Source: thehackernews.com – Author: . Aug 21, 2023THNVulnerability / Cyber Threat A high-severity security flaw has been disclosed in the WinRAR utility that could be potentially...
Day: August 21, 2023
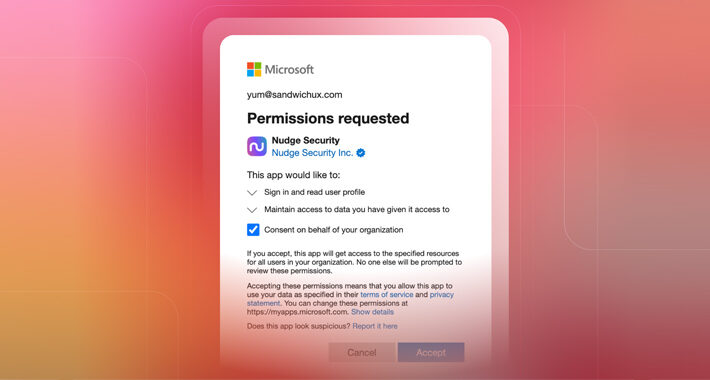
How to Investigate an OAuth Grant for Suspicious Activity or Overly Permissive Scopes – Source:thehackernews.com
Source: thehackernews.com – Author: . From a user’s perspective, OAuth works like magic. In just a few keystrokes, you can whisk through the account creation process...
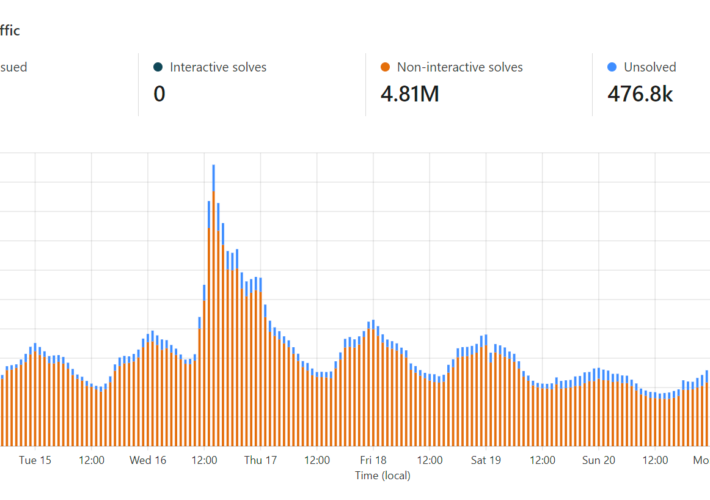
Fighting API Bots with Cloudflare’s Invisible Turnstile – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt There’s a “hidden” API on HIBP. Well, it’s not “hidden” insofar as it’s easily discoverable if you watch the network...
Generative AI Is Scraping Your Data. So, Now What? – Source: www.darkreading.com
Source: www.darkreading.com – Author: Benjamin Fabre, Co-Founder & CEO, DataDome There’s no denying ChatGPT and other generative AI models are a double-edged sword: While they can...
DEF CON’s AI Village Pits Hackers Against LLMs to Find Flaws – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading DEF CON 2023 — Las Vegas — DEF CON’s most buzzed-about event, the AI Village, let thousands...
Visibility Is Just Not Enough to Secure Operational Technology Systems – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 For anyone new to securing an operational technology (OT) network or industrial control systems (ICS) from cyber threats, gaining full visibility...
Hands on with Windows 11’s ‘never combine’ taskbar feature – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Windows 11, already a monumental shift in design from its predecessor, continues to evolve. In its upcoming 23H2 release slated for...
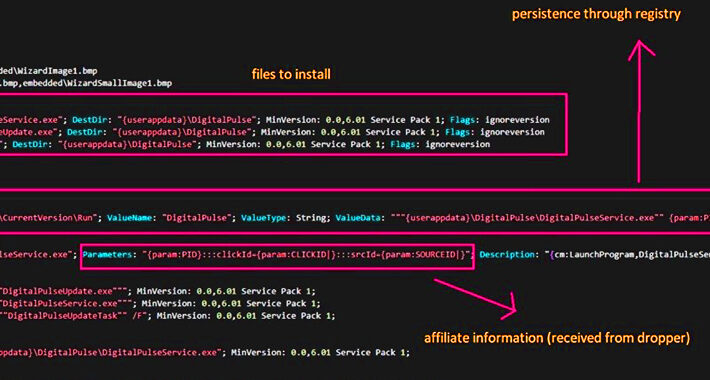
This Malware Turned Thousands of Hacked Windows and macOS PCs into Proxy Servers – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 21, 2023THNMalware / Privacy Threat actors are leveraging access to malware-infected Windows and macOS machines to deliver a proxy server...
HiatusRAT Malware Resurfaces: Taiwan Firms and U.S. Military Under Attack – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 21, 2023THNCyber Threat / Malware The threat actors behind the HiatusRAT malware have returned from their hiatus with a new...
Evacuation of 30,000 hackers – Week in security with Tony Anscombe – Source:
Source: – Author: 1 DEF CON, the annual hacker’s convention in Las Vegas, was interrupted on Saturday evening when authorities evacuated the convention due to a...
DEF CON 31: US DoD urges hackers to go and hack ‘AI’ – Source:
Source: – Author: 1 The limits of current AI need to be tested before we can rely on their output Original Post URL: Category & Tags:...
Mass-spreading campaign targeting Zimbra users – Source:
Source: – Author: 1 ESET researchers have observed a new phishing campaign targeting users of the Zimbra Collaboration email server. Original Post URL: Category & Tags:...
DEF CON 31: Robot vacuums may be doing more than they claim – Source:
Source: – Author: 1 When it comes to privacy, it remains complicated and near impossible for a consumer to make an informed decision. Original Post URL:...
Black Hat 2023: Hacking the police (at least their radios) – Source:
Source: – Author: 1 Hiding behind a black box and hoping no one will hack it has been routinely proven to be unwise and less secure....
Black Hat 2023: How AI changes the monetization of search – Source:
Source: – Author: 1 Search engines, AI, and monetization in the new era Original Post URL: Category & Tags: – Views: 12
Black Hat 2023: AI gets big defender prize money – Source:
Source: – Author: 1 Black Hat is big on AI this year, and for a good reason Original Post URL: Category & Tags: – Views: 3
Black Hat 2023: ‘Teenage’ AI not enough for cyberthreat intelligence – Source:
Source: – Author: 1 Current LLMs are just not mature enough for high-level tasks Original Post URL: Category & Tags: – Views: 2
20k security folks in the desert – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Unsurprisingly, artificial intelligence took the center stage at this year’s edition of Black Hat, one of the world’s largest gatherings of cybersecurity...
Black Hat 2023: Cyberwar fire-and-forget-me-not – Source:
Source: – Author: 1 What happens to cyberweapons after a cyberwar? Original Post URL: Category & Tags: – Views: 0
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....
Fingerprints all over: Can browser fingerprinting increase website security? – Source:
Source: – Author: 1 Browser fingerprinting is supposedly a more privacy-conscious tracking method, replacing personal information with more general data. But is it a valid promise?...
The grand theft of Jake Moore’s voice: The concept of a virtual kidnap – Source:
Source: – Author: 1 With powerful AI, it doesn’t take much to fake a person virtually, and while there are some limitations, voice-cloning can have some...
N. Korean Kimsuky APT targets S. Korea-US military exercises – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini North Korea-linked APT Kimsuky launched a spear-phishing campaign targeting US contractors working at the war simulation centre. North Korea-linked APT...
Four Juniper Junos OS flaws can be chained to remotely hack devices – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Juniper Networks addressed multiple flaws in the J-Web component of Junos OS that could be chained to achieve remote code...
Security Affairs newsletter Round 433 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Cybersecurity: CASB vs SASE – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Understanding cybersecurity aspects addressed by Cloud Access Security Broker (CASB) and Secure Access Service Edge (SASE) In an increasingly digital...
Suspected N. Korean Hackers Target S. Korea-US Drills – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP Suspected North Korean hackers have attempted an attack targeting a major joint military exercise between Seoul and Washington that starts on...
BSidesTLV 2023 – Paz Hameiri – Barcode Scanners Are Disguised Windows To Your Windows – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...