Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The Storm-0558 breach that gave Chinese advanced persistent threat (APT) actors access to emails within...
Month: July 2023
White House, Big Tech Ink Commitments to Secure AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Seven leading tech companies — Google, Microsoft, Meta, Amazon, OpenAI, Anthropic, and Inflection — are meeting at...
Meet the Finalists for the 2023 Pwnie Awards – Source: www.darkreading.com
Source: www.darkreading.com – Author: Karen Spiegelman, Features Editor With Black Hat USA 2023 looming, it’s time to start thinking about the Oscars of cybersecurity, the Pwnie...
The Dark Side of AI – Source: www.darkreading.com
Source: www.darkreading.com – Author: Sam Crowther, Founder & CEO, Kasada New AI tools offer easier and faster ways for people to get their jobs done —...
Plurilock Announces Generative AI ‘Guardrails’ Product, PromptGuard – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Vancouver, British Columbia—(Newsfile Corp. – July 20, 2023) — Plurilock Security Inc. (TSXV: PLUR) (OTCQB: PLCKF) and related subsidiaries (“Plurilock” or...
CISA warns of attacks against Citrix NetScaler ADC and Gateway Devices – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The US CISA warns of cyber attacks targeting Citrix NetScaler Application Delivery Controller (ADC) and Gateway devices. The U.S. Cybersecurity...
Experts believe North Korea behind JumpCloud supply chain attack – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini SentinelOne researchers attribute the recent supply chain attacks on JumpCloud to North Korea-linked threat actors. JumpCloud is a cloud-based directory...
Nice Suzuki, sport: shame dealer left your data up for grabs – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cybernews research team discovered that two Suzuki-authorized dealer websites were leaking customers’ sensitive information. Suzuki or otherwise, buying a new...
JumpCloud Hackers Likely Targeting GitHub Accounts Too – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 3rd Party Risk Management , Cryptocurrency Fraud , Cyberwarfare / Nation-State Attacks Targets Include Blockchain, Crypto, Online Gambling and Cybersecurity Sectors...
ISMG Editors: Microsoft’s Move to Expand Logging Access – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime , Healthcare Also: ISMG’s Healthcare Summit and Emerging Trends, Challenges, New Tech...
Webinar | Graduating into a New Era: Cloud Security’s Biggest Challenges – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Florida Hospital Says Data Theft Attack Affects 1.2 Million – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Breach Notification , Fraud Management & Cybercrime , Ransomware Tampa General Hospital Says Incident Involved Thwarted Ransomware Encryption Attempt Marianne Kolbasuk...
7 Tech Firms Pledge to White House to Make AI Safe, Secure – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Artificial Intelligence & Machine Learning , Government , Industry Specific Microsoft, Google, Meta, Amazon Among Companies Making ‘Voluntary Commitments’ Marianne Kolbasuk...
Microsoft Cloud Hack Exposed More Than Exchange, Outlook Emails – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Researchers at cloud security startup Wiz have an urgent warning for organizations running Microsoft’s M365 platform: That stolen Microsoft Azure...
In Other News: Military Emails Leaked, Google Restricts Internet Access, Chinese Spyware – Source: www.securityweek.com
Source: www.securityweek.com – Author: SecurityWeek News SecurityWeek is publishing a weekly cybersecurity roundup that provides a concise compilation of noteworthy stories that might have slipped under...
Russia Seeks 18 Years in Jail for Founder of Cybersecurity Firm – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP A Russian prosecutor on Friday requested an 18-year prison sentence for Ilya Sachkov, founder of one of the country’s topcybersecurity firms,...
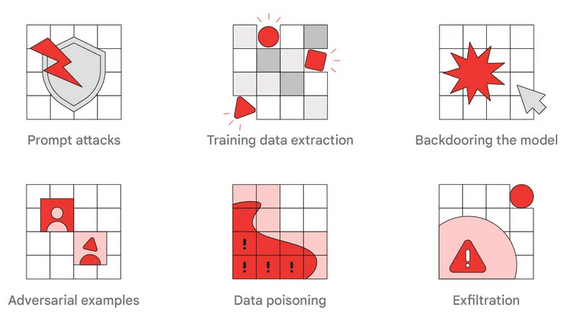
Google Creates Red Team to Test Attacks Against AI Systems – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Google has created a red team that focuses on artificial intelligence (AI) systems and it has published a report providing...
OpenMeetings Flaws Allow Hackers to Hijack Instances, Execute Code on Servers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Three vulnerabilities in Apache OpenMeetings potentially expose organizations to remote code execution attacks, cybersecurity firm Sonar warns. A web conferencing...
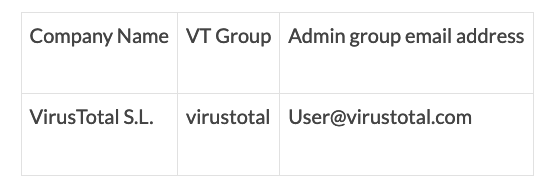
VirusTotal Provides Clarifications on Data Leak Affecting Premium Accounts – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs VirusTotal on Friday provided clarifications on the recent data leak that resulted in the exposure of information on 5,600 of...
Tech Titans Promise Watermarks to Expose AI Creations – Source: www.securityweek.com
Source: www.securityweek.com – Author: AFP The White House said Friday that OpenAI and others in the artificial intelligence race have committed to making their technology safer with...
GitHub Warns of North Korean Social Engineering Attacks Targeting Tech Firm Employees – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A North Korean threat actor has been observed targeting employees at technology firms in a new low-volume social engineering campaign,...
Tampa General Hospital Says Patient Information Stolen in Ransomware Attack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Tampa General Hospital this week started informing patients that their personal information was compromised in a ransomware attack that has...
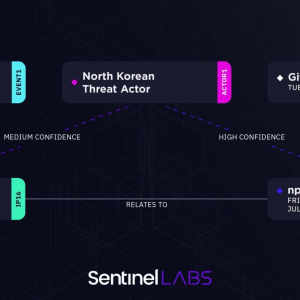
GitHub Developers Targeted by North Korea’s Lazarus Group – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The notorious Lazarus Group is behind a social engineering campaign that uses repository invitations and malicious npm packages to target...
BSides Sofia 2023 – Georgi Gerganov – Keytap Acoustic Keyboard Eavesdropping – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Startups’ Guide to Security Questionnaires – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mimi Pham For startups looking to win business and build trust with potential clients, a robust security program and effective response to...
Dell Adds Orchestration Capabilities to Data Protection Platform – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard Dell Technologies added orchestration capabilities to its data protection software that makes it simpler for IT teams to schedule backup...
Daniel Stori’s ‘Annoying Software’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Cybersecurity Insights with Contrast CISO David Lindner | 7/21 – Source: securityboulevard.com
Source: securityboulevard.com – Author: David Lindner, Director, Application Security Insight #1 WormGPT is a thing. The tool — being sold on hacker forums and considered “ChatGPT’s evil...
Digging Into An Interesting New CVE – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mike Larkin CVE-2023-38408, discovered by the Qualys Threat Research Unit (TRU), describes an RCE (remote code execution) vulnerability made possible by an...
BSides Sofia 2023 – Alexander Nedelchev – Unencrypted Malware, The Invisible Threat – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...