Source: www.darkreading.com – Author: 1 COOKEVILLE, Tenn., Aug. 14, 2023 /PRNewswire-PRWeb/ — Women in CyberSecurity (WiCyS) is hosting its next Virtual Career Fair on Wednesday, Aug. 16, 11 a.m.- 5 p.m. CT, which is...
Day: August 14, 2023
Phishing Operators Make Ready Use of Abandoned Websites for Bait – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Attackers are increasingly targeting abandoned and barely maintained websites for hosting phishing pages, according to a...
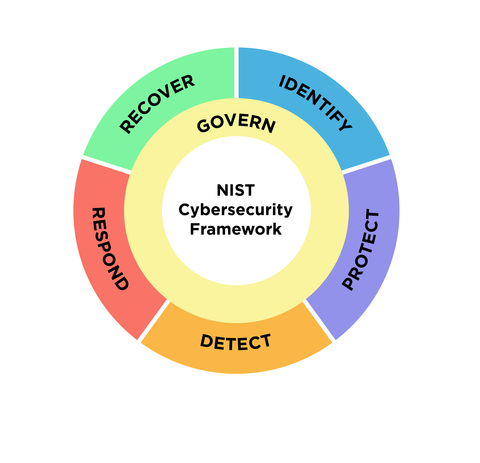
What’s New in the NIST Cybersecurity Framework 2.0 – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading First introduced nearly a decade ago as technical cybersecurity guidance for critical infrastructure interests like energy, banking,...
Russian-African Security Gathering Exposes Kremlin’s Reduced Influence – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Heads of government from the Russian Federation and African states, along with representatives from the African Union and Africa’s integration...
Health Data of 4M Stolen in Cl0p MOVEit Breach of Colorado Department – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A government department in Colorado is the latest victim of a third-party attack by Russia’s Cl0p ransomware...
Following Pushback, Zoom Says It Won’t Use Customer Data to Train AI Models – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Zoom says it will walk back a recent change to its terms of service that allowed...
Lock Down APIs to Prevent Breaches – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Web and mobile application developers need to take more care in creating secure applications, as attackers...
Interpol Shuts Down Phishing Service ’16shops’ – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Three individuals in Indonesia and Japan were arrested for their alleged roles in “16shop,” a notorious phishing-as-a-service...
7 Reasons People Don’t Understand What You Tell Them – Source: www.darkreading.com
Source: www.darkreading.com – Author: Joshua Goldfarb, Security and Fraud Architect, F5 I’ve been fascinated by the difference between what one person writes, says, or does and...
5 Ways CISA Can Help Cyber-Poor Small Businesses & Local Governments – Source: www.darkreading.com
Source: www.darkreading.com – Author: Kevin O’Connor, Director of Threat Research, Adlumin For far too long, the cybersecurity industry has primarily focused on protecting the largest organizations...
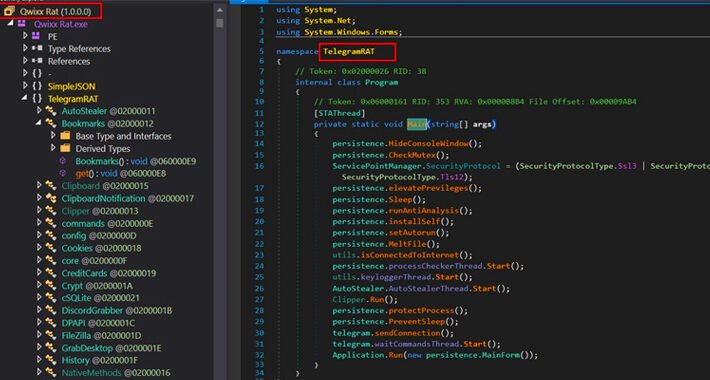
QwixxRAT: New Remote Access Trojan Emerges via Telegram and Discord – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 14, 2023THNCyber Threat / Malware A new remote access trojan (RAT) called QwixxRAT is being advertised for sale by its...
Ongoing Xurum Attacks on E-commerce Sites Exploiting Critical Magento 2 Vulnerability – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 14, 2023THNWebsite Security / Vulnerability E-commerce sites using Adobe’s Magento 2 software are the target of an ongoing campaign that...
Identity Threat Detection and Response: Rips in Your Identity Fabric – Source:thehackernews.com
Source: thehackernews.com – Author: . Why SaaS Security Is a Challenge In today’s digital landscape, organizations are increasingly relying on Software-as-a-Service (SaaS) applications to drive their...
Charming Kitten Targets Iranian Dissidents with Advanced Cyber Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 14, 2023THNCyber Espionage Germany’s Federal Office for the Protection of the Constitution (BfV) has warned of cyber attacks targeting Iranian...
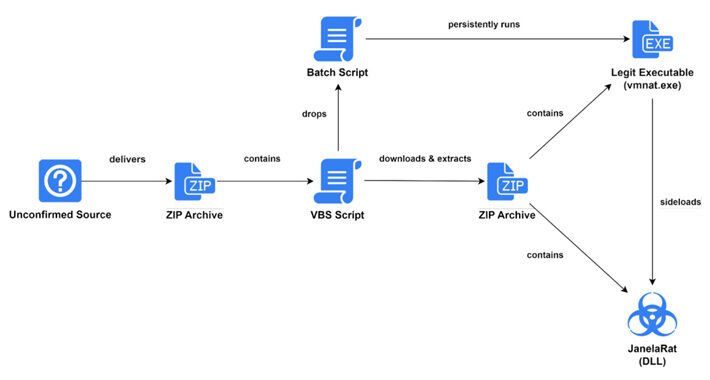
New Financial Malware ‘JanelaRAT’ Targets Latin American Users – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 14, 2023THNMalware / Cyber Threat Users in Latin America (LATAM) are the target of a financial malware called JanelaRAT that’s...
What is a ‘purple team’ in cyber security? (2023) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: A purple team provides a critical lens through which organizations can see how to elevate their cyber security. But...
News alert: Fireblocks uncovers vulnerabilities impacting dozens of major wallet providers – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido New York, N.Y., Aug.9, 2023 – Today, the Fireblocks Cryptography Research Team announced the findings of multiple zero-day vulnerabilities in some...
News Alert: GhangorCloud selected to demo Deep AI-based capabilities at India’s G20 Summit – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido San Jose, Calif., Aug. 7, 2023 – GhangorCloud, a leading provider of Deep AI-based information security and data privacy compliance enforcement...
Alberta Dental Services Security Breach Exposes 1.47M Records – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Alberta Dental Service Corporation (ADSC) has revealed that nearly 1.47 million individuals have been affected by a data breach that occurred...
Several Flaws Found in CyberPower and Dataprobe Products – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A series of security vulnerabilities have been discovered in CyberPower’s PowerPanel Enterprise Data Center Infrastructure Management (DCIM) platform and Dataprobe’s iBoot...
Security Researchers Publish Gigabud Banking Malware Analysis – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity researchers have published a new analysis of the elusive Gigabud banking malware. Originating as an Android Remote Access Trojan (RAT),...
Cumbria Police accidentally publish officers’ names and salaries online – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley ‘Ello ello ello. What’s all this then? Just days after it was learned that the police had exposed the details...
How to hack casino card-shuffling machines – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Security researchers have demonstrated how they were able to exploit a flaw which allowed them to hack the card-shuffling devices...
Ongoing Xurum attacks target Magento 2 e-stores – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of ongoing attacks, dubbed Xurum, targeting e-commerce websites using Adobe’s Magento 2 CMS. Akamai researchers warn of ongoing...
Colorado HCPF Department notifies 4 million individuals after IBM MOVEit breach – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Colorado Department of Health Care Policy & Financing (HCPF) disclose a data breach after MOVEit attack on IBM. The...
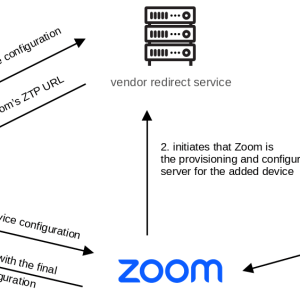
Experts found multiple flaws in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP) – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple flaws in AudioCodes desk phones and Zoom’s Zero Touch Provisioning (ZTP) can expose to several attacks. Researchers from security...
Nine flaws in CyberPower and Dataprobe solutions expose data centers to hacking – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Multiple vulnerabilities in CyberPower PowerPanel Enterprise DCIM platform and Dataprobe PDU could expose data centers to hacking. Researchers from Trellix...
MoustachedBouncer: Espionage against foreign diplomats in Belarus – Source:
Source: – Author: 1 Long-term espionage against diplomats, leveraging email-based C&C protocols, C++ modular backdoors, and adversary-in-the-middle (AitM) attacks… Sounds like the infamous Turla? Think again!...
Time is money, and online game scammers have lots of it – Source:
Source: – Author: 1 Gamers and cybersecurity professionals have something in common – the ever-terrible presence of hacking, scams, and data theft – but how and...
Check cybersecurity pre-invest – Week in security with Tony Anscombe – Source:
Source: – Author: 1 When you invest in a company, do you check its cybersecurity? The U.S. Securities and Exchange Commission has adopted new cybersecurity rules....