Source: www.techrepublic.com – Author: Franklin Okeke Gone are the days when easy-to-memorize passwords such as “Ilovemycat36” sufficed. Nowadays, a long, heterogeneous mashup of characters, cases, numbers...
Day: August 30, 2023
Abnormal Security: Microsoft Tops List of Most-Impersonated Brands in Phishing Exploits – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Image: Timon/Adobe Stock A significant portion of social engineering attacks, such as phishing, involve cloaking a metaphorical wolf in sheep’s...
Legit Security and CrowdStrike: Securing Applications from Code Creation to Cloud Deployment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Noam Dotan Cloud environments and the applications running on them present an enormous attack surface that’s frequently exploited. Protecting runtime environments in...
Why Companies Should Invest in Cybersecurity During a Recession – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalie Anderson Economic downturns often trigger cost-cutting and layoffs. And while it may appear counterintuitive to advocate for new business investments, the...
When kids fly the nest, secure your digital nest eggs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog It’s a landmark shift when our children leave the house to begin their lives as adults. As they pick up...
BSides Cheltenham 2023 – David Abrutat – A Potted History Of British SIGINT – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
U.S. Hacks QakBot, Quietly Removes Botnet Infections – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs The U.S. government today announced a coordinated crackdown against QakBot, a complex malware family used by multiple cybercrime groups to lay...
LogRhythm Announces Partnership with Cimcor for Enhanced Cybersecurity Capabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riley-Ann Parker LogRhythm SIEM combined with CimTrak provides the ability to immediately detect and remediate threats across the enterprise BROOMFIELD, Colo., August...
SMS Toll Fraud Alert: Empowering Social Media Companies to Recover Millions in Stolen Revenue – Source: securityboulevard.com
Source: securityboulevard.com – Author: Arkose Labs SMS toll fraud is putting a severe financial burden on social media businesses, as cybercriminals exploit this communication channel for...
The Evolution of NDP: Finding Our Fit in the Technological Landscape – Source: securityboulevard.com
Source: securityboulevard.com – Author: Barrett Lyon The Evolution of NDP: Finding Our Fit in the Technological Landscape By Barrett Lyon, Co-Founder and Chief Architect As security...
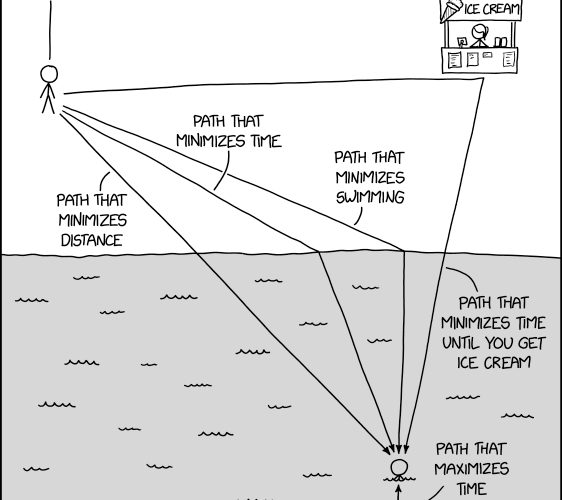
Randall Munroe’s XKCD ‘Path Minimization’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Yes, we have specific objectives for uptime and recovery Yes, we talk about resilience, but don’t have specific objectives It’s...
Did Russia Hack Poland’s Trains? MSM Says Yes, but … Well, You Decide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings It depends what you mean by “hack” (and by “Russia”). Trains all over Poland are mysteriously slamming on the brakes,...
Recovering from a supply-chain attack: What are the lessons to learn from the 3CX hack? – Source:
Source: – Author: 1 The campaign started with a trojanized version of unsupported financial software Original Post URL: Category & Tags: – Views: 2
How a Telegram bot helps scammers target victims – Week in security with Tony Anscombe – Source:
Source: – Author: 1 ESET researchers uncover a Telegram bot that enables even less tech-savvy scammers to defraud people out of their money Original Post URL:...
Telekopye: Hunting Mammoths using Telegram bot – Source:
Source: – Author: 1 Analysis of Telegram bot that helps cybercriminals scam people on online marketplaces Original Post URL: Category & Tags: – Views: 13
Scarabs colon-izing vulnerable servers – Source:
Source: – Author: 1 Analysis of Spacecolon, a toolset used to deploy Scarab ransomware on vulnerable servers, and its operators, CosmicBeetle Original Post URL: Category &...
A Bard’s Tale – how fake AI bots try to install malware – Source:
Source: – Author: 1 The AI race is on! It’s easy to lose track of the latest developments and possibilities, and yet everyone wants to see...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the event’s venue due to...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 18
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 13
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 1
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 16
Chinese Hackers Anticipated Barracuda ESG Patch – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Cybercrime , Cyberwarfare / Nation-State Attacks Threat Actor Deployed an Additional Backdoor to Select Targets David...
LIVE Webinar | How to Build an Impactful Business Case for a Defensible GRC Program – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Mohit Lal Mug Senior Director, Customer Success, SDG Corp Mohit leads the pre-sales & customer success functions for TruOps and works...
Ransomware Attack Cleanup Costs: $11M So Far for Rackspace – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Incident & Breach Response , Ransomware Fallout From Crypto-Locking Malware Attacks and Data Exfiltration Remains Costly...