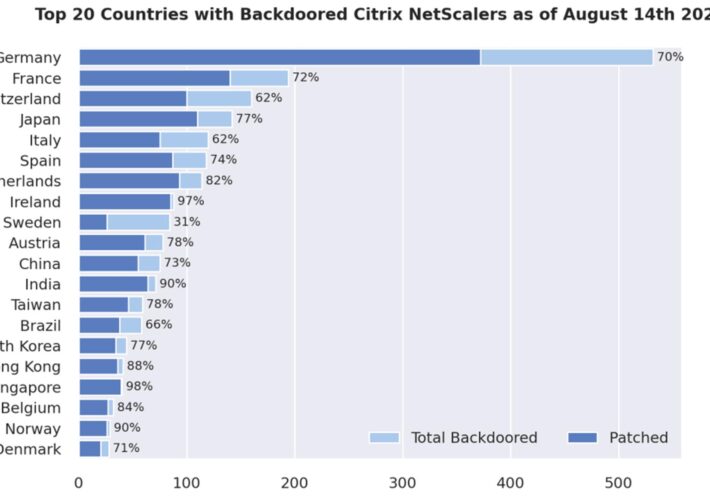
Citrix ADC, Gateways Still Backdoored, Even After Being Patched – Source: www.darkreading.com
Source: www.darkreading.com – Author: Edge Editors, Dark Reading Nearly 1,900 Citrix networking products around the world have been backdoored as part of a large-scale automated campaign...
8 AI Risk and Resilience Firms CISOs Should Track – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ericka Chickowski, Contributing Writer, Dark Reading Keep up with the latest cybersecurity threats, newly-discovered vulnerabilities, data breach information, and emerging trends. Delivered...
QR Code Phishing Campaign Targets Top US Energy Company – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Attackers targeted a major US energy company with a phishing campaign that overall sent more than 1,000...
Iran and the Rise of Cyber-Enabled Influence Operations – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Iranian state actors have another weapon in their arsenal. Since June 2022, multiple Iranian state groups have deployed a...
Mandiant Releases Scanner to Identify Compromised NetScaler ADC, Gateway – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading With thousands of Citrix networking products vulnerable to a critical vulnerability still unpatched and exposed on the...
Google Chrome to warn when installed extensions are malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Google is testing a new feature in the Chrome browser that will warn users when an installed extension has been...
Cuba ransomware uses Veeam exploit against critical U.S. organizations – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Image: Midjourney The Cuba ransomware gang was observed in attacks targeting critical infrastructure organizations in the United States and IT...