Source: www.govinfosecurity.com – Author: 1 Security Awareness Programs & Computer-Based Training , Training & Security Leadership Webhelp CISO on Interactive Tools for Cybersecurity Awareness Training Anna...
Day: July 24, 2023
As Ransomware Monetization Hits Record Low, Groups Innovate – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Fraud Management & Cybercrime , Ransomware Clop’s Zero-Day Mass Exploitation and Extortion is Apogee of High Impact Innovation Mathew J. Schwartz...
Will FedNow Truly Rewire the US Payments Landscape? – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Finance & Banking , Fraud Management & Cybercrime , Fraud Risk Management Experts Discuss Fraud, Security, Implementation Hurdles With Fast Payment...
OneTrust Raises $150M From Al Gore’s Firm Following Layoffs – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Governance & Risk Management , GRC , Privacy Vendor Cuts Valuation by $800M to Get Funding From Generation Investment Management Michael...
Law Firm Hack Affects Victims of an Earlier Breach Again – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 HIPAA/HITECH , Standards, Regulations & Compliance Client Files Breached Included Data of Vision Benefits Plan Members Marianne Kolbasuk McGee (HealthInfoSec) •...
Nubeva’s Ransomware Key Interception and Decryption Technology Validated in Third-Party Lab – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend NuRR is a product that claims to intercept and capture the encryption keys at the start of a ransomware’s encryption...
OneTrust Raises $150 Million at $4.5 Billion Valuation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Data privacy and governance provider OneTrust today announced that it has raised $150 million in new funding, bringing the total...
Cybersecurity Public-Private Partnership: Where Do We Go Next? – Source: www.securityweek.com
Source: www.securityweek.com – Author: Derek Manky When faced with an increasing number of cyberattacks, many organizations think in terms of what additional security tools they need....
MOVEit Hack Could Earn Cybercriminals $100M as Number of Confirmed Victims Grows – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Ransomware recovery company Coveware believes the Cl0p ransomware gang could earn as much as $100 million from the MOVEit hack,...
Los Angeles SIM Swapper Pleads Guilty to Cybercrime Charges – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A Los Angeles man has pleaded guilty to using SIM swapping to perpetrate multiple cybercrime schemes targeting hundreds of victims....
Home affairs cyber survey exposed personal data of participating firms – Source: www.theguardian.com
Source: www.theguardian.com – Author: Josh Taylor The home affairs department exposed the personal information of more than 50 small business survey participants who were sought for...
Over 20,000 Citrix Appliances Vulnerable to New Exploit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A new exploit technique targeting a recent Citrix Application Delivery Controller (ADC) and Gateway vulnerability can be used against thousands...
Atlassian Patches Remote Code Execution Vulnerabilities in Confluence, Bamboo – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Atlassian has released patches for two remote code execution (RCE) vulnerabilities in Confluence Data Center and Server and another in...
Perimeter81 Vulnerability Disclosed After Botched Disclosure Process – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Network security company Perimeter81 apparently needs to improve its responsible disclosure process for vulnerabilities found in its products. Cybersecurity researcher...
Industrial Organizations in Eastern Europe Targeted by Chinese Cyberspies – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs A China-linked cyberspy group appears to be behind a campaign targeting industrial organizations in Eastern Europe, cybersecurity firm Kaspersky reported...
Stolen Microsoft Key: The Impact Is Higher Than Expected – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Earlier this month, Microsoft and CISA disclosed a security incident and attributed it to the Chinese threat group Storm-0558. The...
Tampa General Hospital Data Breach Impacts 1.2 Million Patients – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Tampa General Hospital (TGH) has revealed a data breach that may have affected the information of approximately 1.2 million patients. Writing...
Biden-Harris Administration Secures AI Commitments For Safety – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The Biden-Harris Administration has taken a new step towards ensuring the responsible development of artificial intelligence (AI) technology by securing voluntary...
Cyber-Attack Strikes Norwegian Government Ministries – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Norway’s government has reported that twelve of its ministries have fallen victim to a cyber-attack. At a press conference earlier today,...
Novel Open Source Supply Chain Attacks Target Banking Sector – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Application security provider Checkmarx has identified what it described as the first open source software supply chain attacks targeting the banking...
Booz Allen Pays $377m to Settle Government Fraud Case – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading US government contractor has agreed to pay a massive $377.5m to resolve allegations of procurement fraud – one of...
Thousands of Citrix Servers Exposed to Zero-Day Bug – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Over 15,000 Citrix servers worldwide are at risk of compromise unless administrators patch urgently, a leading security non-profit has warned. The...
Clop Could Make $100m from MOVEit Campaign – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The notorious Clop ransomware gang may earn as much as $100m from its recent data extortion campaign, after a small number...
Google Reportedly Disconnecting Employees from the Internet – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Google Reportedly Disconnecting Employees from the Internet Supposedly Google is starting a pilot program of disabling Internet connectivity from...
Norwegian government IT systems hacked using zero-day flaw – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Norwegian government is warning that its ICT platform used by 12 ministries has suffered a cyberattack after hackers exploited...
How is the Dark Web Reacting to the AI Revolution? – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Flare A quick search for “ChatGPT” on the dark web and Telegram shows 27,912 mentions in the past six months....
Windows 11 23H2 update coming this fall, here’s what’s new – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar As Microsoft prepares for the imminent rollout of Windows 11 23H2, they’ve been developing various innovative features designed to improve...
IBM Report: Average Cost of a Data Breach Rises to $4.45 Million – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Megan Crouse Image: Adobe Stock Data breach costs rose to $4.45 million per incident in 2023, IBM found in its annual Cost...
Auditing and Logging Policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Many computer systems, network devices and other technological hardware used in the enterprise can audit and log various activities. These activities include...
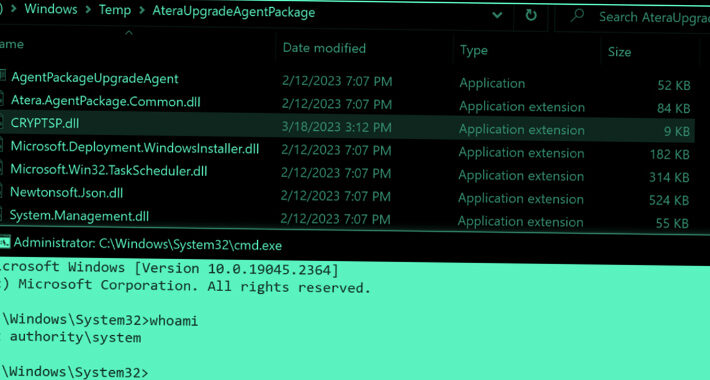
Critical Zero-Days in Atera Windows Installers Expose Users to Privilege Escalation Attacks – Source:thehackernews.com
Source: thehackernews.com – Author: . Jul 24, 2023THNWindows Security / Zero-Day Zero-day vulnerabilities in Windows Installers for the Atera remote monitoring and management software could act...