Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Month: July 2023
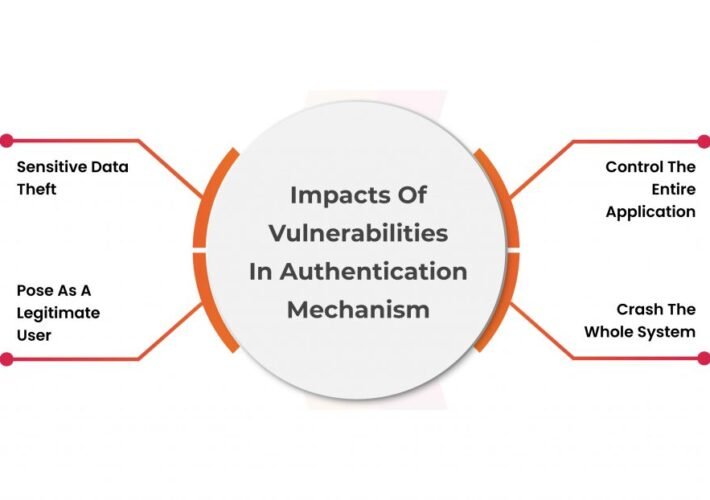
Bypass Vulnerability in WordPress Plugins Authentication – Source: securityboulevard.com
Source: securityboulevard.com – Author: Riddika Grover Authentication bypass vulnerability is a security defect that enables a threat actor to circumvent or bypass the authentication process of...
Looking ahead of CEA guidelines to secure the power sector in India – Source: securityboulevard.com
Source: securityboulevard.com – Author: Prayukth K V Looking ahead of CEA guidelines to secure the power sector in India – Sectrio India’s Central Electricity Authority (CEA)...
Verifiable Credentials: Revolutionizing Digital Identity Verification – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author The digital age has transformed numerous aspects of everyday life, from shopping and banking to...
Is It Safe To Text Social Security Numbers? 10 SSN Safety Tips – Source: securityboulevard.com
Source: securityboulevard.com – Author: ReasonLabs Your social security number (SSN) is one of the most crucial pieces of personal information you possess. It serves as a...
What is a Data Protection Strategy? Components, Best Practices and Benefits – Source: securityboulevard.com
Source: securityboulevard.com – Author: Spanning Cloud Apps Due to the increased shift to a hybrid business model in recent times, the world is witnessing an unprecedented surge...
BSidesSF 2023 – Naveen Srinivasan, Brian Russell – How Do You Trust Your Open Source Software? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Information Security Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: This policy from TechRepublic Premium provides guidelines to safeguard company information, reduce business and legal risks and protect company investments and reputation....
The State of Security 2023 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Cyberattacks continue to grow in quantity and sophistication at the same time that organizations’ systems become increasingly complex. Security teams, as always,...
Deepfaking it: What to know about deepfake‑driven sextortion schemes – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns...
Google Analytics data transfer to U.S. brings $1 million fine to Swedish firms – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Swedish Authority for Privacy Protection (Integritetsskyddsmyndigheten – IMY) has fined two companies with 12.3 million SEK (€1 million/$1.1 million)...
New Python tool checks NPM packages for manifest confusion issues – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A security researcher and system administrator has developed a tool that can help users check for manifest mismatches in packages...
How artificial intelligence is revolutionizing cyber security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In recent years, artificial intelligence (AI) has become one of the most sure-fire and strategic tools available for cyber...
Fortanix Builds Hardware Security Wall Around Plaintext Search – Source: www.darkreading.com
Source: www.darkreading.com – Author: Agam Shah, Contributing Writer Fortanix is bringing hardware security technology to database search with Confidential Data Search, with the goal to help...
OT Assets High Priority for Security Leaders as Industrial Threats Loom – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Industrial control systems (ICS) are an increasingly attractive target for cyber-attacks. Despite the threat, a recent report has found that security...
Thirty-three US Hospitals Hit By Ransomware This Year – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 At least 19 US healthcare organizations (HCOs) have been breached by ransomware gangs so far this year, according to Emsisoft. Brett Callow,...
Four Men Face 20 Years For Money Laundering Charges – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Four US residents have been charged with laundering funds from a variety of fraud schemes during the pandemic, by purchasing cars...
Microsoft Denies Major 30 Million Customer-Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Microsoft has hit back at claims from a shadowy hacktivist outfit that it managed to breach the company and obtain account...
How to Identify Phishing Emails and Prevent an Attack Using DNS Filtering – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Identifying phishing emails and preventing phishing attacks continue to raise serious challenges for any company’s IT team. Although it`s been...
What Is a Managed Security Service Provider (MSSP)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici In today’s digital landscape, businesses face an ever-increasing array of cybersecurity threats. Protecting sensitive data and infrastructure from malicious actors...
Cloudy, With a Chance of Cyber Risk – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Cloud Security , Governance & Risk Management Cloud Adoption in Financial Services has Soared – as...
Who Should Pay for Payment Scams – Banks, Telcos, Big Tech? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Finance & Banking , Fraud Management & Cybercrime , Industry Specific Making the Case for Penalizing Social Media Firms for Authorized...
Dutch Critical OT Systems Vulnerable to Hacks – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Operational Technology (OT) Hackers Could Exploit Inherent Vulnerabilities in OT Systems, Dutch...
CISA’s New ‘CyberSentry’ Program to Tighten ICS Security – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Critical Infrastructure Security , Governance & Risk Management , Government Program to Monitor IT, OT Networks of Enrolled Critical Infrastructure Partners...
Lumu, ExtraHop Lead Network Analysis, Visibility: Forrester – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , Network Detection & Response , Next-Generation Technologies & Secure Development Arista, Trend Micro Earn High Marks...
The Password Game – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I’ve been writing...
Self-Driving Cars Are Surveillance Cameras on Wheels – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Police are already using self-driving car footage as video evidence: While security cameras are commonplace in American cities, self-driving cars...
Dublin Airport staff pay details stolen by hackers after MOVEit attack at third-party provider Aon – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Just a moment… Enable JavaScript and cookies to continue Original Post URL: https://www.bitdefender.com/blog/hotforsecurity/dublin-airport-staff-pay-details-stolen-by-hackers-after-moveit-attack-at-third-party-provider/ Category & Tags: Data loss,Vulnerability,airport,data breach,Dublin,Ireland,MOVEit,vulnerability –...
Cloudy, With a Chance of Cyber Risk – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 3rd Party Risk Management , Cloud Security , Governance & Risk Management Cloud Adoption in Financial Services has Soared – as...
Who Should Pay for Payment Scams – Banks, Telcos, Big Tech? – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Finance & Banking , Fraud Management & Cybercrime , Industry Specific Making the Case for Penalizing Social Media Firms for Authorized...