Source: www.darkreading.com – Author: 1 SAN FRANCISCO, July 6, 2023 — Black Hat, the producer of the cybersecurity industry’s most established and in-depth security events, today announced Maria...
Month: July 2023
StackRot Linux Kernel Bug Has Exploit Code on the Way – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jai Vijayan, Contributing Writer, Dark Reading Exploit code will soon become available for a critical vulnerability in the Linux kernel that a...
Patchless Cisco Flaw Breaks Cloud Encryption for ACI Traffic – Source: www.darkreading.com
Source: www.darkreading.com – Author: Becky Bracken, Editor, Dark Reading Cisco has announced that a high-severity flaw in its data center switching gear could allow threat actors...
Shell Becomes Latest Cl0p MOVEit Victim – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Shell, the multinational oil and gas company, has confirmed that it is the victim of a MOVEit hack, revealing...
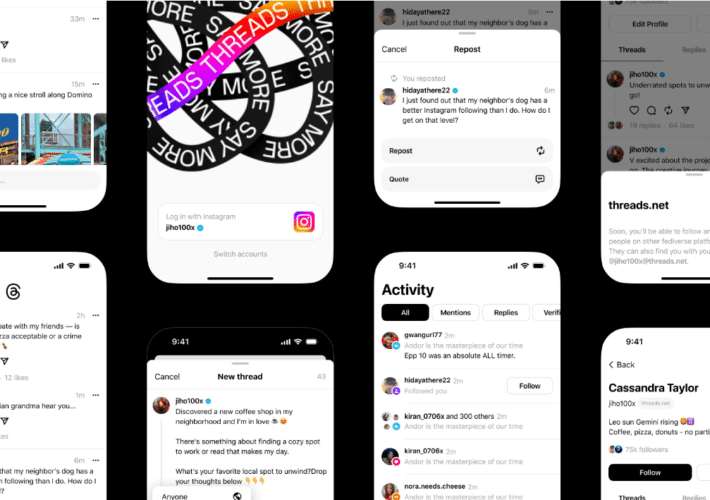
Privacy Woes Hold Up Global Instagram Threads Launch – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading A full 20 million people (and counting) had signed up for Meta’s Twitter competitor within...
Cybersecurity’s Future Hinges on Stronger Public-Private Partnerships – Source: www.darkreading.com
Source: www.darkreading.com – Author: Seth Boro, Managing Partner, ThomaBravo As a managing partner investing in cybersecurity at Thoma Bravo, “diplomacy” in my world is usually limited...
CISOs Find ‘Business as Usual’ Shows the Harsh Realities of Cyber-Risk – Source: www.darkreading.com
Source: www.darkreading.com – Author: Ryan Kalember, Executive Vice President of Cybersecurity Strategy, Proofpoint With the chaos of the pandemic now in the rearview mirror, we are...
Botnets Send Exploits Within Days to Weeks After Published PoC – Source: www.darkreading.com
Source: www.darkreading.com – Author: Robert Lemos, Contributing Writer, Dark Reading Attackers quickly turn around real-world attacks using proof-of-concept code, taking only days to weeks to create...
6 Steps To Outsmart Business Email Compromise Scammers – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Last year the FBI registered over 21,000 complaints about business email fraud, with adjusted losses of over $2.7 billion. Today...
What’s up with Emotet? – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Jakub Kaloč A brief summary of what happened with Emotet since its comeback in November 2021 Emotet is a malware family active...
Anonymous Sudan Or Anonymous Russia? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avivit Anonymous Sudan gained notoriety with its distributed denial of service (DDoS) attacks, targeting Microsoft in June. Earlier this year, the group...
AppSecCon 2023 is Now On Demand – Source: securityboulevard.com
Source: securityboulevard.com – Author: Raj Patil In 2011, Marc Andreessen famously told the Wall Street Journal that “software is eating the world.” Today, that has never...
SAP Remote Function Call (RFC) Vulnerabilities in 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: ltabo SAP Remote Function Call (RFC) Vulnerabilities in 2023 ltabo Thu, 07/06/2023 – 13:44 In 2007, Onapsis CEO & Co-founder Mariano Nuñez...
Using Machine Learning to Find Vulnerabilities and Prevent Cyberattacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Juras Juršėnas When it comes to cybersecurity, organizations are constantly looking for new ways to improve their defenses. A promising area of...
Email Security Awareness Training – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cofense “To err is human” is as true today as it was when Alexander Pope penned the words over 300 years ago....
Digital smugglers: How attackers use HTML smuggling techniques to beat traditional security defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Neko Papez It’s hard to imagine a time when the web browser wasn’t the critical enterprise productivity app. Many enterprise workers born...
AI in the SOC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sue Poremba Is there a more talked about topic than AI right now? Generative AI took the world by storm when ChatGPT...
Operation Brainleeches: Malicious npm packages fuel supply chain and phishing attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lucija Valentić Executive Summary ReversingLabs researchers recently discovered more than a dozen malicious packages published to the npm open source repository that...
Substantive Testing vs. Control Testing: Unveiling the Difference – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michelle Ofir Geveye The goal of audit testing procedures in financial reporting is to gather enough relevant evidence to reasonably establish the...
EU court orders Meta to change data collection practices – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: On Tuesday, a ruling from the European Union’s Court of Justice (CJEU) upheld a 2019 anti-trust authority ruling from...
News Alert: Nuvoton underscores its commitment to 8-bit MCU production sustainability – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Hsinchu, Taiwan – July 6, 2023 – Nuvoton Technology, one of the world’s leading suppliers of microcontrollers, has proudly launched its...
News Alert: Swissbit introduces small-capacity memory for IIoT, smart city applications – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Westford, Mass., June 27, 2023 – The industry is vying for ever-increasing gigabyte capacities. And yet there are countless applications that...
Belgian Tax Hack – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Belgian Tax Hack Here’s a fascinating tax hack from Belgium (listen to the details here, episode #484 of “No...
Ongoing Incident Prompts JumpCloud to Reset API Keys – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 In response to an ongoing incident, JumpCloud has reset the admin Application Programming Interface (API) keys for affected customers. In a...
Cisco Enterprise Switch Flaw Exposes Encrypted Traffic – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A critical security flaw has been discovered in the Cisco Application Centric Infrastructure (ACI) Multi-Site CloudSec encryption feature, potentially allowing hackers...
Unpatched SolarView Systems Vulnerable to Exploits – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers at VulnCheck have highlighted the exploitation of vulnerabilities in the SolarView Series, an industrial control systems (ICS) hardware widely...
Human Error the Leading Cause of Cloud Data Breaches – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Around two in five (39%) businesses experienced a data breach in their cloud environment in 2022, a rise of 4% compared...
Experts Warn of Impending TeamTNT Docker Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers have warned that the infamous TeamTNT group could be preparing a significant new campaign against cloud-native environments, after spotting...
Police Arrest Suspected OPERA1ER Cybercrime Kingpin – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Police have announced the arrest of an individual they believe to be a key figure in a prolific cybercrime group which...
Suspicious Email Reports Up a Third as NCSC Hails Active Defense – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading UK cybersecurity agency has hailed continued progress with its flagship initiative, designed to make the country the safest place...