Source: securityaffairs.com – Author: Pierluigi Paganini Researchers spotted a new Windows information stealer called Meduza Stealer, the authors employ sophisticated marketing strategies to promote it. The Meduza...
Month: July 2023
Experts detected a new variant of North Korea-linked RUSTBUCKET macOS malware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers spotted a new version of the RustBucket Apple macOS malware that supports enhanced capabilities. Researchers from the Elastic Security...
How to add the Docker Scout feature to the Docker CLI – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Jack Wallen on July 3, 2023, 9:38 AM EDT How to add the Docker Scout feature to the Docker CLI In this...
IT Physical Security Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy will help your organization safeguard its hardware, software and data from exposure to persons (internal or external) who could intentionally...
Celebrating Arkose Labs’ Net Promoter Score of 100 for Q2 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Patrice Boffa A Testament to Our Customer Success Team’s Dedication We are thrilled to announce that Arkose Labs has achieved an exceptional...
BSidesSF 2023 – Nika Korchok Wakulich – MTV Reboot — My Super Sweet 16-Bit Malware ~ *MS-DOS Edition* ~ [TSR Remix] – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
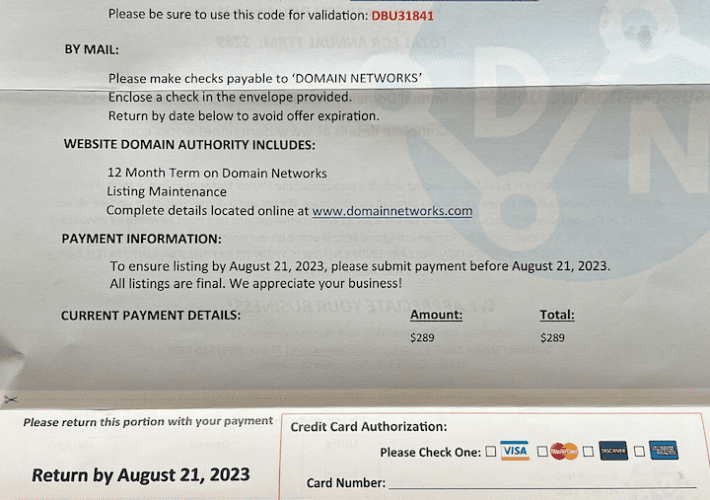
Who’s Behind the DomainNetworks Snail Mail Scam? – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs If you’ve ever owned a domain name, the chances are good that at some point you’ve received a snail mail letter...
Google To Replace the “Padlock Icon” with the “Tune Icon” in Chrome 117 Version – Source: securityboulevard.com
Source: securityboulevard.com – Author: SSLWiki Chrome’s “Padlock Icon” is to be replaced by “Tune Icon” in the Latest Version 117, According to Google Google recently announced...
How to Show the Efficiency of a Vulnerability Management Program – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michelle Ofir Geveye What is Vulnerability Management? Vulnerability management is a critical element of information security. With cyber-attacks and data breaches increasing...
Self-Driving Cars Are Surveillance Cameras on Wheels – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier Police are already using self-driving car footage as video evidence: While security cameras are commonplace in American cities, self-driving cars...
MOVEit Cyberattack, The Problem with Password Rotations, Military Alert on Free Smartwatches – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Eston Several major organizations, including British Airways and the BBC, fell victim to the recent MOVEit cyberattack. We discuss the alarming...
Choosing Between Self-Managed and Service-Based SSO Solutions: A Comprehensive Comparison – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta In today’s interconnected digital landscape, secure and seamless access to multiple applications and systems is crucial for organizations of all...
Massive Data Breach Affects UK Hospital Group – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The BlackCat ransomware group claims they have breached Barts Health NHS Trust and stolen seven terabytes of internal documents. On...
BlackCat Ransomware Gang to Launch Malicious WinSCP Ads – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Andreea Chebac The BlackCat ransomware group launched a malvertising campaign to push Cobalt Strike. They put up advertisements to attract people to...
What Is a Managed Security Service Provider (MSSP)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici In today’s digital landscape, businesses face an ever-increasing array of cybersecurity threats. Protecting sensitive data and infrastructure from malicious actors...
Understanding Managed SIEM: Empowering Businesses with Proactive Security – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian Organizations face an ongoing battle to protect their sensitive data and critical infrastructure in today’s increasingly sophisticated digital world. Security...
Shielding Learning: The Power of Cybersecurity in Education – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu As schools and universities continue to rely heavily on technology, the risk of cyberattacks becomes increasingly alarming. With hackers getting...
New Malware Alert: EarlyRAT Linked to North Korean Hacking Group – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu A previously undocumented remote access trojan (RAT) has been discovered by security analysts. Dubbed ‘EarlyRAT’, the trojan is believed to...
New Proxyjacking Campaign: Cybercriminals Hijack Vulnerable SSH Servers – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu A new financially motivated campaign is actively targeting vulnerable SSH servers to covertly ensnare them in a proxy network. According...
Verizon 2023 DBIR: What’s new this year and top takeaways for SMBs – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster Here are some of the key insights on the evolving data breach landscape as revealed by Verizon’s analysis of more...
TSMC Targeted by LockBit via Supplier Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A supply chain attack is the likely cause of Taiwanese giant chipmaker TSMC finding itself on the infamous ransomware group LockBit’s...
Croydon Council Hit With Enforcement Notice For FOI Fail – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A London borough council could be found in contempt of court if it fails to address serious data compliance issues, according...
International Police Operation Dismantles Phone Scam Network – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A multi-national policing operation has led to the arrest of dozens of suspects including the alleged boss of an organized crime...
Musk Losing Battle of Bad Bots as Rate Limits Begin – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Twitter’s problem with bad bots appears to be getting worse, despite owner Elon Musk’s assurances when he bought the platform that...
Improve Your Security WordPress Spam Protection With CleanTalk Anti-Spam – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 03, 2023The Hacker NewsWebsite Security Tool Every website owner or webmaster grapples with the issue of spam on their website...
CISA Flags 8 Actively Exploited Flaws in Samsung and D-Link Devices – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 03, 2023Ravie LakshmananMobile Security / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has placed a set of...
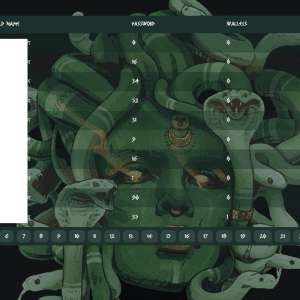
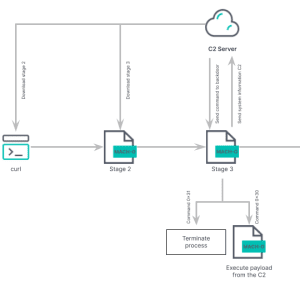
Evasive Meduza Stealer Targets 19 Password Managers and 76 Crypto Wallets – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 03, 2023Ravie LakshmananMalware / Hacking In yet another sign of a lucrative crimeware-as-a-service (CaaS) ecosystem, cybersecurity researchers have discovered a...
BlackCat Operators Distributing Ransomware Disguised as WinSCP via Malvertising – Source:thehackernews.com
Source: thehackernews.com – Author: . Threat actors associated with the BlackCat ransomware have been observed employing malvertising tricks to distribute rogue installers of the WinSCP file...
Architecting XDR to Save Money and Your SOC’s Sanity – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 The cyber security operation center (SOC) model’s focus has shifted to extended detection and response (XDR). Architected correctly, XDR puts less...
Security Affairs newsletter Round 426 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...



![bsidessf-2023-–-nika-korchok-wakulich-–-mtv-reboot-—-my-super-sweet-16-bit-malware-~-*ms-dos-edition*-~-[tsr-remix]-–-source:-securityboulevard.com](https://ciso2ciso.com/wp-content/uploads/2023/07/67876/bsidessf-2023-nika-korchok-wakulich-mtv-reboot-my-super-sweet-16-bit-malware-ms-dos-edition-tsr-remix-source-securityboulevard-com-710x500.jpg)