Source: www.securityweek.com – Author: Eduard Kovacs Industrial giant Honeywell wants to extend its operational technology (OT) cybersecurity portfolio with the acquisition of Tel Aviv, Israel-based OT...
Month: July 2023
PoC Exploit Published for Recent Ubiquiti EdgeRouter Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A recently patched vulnerability in Ubiquiti EdgeRouter and AirCube devices could be exploited to execute arbitrary code, vulnerability reporting firm...
Critical Vulnerability Can Allow Takeover of Mastodon Servers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A critical vulnerability in the decentralized social networking platform Mastodon could be exploited to take over servers. The issue was...
StackRot: Linux Bug so bad Linus Dives Into Code to Fix It – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Torvalds feels the pressure, fixes lazy locks. A critical vulnerability in the Linux kernel caused Linus Torvalds (pictured) to get...
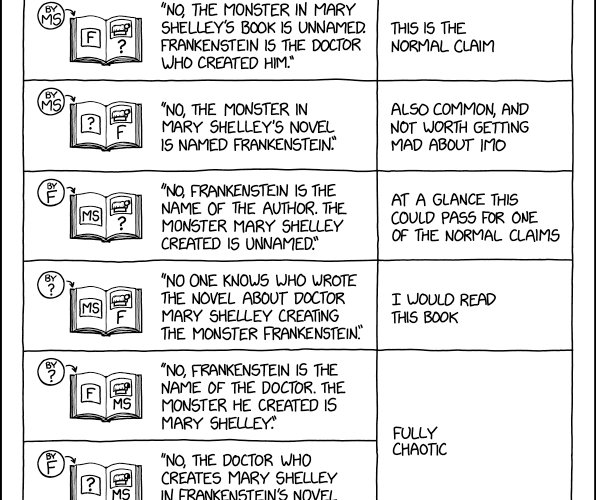
Randall Munroe’s XKCD ‘Frankenstein Claim Permutations’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
BSides Knoxville 2023 – Omar Minawi – Client-Side JavaScript From Your Nightmares: Multi-Step XSS Attacks And Defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Navigating the Digital Landscape: A Guide for Young People on Managing Their Online Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author As the digital world continues to flourish, it is becoming increasingly crucial for young people...
Employee Spotlight – Joseph Pike – Source: securityboulevard.com
Source: securityboulevard.com – Author: Janice Sheridan We spoke to Security Analyst, Joseph Pike For this month’s employee spotlight piece, we spoke to Security Analyst and heavy...
Advanced Endpoint Protection (AEP): What Are the Options? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gilad David Maayan Advanced endpoint protection, often referred to as AEP, is a comprehensive cybersecurity solution designed to protect an organization’s endpoints,...
Finding the Right Tools for Response and Visibility in the SOC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sue Poremba One of the more difficult tasks for a cybersecurity professional—from the CISO to the person responsible for log management in...
Enhancing Financial Sector Security: IBM Cloud Security & Compliance Center and CyberSaint Collaborate to Streamline 3rd and 4th Party Risk Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Vivek Kinra and Jerry Layden We are thrilled to announce a strategic integration between IBM Cloud Security & Compliance Center and CyberSaint,...
Third-party risk management survey: Prioritize end-to-end software supply chain security — or fail – Source: securityboulevard.com
Source: securityboulevard.com – Author: John P. Mello Jr. Awareness of the risks posed by third-party vendors is high among organizations across industries, but visibility into those...
Crafting a Successful Cybersecurity Risk Management Strategy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michelle Ofir Geveye In a world where cyber risks lurk in the dark shadows of our networks, one thing is crystal clear....
Banking Firms Under Attack by Sophisticated ‘Toitoin’ Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A sophisticated and evasive malware campaign is targeting businesses in Latin America with a multi-stage attack that...
How to Use Log Management to Retrace Your Digital Footsteps – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Logs are like digital footprints or a letter that developers write to themselves for the future. They track every action or...
What Is Vendor Risk Management (VRM)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici In the ever-evolving and intricate realm of modern business, organizations rely heavily on various vendors and third-party partners to keep their...
Chrome’s big design refresh uses Microsoft Mica effect in custom themes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google is working on a significant design overhaul for Chrome across Windows, Mac, and Chromebook platforms. Named Chrome’s Material You-based,...
Charming Kitten hackers use new ‘NokNok’ malware for macOS – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers observed a new campaign they attribute to the Charming Kitten APT group where hackers used new NokNok malware that...
Windows Subsystem for Android gets July 2023 preview with new features – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Windows 11, with its Windows Subsystem for Android (WSA), allows users to access almost all popular Android apps directly from...
AMD releases Adrenalin 23.7.1 WHQL driver for Windows – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar After a long break, AMD has released a new graphics driver, Adrenalin 23.7.1 WHQL (driver version 23.10.01.45). The new driver...
Two spyware sending data of more than 1.5M users to China were found in Google Play Store – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Two apps on the Google Play Store with more than 1.5 million downloads have been discovered spying on users and...
Security Affairs newsletter Round 427 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
BSides Knoxville 2023 – Reanna Schultz – Social Engineering: Training The Human Firewall – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
New R Package For HTTP Headers Hashing – Source: securityboulevard.com
Source: securityboulevard.com – Author: hrbrmstr HTTP Headers Hashing (HHHash) is a technique developed by Alexandre Dulaunoy to generate a fingerprint of an HTTP server based on...
How to Combat Misinformation in the Age of AI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lohrmann on Cybersecurity Fake news, misinformation and online scams are growing at an alarming rate as generative AI explodes in usage. So...
Updated Truebot Malware Targeting Orgs in US, Canada – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Malware as-a-Service New Variant of Trojan Called Silence.Downloader Seen in May Prajeet Nair (@prajeetspeaks)...
Instagram’s Threads to get Twitter-like hashtags support, edit button and more – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Instagram’s dedicated text-sharing app, Threads, is set to introduce many new features, including Twitter-style hashtags, an edit button, a trending...
New ‘Big Head’ ransomware displays fake Windows update alert – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers have dissected a recently emerged ransomware strain named ‘Big Head’ that may be spreading through malvertising that promotes fake Windows...
Updated Truebot Malware Targeting Orgs in US, Canada – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Malware as-a-Service New Variant of Trojan Called Silence.Downloader Seen in May Prajeet Nair (@prajeetspeaks)...
Google addressed 3 actively exploited flaws in Android – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google released July security updates for Android that addressed tens of vulnerabilities, including three actively exploited flaws. July security updates...