Source: www.darkreading.com – Author: Karen Spiegelman, Features Editor Keep up with the latest cybersecurity threats, newly-discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or...
Day: July 31, 2023
Healthcare Innovation: A Safe and Secure Approach – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Digital innovation continues to improve patient outcomes and accelerate accessibility and equity of care, while new digital technologies empower patients to...
Automatically Finding Prompt Injection Attacks – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Researchers have just published a paper showing how to automate the discovery of prompt injection attacks. They look something like...
Patchwork Hackers Target Chinese Research Organizations Using EyeShell Backdoor – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 31, 2023THNCyber Espionage / Malware Threat actors associated with the hacking crew known as Patchwork have been spotted targeting universities...
AVRecon Botnet Leveraging Compromised Routers to Fuel Illegal Proxy Service – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 31, 2023THNNetwork Security / Botnet More details have emerged about a botnet called AVRecon, which has been observed making use...
Fruity Trojan Uses Deceptive Software Installers to Spread Remcos RAT – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 31, 2023THNMalware / Cyber Threat Threat actors are creating fake websites hosting trojanized software installers to trick unsuspecting users into...
Multiple Flaws Found in Ninja Forms Plugin Leave 800,000 Sites Vulnerable – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 31, 2023THNWebsite Security / WordPress Multiple security vulnerabilities have been disclosed in the Ninja Forms plugin for WordPress that could...
Is backdoor access oppressive? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Bills granting access to end-to-end encrypted systems, opportunity for cybercriminals, abuse by authority, human rights, and tech companies leaving the UK? Original...
Gathering dust and data: How robotic vacuums can spy on you. – Source:
Source: – Author: 1 Mitigate the risk of data leaks with a careful review of the product and the proper settings. Original Post URL: Category &...
Dear all, What are some common subject lines in phishing emails? – Source:
Source: – Author: 1 Scammers exploit current ongoing events, account notifications, corporate communication, and a sense of urgency. Original Post URL: Category & Tags: – Views:...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
8 common work-from-home scams to avoid – Source:
Source: – Author: 1 That ‘employer’ you’re speaking to may in reality be after your personal information, your money or your help with their illegal activities...
Child identity theft: how do I keep my kids’ personal data safe? – Source:
Source: – Author: 1 Why is kids’ personal information in high demand, how do criminals steal it, and what can parents do to help prevent child...
Protect yourself from ticketing scams ahead of the Premier League Summer Series USA Tour – Source:
Source: – Author: 1 There is a significant secondary marketplace where tickets can sell for several times their original value, opening the opportunity for scammers and...
Key findings from ESET Threat Report H1 2023 – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here’s how cybercriminals have adjusted their tactics in response to Microsoft’s stricter security policies, plus other interesting findings from ESET’s new Threat...
The danger within: 5 steps you can take to combat insider threats – Source:
Source: – Author: 1 Some threats may be closer than you think. Are security risks that originate from your own trusted employees on your radar? Original...
ESET Research Podcast: Finding the mythical BlackLotus bootkit – Source:
Source: – Author: 1 Here’s a story of how an analysis of a supposed game cheat turned into the discovery of a powerful UEFI threat Original...
ESET Threat Report H1 2023 – Source:
Source: – Author: 1 A view of the H1 2023 threat landscape as seen by ESET telemetry and from the perspective of ESET threat detection and...
Emotet: sold or on vacation? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Originally a banking trojan, Emotet later evolved into a full-blown botnet and went on to become one of the most dangerous cyberthreats...
What’s up with Emotet? – Source:
Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: – Views:...
Deepfaking it: What to know about deepfake-driven sextortion schemes – Source:
Source: – Author: 1 Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns Original Post...
Verizon 2023 DBIR: What’s new this year and top takeaways for SMBs – Source:
Source: – Author: 1 Here are some of the key insights on the evolving data breach landscape as revealed by Verizon’s analysis of more than 16,000...
GUEST ESSAY: Here’s why shopping for an EV feels very much like shopping for a new laptop – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By James Jeffs Computer chips have been part of cars for a long time, but no one really cares about them...
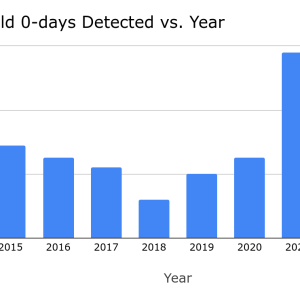
In 2022, more than 40% of zero-day exploits used in the wild were variations of previous issues – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Google’s Threat Analysis Group Google states that more than 40% of zero-day flaws discovered in 2022 were variants of previous...
New flaw in Ivanti Endpoint Manager Mobile actively exploited in the wild – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Software firm Ivanti disclosed another security vulnerability impacting Endpoint Manager Mobile (EPMM), that it said actively exploited. Ivanti disclosed a...
Security Affairs newsletter Round 430 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
Google: Android patch gap makes n-days as dangerous as zero-days – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google has published its annual 0-day vulnerability report, presenting in-the-wild exploitation stats from 2022 and highlighting a long-standing problem in...
Microsoft Edge is getting a ‘darker’ dark mode theme – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft has quietly announced an enhancement to the Edge browser’s dark mode, making it even darker. The current dark mode,...
Israel’s largest oil refinery website offline after DDoS attack – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Ax Sharma Website of Israel’s largest oil refinery operator, BAZAN Group is inaccessible from most parts of the world as threat actors claim to have...
BSides Leeds 2023 – Alex Martin – Five Days, One Red Team, A Beach Like No Other: The Bank Job – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...