Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Up until last Thursday, OpenAI’s ChatGPT held the record for the fastest stratospheric platform growth ever, reaching 10 million...
Day: July 10, 2023
MY TAKE: ‘IOWN’ makes the business case for fostering diversity, respecting individual privacy – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido By Byron V. Acohido To tap the full potential of massively interconnected, fully interoperable digital systems we must solve privacy and...
RomCom Group Targets Ukraine Supporters Ahead of NATO Summit – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 The RomCom threat actor has reportedly launched a targeted cyber campaign aimed at organizations and individuals supporting Ukraine just days before...
Crimeware Group Asylum Ambuscade Ventures Into Cyber-Espionage – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Asylum Ambuscade, a crimeware group, has been observed changing tactics and moving to cyber espionage. The group, initially exposed by researchers...
Android OS Tools Fuel Cybercrime Spree, Prey on Digital Users – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Cyber-criminals have increasingly utilized specialized mobile Android OS device spoofing tools to bypass anti-fraud controls and impersonate compromised account holders. According...
Central Bankers Develop Framework For Securing Digital Currencies – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 An international financial institution owned by the world’s central banks has published a new framework designed to help members mitigate cyber...
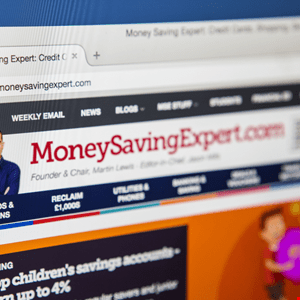
Martin Lewis Shocked at Deepfake Investment Scam Ad – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A leading UK TV personality has hit out at a lack of regulation for fraudulent internet advertising, after a deepfake likeness...
Cyber Extortion Cases Surge 39% Annually – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Incidents of online extortion reported to the police increased by nearly two-fifths in 2022 compared to a year previously, according to...
TPG to Acquire Forcepoint’s Government Cybersecurity Business Unit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ryan Naraine Private equity giant TPG on Monday announced plans to acquire Forcepoint’s Global Governments and Critical Infrastructure (G2CI) business unit in...
Critical Infrastructure Services Firm Ventia Takes Systems Offline Due to Cyberattack – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Critical infrastructure services provider Ventia over the weekend announced that it has taken some of its systems offline to contain...
A Cybersecurity Wish List Ahead of NATO Summit – Source: www.securityweek.com
Source: www.securityweek.com – Author: Kevin Townsend As tomorrow’s NATO Summit in Vilnius, Lithuania approaches, SecurityWeek questions what NATO should do about cybersecurity. The Russia/Ukraine conflict offers...
Honeywell Boosting OT Cybersecurity Offering With Acquisition of SCADAfence – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Industrial giant Honeywell wants to extend its operational technology (OT) cybersecurity portfolio with the acquisition of Tel Aviv, Israel-based OT...
PoC Exploit Published for Recent Ubiquiti EdgeRouter Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A recently patched vulnerability in Ubiquiti EdgeRouter and AirCube devices could be exploited to execute arbitrary code, vulnerability reporting firm...
Critical Vulnerability Can Allow Takeover of Mastodon Servers – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A critical vulnerability in the decentralized social networking platform Mastodon could be exploited to take over servers. The issue was...
StackRot: Linux Bug so bad Linus Dives Into Code to Fix It – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Torvalds feels the pressure, fixes lazy locks. A critical vulnerability in the Linux kernel caused Linus Torvalds (pictured) to get...
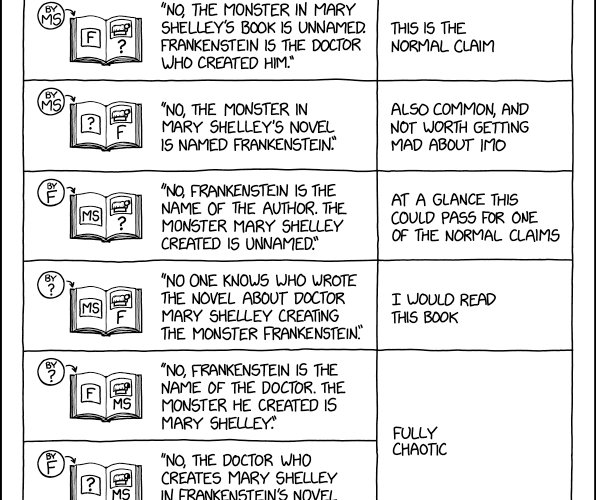
Randall Munroe’s XKCD ‘Frankenstein Claim Permutations’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
BSides Knoxville 2023 – Omar Minawi – Client-Side JavaScript From Your Nightmares: Multi-Step XSS Attacks And Defenses – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Navigating the Digital Landscape: A Guide for Young People on Managing Their Online Identities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Deepak Gupta – Tech Entrepreneur, Cybersecurity Author As the digital world continues to flourish, it is becoming increasingly crucial for young people...
Employee Spotlight – Joseph Pike – Source: securityboulevard.com
Source: securityboulevard.com – Author: Janice Sheridan We spoke to Security Analyst, Joseph Pike For this month’s employee spotlight piece, we spoke to Security Analyst and heavy...
Advanced Endpoint Protection (AEP): What Are the Options? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Gilad David Maayan Advanced endpoint protection, often referred to as AEP, is a comprehensive cybersecurity solution designed to protect an organization’s endpoints,...
Finding the Right Tools for Response and Visibility in the SOC – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sue Poremba One of the more difficult tasks for a cybersecurity professional—from the CISO to the person responsible for log management in...
Enhancing Financial Sector Security: IBM Cloud Security & Compliance Center and CyberSaint Collaborate to Streamline 3rd and 4th Party Risk Management – Source: securityboulevard.com
Source: securityboulevard.com – Author: Vivek Kinra and Jerry Layden We are thrilled to announce a strategic integration between IBM Cloud Security & Compliance Center and CyberSaint,...
Third-party risk management survey: Prioritize end-to-end software supply chain security — or fail – Source: securityboulevard.com
Source: securityboulevard.com – Author: John P. Mello Jr. Awareness of the risks posed by third-party vendors is high among organizations across industries, but visibility into those...
Crafting a Successful Cybersecurity Risk Management Strategy – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michelle Ofir Geveye In a world where cyber risks lurk in the dark shadows of our networks, one thing is crystal clear....
Banking Firms Under Attack by Sophisticated ‘Toitoin’ Campaign – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading A sophisticated and evasive malware campaign is targeting businesses in Latin America with a multi-stage attack that...
How to Use Log Management to Retrace Your Digital Footsteps – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 Logs are like digital footprints or a letter that developers write to themselves for the future. They track every action or...
What Is Vendor Risk Management (VRM)? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Madalina Popovici In the ever-evolving and intricate realm of modern business, organizations rely heavily on various vendors and third-party partners to keep their...
Chrome’s big design refresh uses Microsoft Mica effect in custom themes – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Google is working on a significant design overhaul for Chrome across Windows, Mac, and Chromebook platforms. Named Chrome’s Material You-based,...
Charming Kitten hackers use new ‘NokNok’ malware for macOS – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Security researchers observed a new campaign they attribute to the Charming Kitten APT group where hackers used new NokNok malware that...
Windows Subsystem for Android gets July 2023 preview with new features – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Windows 11, with its Windows Subsystem for Android (WSA), allows users to access almost all popular Android apps directly from...