Source: securityboulevard.com – Author: Dex Tovin In today’s world of software development, cybersecurity is more than a luxury; it’s a necessity. Cyber threats aren’t only growing...
Month: June 2023
How to Spot and Stop Active Directory Attacks Faster – Part 2 – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bob Zhang Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
BSidesSF 2023 – Ben Sadeghipour – Hackers Don’t Care About Scope – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
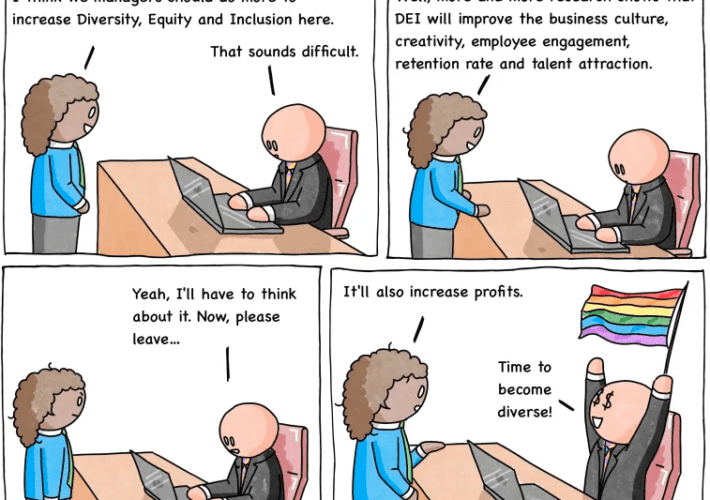
Comic Agilé – Mikkel Noe-Nygaard, Luxshan Ratnarav – #244 — DEI – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics BSidesSF 2023 – Sanchay Jaipuriyar – Overwatch: A Serverless Approach To Orchestrating Your Security Automation Why is Identity...
Security Questionnaires: The Complete Breakdown for Vendors – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mimi Pham New research from SecurityScorecard found that 98% of organizations have at least one vendor that’s had a breach in the...
Hackers Using MOVEit Flaw to Deploy Web Shells, Steal Data – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Governance & Risk Management , Patch Management Mandiant Said TTPs of Threat Group Behind Exploiting MOVEit Appear Similar to FIN11 Michael...
Chinese APT Backdoor Bypasses Indonesian Antivirus – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Cybercrime , Endpoint Security , Fraud Management & Cybercrime TinyNote Creates a ‘You Can’t See It But It’s There’ Open Window...
Mistrial in Criminal HIPAA Case Against Army Doctor & Spouse – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 HIPAA/HITECH , Standards, Regulations & Compliance Jury Deadlocked on Whether Couple Was Entrapped to Leak Records to Undercover Agent Marianne Kolbasuk...
New Linux Ransomware BlackSuit is similar to Royal ransomware – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Experts noticed that the new Linux ransomware BlackSuit has significant similarities with the Royal ransomware family. Royal ransomware is one of the most...
CISA adds Progress MOVEit Transfer zero-day to its Known Exploited Vulnerabilities catalog – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini US CISA added actively exploited Progress MOVEit Transfer zero-day vulnerability to its Known Exploited Vulnerabilities catalog. US Cybersecurity and Infrastructure...
New botnet Horabot targets Latin America – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A new botnet malware dubbed Horabot is targeting Spanish-speaking users in Latin America since at least November 2020. Cisco Talos researchers were...
Point32Health ransomware attack exposed info of 2.5M people – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini After the recent ransomware attack, Point32Health disclosed a data breach that impacted 2.5 million Harvard Pilgrim Health Care subscribers. In...
New Linux Ransomware Strain BlackSuit Shows Striking Similarities to Royal – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 03, 2023Ravie LakshmananEndpoint Security / Linux An analysis of the Linux variant of a new ransomware strain called BlackSuit has...
Cloud Security Tops Concerns for Cybersecurity Leaders: EC-Council’s Certified CISO Hall of Fame Report 2023 – Source:thehackernews.com
Source: thehackernews.com – Author: . A survey of global cybersecurity leaders through the 2023 Certified CISO Hall of Fame Report commissioned by the EC-Council identified 4...
FTC Slams Amazon with $30.8M Fine for Privacy Violations Involving Alexa and Ring – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 03, 2023Ravie LakshmananPrivacy / Technology The U.S. Federal Trade Commission (FTC) has fined Amazon a cumulative $30.8 million over a...
Improve your app security on Azure – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Mary Branscombe Image: PhotoGranary/Adobe Stock When cloud computing first became popular, it was seen as a way of reducing both friction and...
1Password enables passkeys — a new option from passwords – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Karl Greenberg Identity management company 1Password is spinning up a pair of new features that constitute a major shift away from passwords...
Develop valuable cyber security skills over a lifetime for only $70 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy on June 2, 2023, 11:48 AM EDT Develop valuable cyber security skills over a lifetime for only $70 Not only...
How top CISOs drive unparalleled operational resilience – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In 2023 alone, more than 33 billion records will be stolen by cyber criminals. Last year, phishing attacks increased...
5 ways ChatGPT and LLMs can advance cyber security – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: Although generative AI chatbots and Large Language Models (LLMs) can be a double-edged sword when it comes to corporate...
Enzo Biochem Hit by Ransomware, 2.5 Million Patients’ Data Compromised – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Enzo Biochem, a biotechnology company renowned for producing and distributing DNA-based tests designed to identify viral and bacterial diseases, has recently...
US and Korean Agencies Issue Warning on North Korean Cyber-Attacks – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 US and South Korean security agencies have issued a joint warning regarding North Korea’s use of social engineering tactics in cyber-attacks....
Malicious PyPI Packages Use Compiled Python Code to Bypass Detection – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Security researchers at ReversingLabs have discovered a novel attack that used compiled Python code to evade detection. According to ReversingLabs reverse...
Russia points finger at US for iPhone exploit campaign that also hit Kaspersky Lab – Source: www.csoonline.com
Source: www.csoonline.com – Author: The Operation Triangulation surveillance campaign infects Apple iPhones without the need for user action and is difficult to detect. The Russian federal...
Attackers use Python compiled bytecode to evade detection – Source: www.csoonline.com
Source: www.csoonline.com – Author: Newly discovered campaign takes advantage of the fact that most vulnerability scanning tools don’t read compiled open-source software. Attackers who are targeting...
MOVEit Transfer vulnerability appears to be exploited widely – Source: www.csoonline.com
Source: www.csoonline.com – Author: A SQL injection vulnerability has been found in the MOVEit Transfer web application, allowing an unauthenticated attacker to gain unauthorized access to...
PyPI’s 2FA Requirements Don’t Go Far Enough, Researchers Say – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tara Seals, Managing Editor, News, Dark Reading The official open source code repository for the Python programming language, the Python Package Index...
‘PostalFurious’ SMS Attacks Target UAE Citizens for Data Theft – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading Residents of the United Arab Emirates have been targeted by SMS campaigns that aim to steal payment and...
‘Picture-in-Picture’ Obfuscation Spoofs Delta, Kohl’s for Credential Harvesting – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nathan Eddy, Contributing Writer, Dark Reading Hackers are turning to obfuscation tactics relying on glossy advertising photos from Delta Airlines and retailer...
Streamers Ditch Netflix for Dark Web After Password Sharing Ban – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading From the outside, Netflix’s ban on password sharing may seem like a net positive for cybersecurity,...