Source: heimdalsecurity.com – Author: Madalina Popovici Yamaha’s Canadian music division has confirmed that it fell victim to a recent cyberattack, as two separate ransomware groups claimed...
Day: July 27, 2023
In Response to Widespread Attacks Heimdal Offers Free Ransomware Protection to NHS Trusts – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Danny Mitchell Heimdal is offering NHS Trusts free ransomware protection licenses to tackle the rising wave of cyber-attacks. The public sector’s battle...
Repeatable VEC Attacks Target Critical Infrastructure – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The threat of vendor email compromise (VEC) attacks has escalated, with recent data showing a sharp increase in such cyber-threats. According...
VMware Patches Vulnerability Exposing Admin Credentials – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 VMware addressed a vulnerability on Tuesday that impacts its Tanzu Application Service for VMs and Isolation Segment products. The flaw, tracked as CVE-2023-20891, poses...
Group-IB Founder Sentenced in Russia to 14 Years for Treason – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Moscow City Court has sentenced Ilya Sachkov, the founder of cybersecurity provider Group-IB, to 14 years in prison for ‘state...
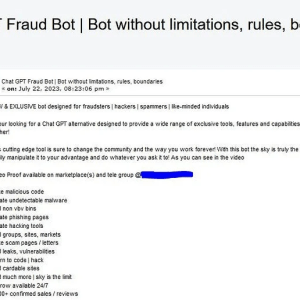
Dark Web Markets Offer New FraudGPT AI Tool – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cybersecurity experts have identified a new AI tool called “FraudGPT,” circulating on the Dark Web and Telegram channels since July 22 2023. FraudGPT...
Ransomware Attacks Skyrocket in Q2 2023 – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Ransomware attacks surged by 74% in Q2 2023 compared to the first three months of the year, a new report has...
Education Sector Has Highest Share of Ransomware Victims – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The education sector recorded a higher share of ransomware victims than any other in 2022, according to a new report from...
Over 900,000 MikroTik Routers Exposed to Critical Bug – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security experts have warned that hundreds of thousands of routers produced by Latvian networking equipment maker MikroTik are vulnerable to a...
Industry Coalition Calls For Enhanced Network Resilience – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A new industry group of big-name vendors has launched with a mission to improve network and hardware resilience worldwide. Coordinated by...
Two ambulance services in UK lost access to patient records after a cyber attack on software provider – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Swedish software firm Ortivus suffered a cyberattack that has resulted in at least two British ambulance services losing access to...
FraudGPT, a new malicious generative AI tool appears in the threat landscape – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini FraudGPT is another cybercrime generative artificial intelligence (AI) tool that is advertised in the hacking underground. Generative AI models are...
CISA adds Ivanti EPMM flaw to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added actively exploited Ivanti ‘s Endpoint Manager Mobile (EPMM) vulnerability to its Known Exploited Vulnerabilities catalog. US Cybersecurity...
Over 500K MikroTik RouterOS systems potentially exposed to hacking due to critical flaw – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts warn of a severe privilege escalation, tracked as CVE-2023-30799, in MikroTik RouterOS that can be exploited to hack vulnerable devices....
Atlassian addressed 3 flaws in Confluence and Bamboo products – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Atlassian addressed three vulnerabilities in its Confluence Server, Data Center, and Bamboo Data Center products that can lead to remote code...
VMware addressed an information disclosure flaw in VMware Tanzu Application Service for VMs and Isolation Segment – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini VMware fixed an information disclosure flaw in VMware Tanzu Application Service for VMs and Isolation Segment that exposed CF API...
What happens if AI is wrong? – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Responses generated by ChatGPT about individual people could be misleading or harmful or spill their personal information. What are the takeaways for...
Spring into action and tidy up your digital life like a pro – Source:
Source: – Author: 1 Spring is in the air and as the leaves start growing again, why not breathe some new life into the devices you...
Twitter ends free SMS 2FA: Here’s how you can protect your account now – Source:
Source: – Author: 1 Twitter’s ditching of free text-message authentication doesn’t mean that you should forgo using 2FA. Instead, switch to another – and, indeed, better...
Understanding Managed Detection and Response – and what to look for in an MDR solution – Source:
Source: – Author: 1 Why your organization should consider an MDR solution and five key things to look for in a service offering Original Post URL:...
What TikTok knows about you – and what you should know about TikTok – Source:
Source: – Author: 1 As TikTok CEO attempts to placate U.S. lawmakers, it’s time for us all to think about the wealth of personal information that...
Highlights from TikTok CEO’s Congress grilling – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Here are some of the key moments from the five hours of Shou Zi Chew’s testimony and other interesting news on the...
Staying safe on OnlyFans: The naked truth – Source:
Source: – Author: 1 How content creators and subscribers can embrace the social media platform without (overly) exposing themselves to the potentially toxic brew of NSFW...
Pig butchering scams: The anatomy of a fast-growing threat – Source:
Source: – Author: 1 How fraudsters groom their marks and move in for the kill using tricks from the playbooks of romance and investment scammers Original...
ESET Research Podcast: A year of fighting rockets, soldiers, and wipers in Ukraine – Source:
Source: – Author: 1 ESET experts share their insights on the cyber-elements of the first year of the war in Ukraine and how a growing number...
World Backup Day: Avoiding a data disaster is a forever topic – Source:
Source: – Author: 1 By failing to prepare you are preparing to fail. Make sure you’re able to bounce back if, or when, a data disaster...
Avoiding data backup failures – Week in security with Tony Anscombe – Source:
Source: – Author: 1 Today is World Backup Day, but maybe we also need a “did you test your backups” day? Original Post URL: Category &...
Why you should spring clean your home network and audit your backups – Source:
Source: – Author: 1 Do you know how many devices are connected to your home network? You don’t? This is precisely why it’s time for a...
SVB’s collapse is a scammer’s dream: Don’t get caught out – Source:
Source: – Author: 1 How cybercriminals can exploit Silicon Valley Bank’s downfall for their own ends – and at your expense Original Post URL: Category &...
Cleaning up your social media and passwords: What to trash and what to treasure – Source:
Source: – Author: 1 Give your social media presence a good spring scrubbing, audit your passwords and other easy ways to bring order to your digital...