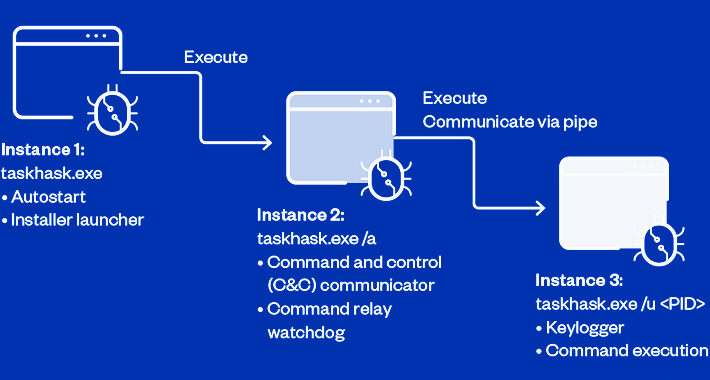
Source: www.securityweek.com – Author: Eduard Kovacs Researchers have abused dangling DNS records to hijack subdomains belonging to over a dozen major organizations, and they warn that...
Day: August 31, 2023
New Research Exposes Airbnb as Breeding Ground For Cybercrime – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cyber-criminals have been increasingly exploiting the Airbnb platform for fraudulent endeavors. A new analysis by cybersecurity experts at SlashNext highlighted the...
Facebook Accounts Targeted by Vietnamese Threat Groups – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cyber-attacks targeting Meta Business and Facebook accounts are gaining popularity among criminals in Vietnam, according to a new report published by...
GRU Blamed for Infamous Chisel Malware Targeting Ukraine’s Military Phones – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK and its Five Eyes partners (Australia, Canada, New Zealand and the US) officially support Ukraine’s attribution of Infamous Chisel,...
Russian APT Intensifies Cyber Espionage Activities Amid Ukrainian Counter-Offensive – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Russian APT group Gamaredon has intensified its cyber espionage activities ahead of and during Ukraine’s counter-offensive operations, according to a new...
Classiscam Spreads: $64.5M Scheme Targets 79 Countries – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Classiscam scam-as-a-service operation has grown into a $64.5 million worldwide threat, infiltrating 79 countries, according to cybersecurity experts at Group-IB....
Chinese Group Spreads Android Spyware via Trojan Signal, Telegram Apps – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading A China-based advanced persistent threat group that used an Android malware tool called BadBazaar to spy...
APT Attacks From ‘Earth Estries’ Hit Gov’t, Tech With Custom Malware – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading A newly identified threat actor is quietly stealing information from governments and technology organizations around the...
New York Times Spoofed to Hide Russian Disinformation Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A Russian disinformation campaign has been found spreading fake articles posing as legitimate stories from major media...
Earth Estries’ Espionage Campaign Targets Governments and Tech Titans Across Continents – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 31, 2023THNCyber Attack / Hacking A hacking outfit nicknamed Earth Estries has been attributed to a new, ongoing cyber espionage...
47,000 London Metropolitan Police Personnel Impacted by Data Breach – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși London`s Metropolitan Police announced bolstering cybersecurity measures after one of its suppliers detected a data breach. A contractor responsible for...
How to Manage XDR Alerts with Heimdal – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Adelina Deaconu With Heimdal XDR, you gain complete visibility into XDR alerts, network traffic, user behavior, and endpoint activity. It makes investigating...
Smashing Security podcast #337: The DEA’s crypto calamity, and scammers’ blue tick bonanza – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Seized cryptocurrency is stolen from the DEA, blue-ticks are being exploited, a bath full of dollar bills, the comfort offered...
Japan’s cybersecurity agency admits it was hacked for months – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Japan’s National Center of Incident Readiness and Strategy for Cybersecurity (NISC), the agency responsible for the nation’s defences against cyber...
Recovering from a supply-chain attack: What are the lessons to learn from the 3CX hack? – Source:
Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 2
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 0
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 0
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 14
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 13
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 2
Hyperview Integrates RF Code Technology to Automate IT Asset Tracking – Source: securityboulevard.com
Source: securityboulevard.com – Author: Rajan Sodhi Leading DCIM software provider leverages RF Code CenterScape software to accurately capture and report on critical assets’ location and environmental...