Source: securityaffairs.com – Author: Pierluigi Paganini Wiz researchers discovered two Linux vulnerabilities in the Ubuntu kernel that can allow an unprivileged local user to gain elevated...
Month: July 2023
How scammers used SEO to disguise themselves as an electric utility – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog Summer is at its height, and it’s a good time to go sit by the pool with a glass of...
Redefining Security: Going Beyond Compliance in Financial Organizations (Plus Memes!) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team Organizations often confuse the concept of being compliant with being secure. They assume that they must be appropriately protected once...
BSides Leeds 2023 – Peter Jones – Practical Blue Teaming – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Netography: Getting Beyond the ‘Black Box’ Approach to DDoS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Martin Roesch Netography: Getting Beyond the ‘Black Box’ Approach to DDoS By Martin Roesch, CEO According to the Verizon 2023 Data Breach...
Randall Munroe’s XKCD ‘Bad Map Projection: ABS (Longitude)’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Growing AI-powered fraud highlights the need for advanced fraud detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team In the six months since ChatGPT launched in November 2022, nearly half of consumers admitted to finding...
More malicious npm packages found in wake of JumpCloud supply chain hack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Roberts Two weeks after the IT management firm JumpCloud announced that it was the victim of a supply chain attack aimed...
A Fraud Risk Management Guide for Savvy Businesses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Arkose Labs Fraud is a pervasive threat to any organization’s viability and sustainability, with fraudsters continually seeking innovative ways to deceive and...
Supply Chain and Firmware Security Take Center Stage in 2024 NDAA – Source: securityboulevard.com
Source: securityboulevard.com – Author: Chris Garland Every year, Congress passes the National Defense Authorization Act (NDAA), which sets the budget and defines key policy priorities for...
The Week in Security: North Korean APT targets developers, this Barbie is a cybercriminal – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kate Tenerowicz Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world...
Moscow Court Convicts Former Group-IB Chief for Treason – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , IT Risk Management Ilya Sachkov Sentenced to 14 Years in Prison Mihir Bagwe (MihirBagwe) • July...
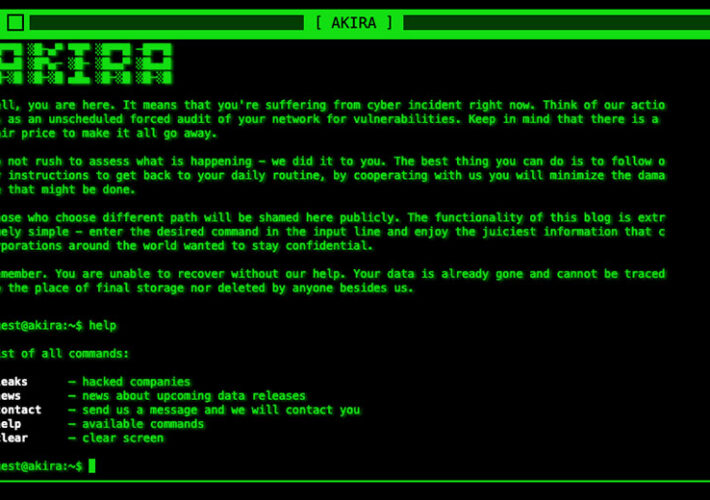
Are Akira Ransomware’s Crypto-Locking Malware Days Numbered? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Ransomware Ransomware-Building Group Lost Royal-Organized Competition, Researchers Say Mathew J. Schwartz (euroinfosec) • July 27, 2023...
Coro Buys Privatise to Infuse SASE With Network Connectivity – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , SASE , Security Operations Privatise Will Add DNS Filtering, Content Filtering, ZTNA to Coro’s SASE Platform...
Phishing Scam Affects Nearly 170K Henry Ford Health Patients – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Email Threat Protection , Fraud Management & Cybercrime , Healthcare Academic Medical Provider Says 3 Employee Email Accounts Were Compromised Marianne...
Breach Roundup: Zenbleed Flaw Exposes AMD Ryzen CPUs – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Incident & Breach Response , Security Operations Wuhan Earthquake Monitoring Center Suffers Cyberattack; NATO’s COI Portal Breached Anviksha More (AnvikshaMore) •...
Security Incident Impacts CardioComm’s Operations – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 CardioComm Solutions, a Canadian medical provider of consumer heart monitoring and medical ECG software solutions, has disclosed a cybersecurity incident on...
High Severity Vulnerabilities Discovered in Ninja Forms Plugin – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Multiple high-severity vulnerabilities have been discovered in Ninja Forms, a popular forms builder plugin for WordPress with over 900,000 active installations....
China’s Wuhan Earthquake Center Suffers Cyber-Attack – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Wuhan Earthquake Monitoring Center in China has been hit by a cyber-incident perpetuated by a hacker group with an “overseas...
“Mysterious Elephant” Emerges, Kaspersky Reports – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new malicious actor known as “Mysterious Elephant” operating in the Asia-Pacific region has emerged in the threat landscape in the second...
OpenAI, Microsoft, Google and Anthropic Form Body to Regulate AI – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 You may have heard Sam Altman, the man behind ChatGPT, call for the regulation of future AI models while at the...
NCSC Publishes New Guidance on Shadow IT – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The UK’s leading cybersecurity agency has released new guidance for system owners and technical staff on how to manage shadow IT...
Supply Chain Attack Hits NHS Ambulance Trusts – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A cyber-attack on an NHS supplier has left two ambulance trusts serving millions of people without access to electronic patient records,...
SEC Wants Cyber-Incident Disclosure Within Four Days – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The US Securities and Exchange Commission (SEC) has adopted new rules requiring publicly listed firms to disclose serious incidents within four...
GameOver(lay): Two Severe Linux Vulnerabilities Impact 40% of Ubuntu Users – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 27, 2023THNLinux / Endpoint Security Cybersecurity researchers have disclosed two high-severity security flaws in the Ubuntu kernel that could pave...
New Malvertising Campaign Distributing Trojanized IT Tools via Google and Bing Search Ads – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 27, 2023THNMalvertising / Software Security A new malvertising campaign has been observed leveraging ads on Google Search and Bing to...
4 Most Dangerous and Destructive Ransomware Groups of 2022 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Lance Whitney Image: nicescene/Adobe Stock 2022 marked another year in which ransomware proved to be one of the most pernicious cyberthreats around...
Get 8 Months of Live Cyber Security Training for Under $500 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy on July 25, 2023, 1:33 PM EDT Get 8 Months of Live Cyber Security Training for Under $500 If you’re...
Checklist: Securing Digital Information – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Digital information is generally the lifeblood of any given organization, containing essential company data needed to run the business. Paperless offices have...
BreachForums database and private chats for sale in hacker data breach – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams While consumers are usually the ones worried about their information being exposed in data breaches, it’s now the hacker’s turn,...