Source: – Author: 1 A brief summary of what happened with Emotet since its comeback in November 2021 Original Post URL: Category & Tags: – Views:...
Day: July 28, 2023
Deepfaking it: What to know about deepfake-driven sextortion schemes – Source:
Source: – Author: 1 Criminals increasingly create deepfake nudes from people’s benign public photos in order to extort money from them, the FBI warns Original Post...
Verizon 2023 DBIR: What’s new this year and top takeaways for SMBs – Source:
Source: – Author: 1 Here are some of the key insights on the evolving data breach landscape as revealed by Verizon’s analysis of more than 16,000...
The good, the bad and the ugly of AI – Week in security with Tony Anscombe – Source:
Source: – Author: 1 The growing use of synthetic media and the difficulties in distinguishing between real and fake content raise a slew of legal and...
Moscow Court Convicts Former Group-IB Chief for Treason – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , IT Risk Management Ilya Sachkov Sentenced to 14 Years in Prison Mihir Bagwe (MihirBagwe) • July...
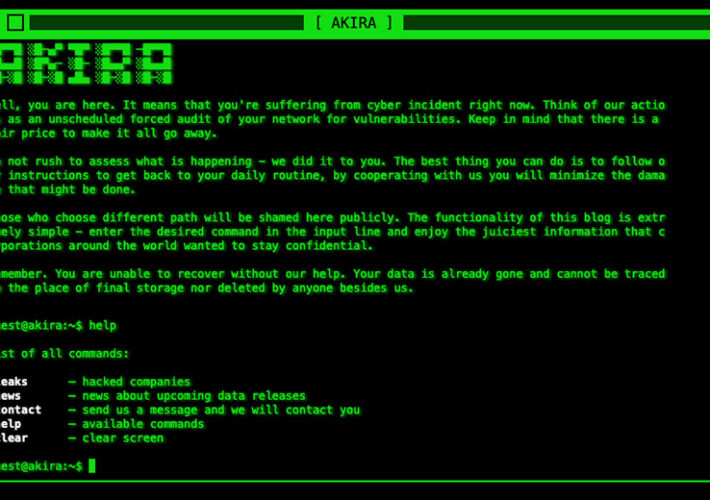
Are Akira Ransomware’s Crypto-Locking Malware Days Numbered? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware Ransomware-Building Group Lost Royal-Organized Competition, Researchers Say Mathew J. Schwartz (euroinfosec) • July 27, 2023...
Coro Buys Privatise to Infuse SASE With Network Connectivity – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , SASE , Security Operations Privatise Will Add DNS Filtering, Content Filtering, ZTNA to Coro’s SASE Platform...
Phishing Scam Affects Nearly 170K Henry Ford Health Patients – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Email Threat Protection , Fraud Management & Cybercrime , Healthcare Academic Medical Provider Says 3 Employee Email Accounts Were Compromised Marianne...
Breach Roundup: Zenbleed Flaw Exposes AMD Ryzen CPUs – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Incident & Breach Response , Security Operations Wuhan Earthquake Monitoring Center Suffers Cyberattack; NATO’s COI Portal Breached Anviksha More (AnvikshaMore) •...
US Senator Wyden Accuses Microsoft of ‘Cybersecurity Negligence’ – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Oregon senator Ron Wyden wants the U.S. government to hold Microsoft responsible for what he describes as “negligent cybersecurity practices”...
European Threat Intelligence Firm QuoIntelligence Raises $5.5 Million in Seed Funding – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Threat intelligence services provider QuoIntelligence today announced that it has raised €5 million ($5.5 million) in seed funding. The investment...
Head of US Cybersecurity Agency Sees Progress on Election Security, With More Work Needed for 2024 – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Efforts to protect the nation’s election systems have grown exponentially since the 2016 presidential election, but more is needed to...
TSA Updates Pipeline Cybersecurity Requirements – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs The Transportation Security Administration (TSA) announced on Wednesday an update to its cybersecurity requirements for oil and natural gas pipeline...
Multiple Security Issues Identified in Peloton Fitness Equipment – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Internet-connected Peloton fitness equipment is plagued with numerous security issues that could allow attackers to obtain device information or deploy...
The Good, the Bad and the Ugly of Generative AI – Source: www.securityweek.com
Source: www.securityweek.com – Author: Marc Solomon As humans, we’re naturally wired to be negative. It’s a widely studied concept referred to as negativity bias, and it’s...
Two New Vulnerabilities Could Affect 40% of Ubuntu Cloud Workloads – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend Researchers at cloud security firm Wiz have discovered two easily exploitable privilege escalation vulnerabilities in Ubuntu’s OverlayFS module affecting 40%...
CardioComm Takes Systems Offline Following Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Canadian heart monitoring and medical electrocardiogram solutions provider CardioComm this week announced it has taken systems offline following a cyberattack....
Axis Door Controller Vulnerability Exposes Facilities to Physical, Cyber Threats – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A potentially serious vulnerability affecting a network door controller made by Swedish security solutions provider Axis Communications can expose facilities...
Zimbra fixed actively exploited zero-day CVE-2023-38750 in ZCS – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Zimbra addressed a zero-day vulnerability exploited in attacks aimed at Zimbra Collaboration Suite (ZCS) email servers. Two weeks ago Zimbra...
DepositFiles exposed config file, jeopardizing user security – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini DepositFiles, a popular web hosting service, left its environment configuration file accessible, revealing a trove of highly sensitive credentials. The...
Group-IB CEO Ilya Sachkov sentenced to 14 years in a strict prison colony – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Ilya Sachkov, CEO and co-founder of Group-IB was sentenced to 14 years in a high security prison colony according to...
Two flaws in Linux Ubuntu affect 40% of Ubuntu users – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Wiz researchers discovered two Linux vulnerabilities in the Ubuntu kernel that can allow an unprivileged local user to gain elevated...
How scammers used SEO to disguise themselves as an electric utility – Source: securityboulevard.com
Source: securityboulevard.com – Author: Avast Blog Summer is at its height, and it’s a good time to go sit by the pool with a glass of...
Redefining Security: Going Beyond Compliance in Financial Organizations (Plus Memes!) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Votiro Team Organizations often confuse the concept of being compliant with being secure. They assume that they must be appropriately protected once...
BSides Leeds 2023 – Peter Jones – Practical Blue Teaming – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Netography: Getting Beyond the ‘Black Box’ Approach to DDoS – Source: securityboulevard.com
Source: securityboulevard.com – Author: Martin Roesch Netography: Getting Beyond the ‘Black Box’ Approach to DDoS By Martin Roesch, CEO According to the Verizon 2023 Data Breach...
Randall Munroe’s XKCD ‘Bad Map Projection: ABS (Longitude)’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Growing AI-powered fraud highlights the need for advanced fraud detection – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sift Trust and Safety Team In the six months since ChatGPT launched in November 2022, nearly half of consumers admitted to finding...
More malicious npm packages found in wake of JumpCloud supply chain hack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Roberts Two weeks after the IT management firm JumpCloud announced that it was the victim of a supply chain attack aimed...
A Fraud Risk Management Guide for Savvy Businesses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Arkose Labs Fraud is a pervasive threat to any organization’s viability and sustainability, with fraudsters continually seeking innovative ways to deceive and...