Source: www.bleepingcomputer.com – Author: Ionut Ilascu Image: Bing Create The ALPHV ransomware gang, also referred to as BlackCat, is trying to put more pressure on their...
Day: July 27, 2023
Top takeaways from TrustCon 2023 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jane Lee TrustCon is THE place to be for trust and safety practitioners to network and learn from others in the industry....
Navigating the New SEC Cybersecurity Rules: A Comprehensive Guide for Security Leaders – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ethan Bresnahan On July 26, the Securities and Exchange Commission voted to adopt rules to increase transparency with investors around cyber risk...
BSides Leeds 2023 – John Atkinson – The Obfuscation Situation – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Attackers are Hiding Malware Behind Barbie-Themed Scams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeffrey Burt The massive box office brought in by the “Barbie” movie during its opening weekend—$162 million—surprised even some Hollywood industry watchers...
Linux Commands To Check The State Of Firmware – Source: securityboulevard.com
Source: securityboulevard.com – Author: Paul Asadoorian Whether you are new to Linux or a seasoned Linux systems administrator, knowing the hardware and firmware on your systems...
Russia Sends Cybersecurity CEO to Jail for 14 Years – Source: securityboulevard.com
Source: securityboulevard.com – Author: BrianKrebs The Russian government today handed down a treason conviction and 14-year prison sentence on Iyla Sachkov, the former founder and CEO...
Cyber Storm Unleashed: Unmasking STORM-0978’s Exploitation of the CVE-2023-36884 Vulnerability – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cyborg Security Threat Overview – CVE-2023-36884 CVE-2023-36884 is a newly discovered critical security flaw in Microsoft Office and Windows HTML, enabling remote...
Unleashing Intelligence: Transforming NetFlow and Flow Log Data into Actionable Intelligence – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tom Dixon Unleashing Intelligence: Transforming NetFlow and Flow Log Data into Actionable Intelligence Tom Dixon, Senior Field Engineer In our modern digital...
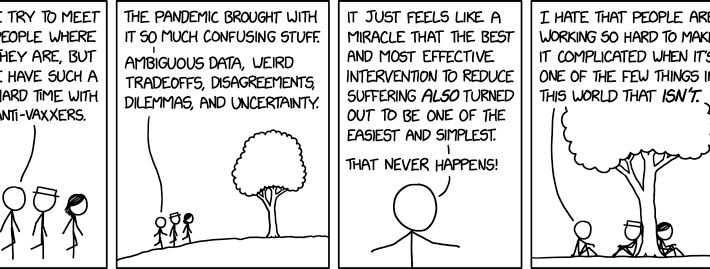
Randall Munroe’s XKCD ‘Anti-Vaxxers’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
ALERT: Google Wants to DRM your OS for ‘Web Environment Integrity’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Thinly veiled attempt to track you and make more ad money. Google’s proposed new web protocol has the effect of...
ChatGPT’s Web3 Bug Reports Are ‘Nonsensical,’ Immunefi Says – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development The Generative AI Tool Can Write Bug Reports – Just...
Why CrowdStrike Is Eyeing Cyber Vendor Bionic at Up to $300M – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Cloud Security , Next-Generation Technologies & Secure Development Bionic Is in Line for a 9-Figure Deal Just 31...
Cardiac Monitoring Software Firm Hit With Cyberattack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Fraud Management & Cybercrime , Healthcare , Industry Specific CardioComm Says Business Operations Will Be Affected for Days or ‘Longer’ Marianne...
OnDemand | Graduating into a New Era: Cloud Security’s Biggest Challenges – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Live Webinar | A Proactive Approach to Incident Response for OT – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Paul Shaver Global Practice Leader, Mandiant Mr. Shaver is the Global Practice Leader for Mandiant’s Industrial Control Systems/Operational Technology Security Consulting...
Software Vendor Attack Slows Down 2 UK Ambulance Services – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Healthcare , Industry Specific Paramedics Can’t Access NHS Patient Records, Resort to Using Pen and Paper Marianne Kolbasuk McGee (HealthInfoSec) •...
Criminals Are Flocking to a Malicious Generative AI Tool – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Next-Generation Technologies & Secure Development A 12-Month Subscription to FraudGPT Costs $1,700 Prajeet Nair (@prajeetspeaks)...
Learn How to Protect Your Business With Ultimate Security for $80 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy on July 26, 2023, 5:36 AM EDT Learn How to Protect Your Business With Ultimate Security for $80 Protect your...
Get 8 Months of Live Cyber Security Training for Under $500 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy on July 25, 2023, 1:33 PM EDT Get 8 Months of Live Cyber Security Training for Under $500 If you’re...
Russia Sends Cybersecurity CEO to Jail for 14 Years – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs The Russian government today handed down a treason conviction and 14-year prison sentence on Iyla Sachkov, the former founder and CEO...
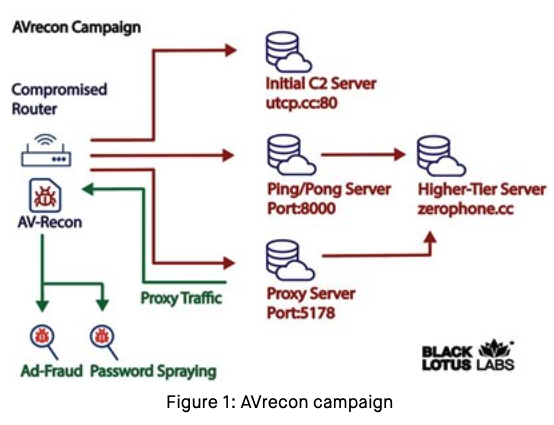
Who and What is Behind the Malware Proxy Service SocksEscort? – Source: krebsonsecurity.com
Source: krebsonsecurity.com – Author: BrianKrebs Researchers this month uncovered a two-year-old Linux-based remote access trojan dubbed AVrecon that enslaves Internet routers into botnet that bilks online...
Backdoor in TETRA Police Radios – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Seems that there is a deliberate backdoor in the twenty-year-old TErrestrial Trunked RAdio (TETRA) standard used by police forces around...
Smashing Security podcast #332: Nudes leak at the plastic surgery, Mali mail mix-up, and WormGPT – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Dr 90210 finds himself in a sticky situation after his patients’ plastic surgery photos AND more end up in the...
Following claims by two ransomware groups, Yamaha confirms cyberattack – Source: www.bitdefender.com
Source: www.bitdefender.com – Author: Graham Cluley Yamaha Corporation, the world’s largest producer of musical equipment, has confirmed that has suffered a “cybersecurity incident” during which hackers...
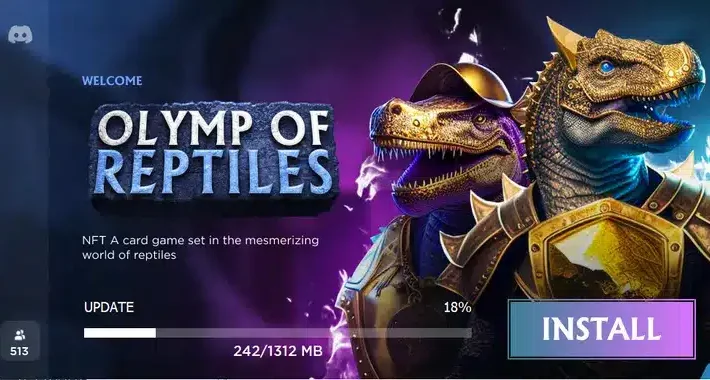
New Realst Mac malware, disguised as blockchain games, steals cryptocurrency wallets – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Fake blockchain games, that are being actively promoted by cybercriminals on social media, are actually designed to infect the computers...
Terrestrial Trunked Radio System Vulnerable to Leakage and Message Injection – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Dutch researchers revealed 5 vulnerabilities in the Terrestrial Trunked Radio (TETRA) that could expose government organizations and critical infrastructure communication...
Norwegian Government`s System Breached over Ivanti EPMM Zero-Day – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși The Norwegian National Security Authority (NSM) revealed that threat actors exploited the CVE-2023-35078 zero-day vulnerability in Ivanti’s Endpoint Manager Mobile...
What Is Vulnerability Scanning: Definition, Types, Best Practices – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu What Is Vulnerability Scanning? Vulnerability scanning is the process of discovering, analysing, and reporting security flaws and vulnerabilities. Alongside vulnerability assessment,...
New Vulnerability Puts 926,000 MikroTik Routers at Risk! Users Urged to Patch – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Researchers found a critical ‘Super Admin’ privilege elevation vulnerability that impacts MikroTik devices. Over 900,000 RouterOS routers are at risk...