Source: securityaffairs.com – Author: Pierluigi Paganini Updated Kmsdx botnet targets IoT devices Researchers spotted an updated version of the KmsdBot botnet that is now targeting Internet of...
Month: August 2023
Massive MOVEit campaign already impacted at least 1,000 organizations and 60 million individuals – Source: securityaffairs.com
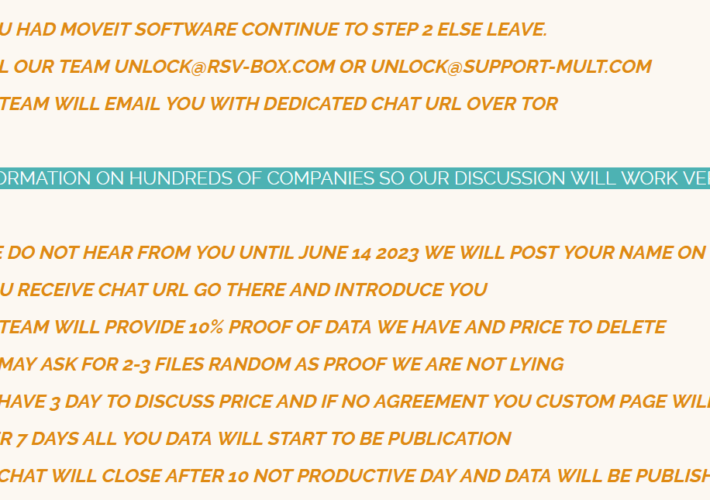
Source: securityaffairs.com – Author: Pierluigi Paganini Massive MOVEit campaign already impacted at least 1,000 organizations and 60 million individuals The recent wave of MOVEit attacks conducted by the...
Poland’s authorities investigate a hacking attack on country’s railways – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Poland’s authorities investigate a hacking attack on country’s railways The Polish domestic security agency is investigating a hacking attack on...
Leaked LockBit 3.0 ransomware builder used by multiple threat actors – Source: securityaffairs.com
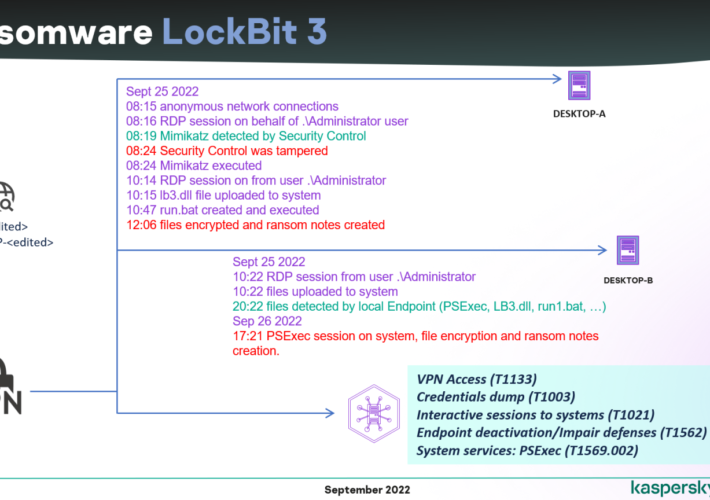
Source: securityaffairs.com – Author: Pierluigi Paganini Leaked LockBit 3.0 ransomware builder used by multiple threat actors The leak of the source code of the LockBit 3.0 ransomware builder...
Security Affairs newsletter Round 434 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Malware Unleashed: Public Sector Hit in Sudden Surge, Reveals New Research – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Report unmasks recent cybersecurity challenges for governments, healthcare, financial services, and vital infrastructure. Ismael Valenzuela, Vice President of Threat Research &...
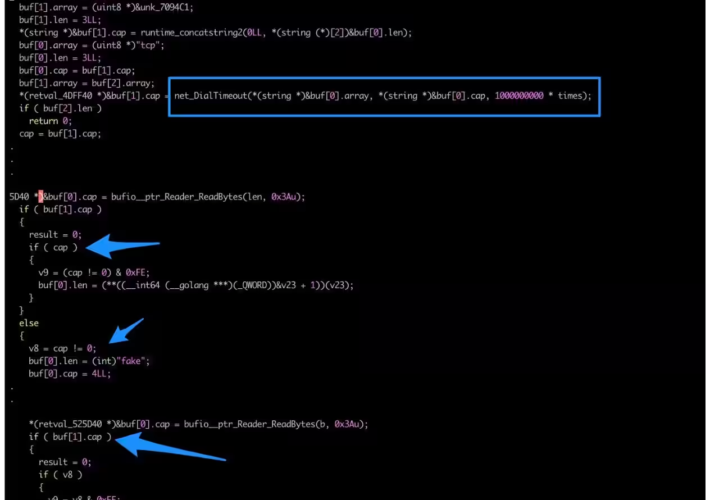
KmsdBot Malware Gets an Upgrade: Now Targets IoT Devices with Enhanced Capabilities – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 28, 2023THNInternet of Things / Malware An updated version of a botnet malware called KmsdBot is now targeting Internet of...
Cloud Repatriation: The Unforeseen Reversal in Cloud Computing Trends – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi As cloud computing continues to evolve, an intriguing new trend is emerging – cloud repatriation. This concept, also known as...
BSides Cheltenham 2023 – Simon Gurney – Making Your Own Cool Conference Badges! – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
What’s New in the NIST Cybersecurity Framework 2.0 Draft? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity NIST has released a draft version 2.0 of the Cybersecurity Framework. Here’s what you need to know and how...
SmokeLoader Trojan Deploys Location-Tracking Malware – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Customer Identity & Access Management (CIAM) , Cybercrime , Fraud Management & Cybercrime ‘Whiffy Recon’ Uses WiFi Access Points, Google API...
SmokeLoader Trojan Deploys Location-Tracking Malware – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Customer Identity & Access Management (CIAM) , Cybercrime , Fraud Management & Cybercrime ‘Whiffy Recon’ Uses WiFi Access Points, Google API...
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 1
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 2
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 17
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 1
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 1
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Weekly Update 362 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt Somehow in this week’s video, I forgot to talk about the single blog post I wrote this week! So here’s...
Cisco fixes 3 high-severity DoS flaws in NX-OS and FXOS software – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cisco addressed three high-severity flaws in NX-OS and FXOS software that could cause denial-of-service (DoS) conditions. Cisco this week addressed...
Cloud and hosting provider Leaseweb took down critical systems after a cyber attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The cloud and hosting provider Leaseweb suffered a security breach that impacted some “critical” systems of the company. Global hosting...