Source: www.darkreading.com – Author: Microsoft Security, Microsoft As the war in Ukraine extends into its second year, Russian threat actors have expanded the scope of their...
Month: June 2023
How Popular Messaging Tools Instill a False Sense of Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Tobias Pischl, Head of Product, Information, and Email Security, Symantec Enterprise Division, Broadcom Today, an increasing number of large enterprises, from financial...
Microsoft links Cadet Blizzard APT to Russia’s military intelligence GRU – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Microsoft linked a series of wiping attacks to a Russia-linked APT group, tracked as Cadet Blizzard, that is under the control...
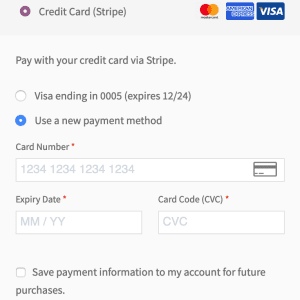
Critical flaw found in WooCommerce Stripe Gateway Plugin used by +900K sites – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Hundreds of thousands of online stores are potentially exposed to hacking due to a critical vulnerability in the WooCommerce Stripe...
Unveiling the Balada injector: a malware epidemic in WordPress – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Learn the shocking truth behind the Balada Injector campaign and find out how to protect your organization from this relentless...
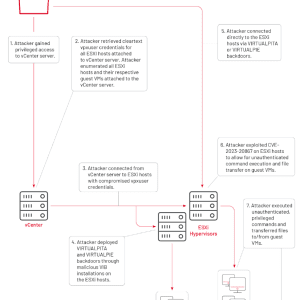
China-linked APT UNC3886 used VMware ESXi Zero-Day – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A China-linked APT group tracked as UNC3886 has been spotted exploiting a VMware ESXi zero-day vulnerability. Mandiant researchers observed a...
LLM meets Malware: Starting the Era of Autonomous Threat – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Malware researchers analyzed the application of Large Language Models (LLM) to malware automation investigating future abuse in autonomous threats. In...
Smashing Security podcast #326: Right Royal security threats and MOVEit mayhem – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley There are shocking revelations about a US Government data suck-up, historic security breaches at Windsor Castle, and the MOVEit hack...
Talking cybersecurity on “Learning Curve” – Source: grahamcluley.com
Source: grahamcluley.com – Author: Graham Cluley Earlier this year I had the honour of being invited by Vodafone to appear on an episode of “Learning Curve”,...
BrandPost: Microsoft special report: Iran’s adoption of cyber-enabled influence operations – Source: www.csoonline.com
Source: www.csoonline.com – Author: About | When you have comprehensive security, the future is yours to build. Learn about the strategies and solutions to secure your...
Attackers set up rogue GitHub repos with malware posing as zero-day exploits – Source: www.csoonline.com
Source: www.csoonline.com – Author: The threat actor created fake personas on Twitter for researchers at a non-existent security firm. In an unusual attack campaign, a hacker...
Microsoft Office 365 AitM phishing reveals signs of much larger BEC campaign – Source: www.csoonline.com
Source: www.csoonline.com – Author: This newly discovered, global campaign indicates growing popularity for multi-stage adversary-in-the-middle tactics among threat actors.
Rezilion releases agentless runtime software vulnerability management solution – Source: www.csoonline.com
Source: www.csoonline.com – Author: Software supply chain security vendor claims to have discovered that true, non-agent-based runtime vulnerability analysis is possible by harnessing cloud APIs. Roman...
Cyber liability insurance vs. data breach insurance: What’s the difference? – Source: www.csoonline.com
Source: www.csoonline.com – Author: Cyber insurance is increasingly becoming a compulsory element in business relationships. Knowing what coverage meets a company’s specific needs can provide better...
Chinese Hackers Exploit VMware Zero-Day to Backdoor Windows and Linux Systems – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananZero-Day / Network Security The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day...
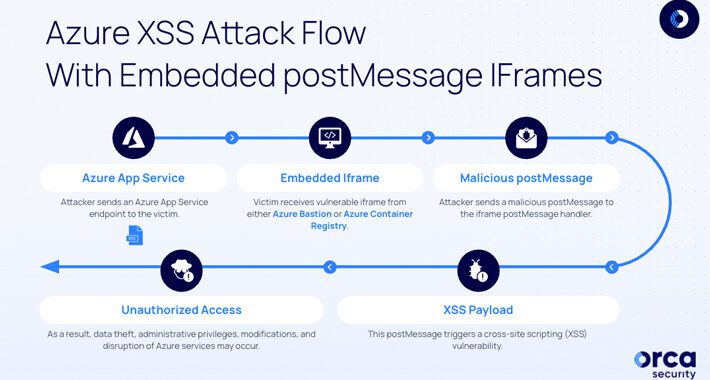
Severe Vulnerabilities Reported in Microsoft Azure Bastion and Container Registry – Source:thehackernews.com
Source: thehackernews.com – Author: . Jun 14, 2023Ravie LakshmananCloud Security / Vulnerability Two “dangerous” security vulnerabilities have been disclosed in Microsoft Azure Bastion and Azure Container...
Microsoft: Windows Kernel CVE-2023-32019 fix is disabled by default – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has released an optional fix to address a Kernel information disclosure vulnerability affecting systems running multiple Windows versions, including...
Fake WannaCry ransomware targets Russian “Enlisted” FPS players – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A ransomware operation targets Russian players of the Enlisted multiplayer first-person shooter, using a fake website to spread trojanized versions...
Windows 11 KB5027231 update breaks Google Chrome for Malwarebytes users – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Malwarebytes confirmed today that the Windows 11 22H2 KB5027231 cumulative update released this Patch Tuesday breaks Google Chrome on its customers’...
New ‘Shampoo’ Chromeloader malware pushed via fake warez sites – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A new ChromeLoader campaign is underway, infecting visitors of warez and pirated movie sites with a new variant of the...
Microsoft links data wiping attacks to new Russian GRU hacking group – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has linked a threat group it tracks as Cadet Blizzard since April 2023 to Russia’s Main Directorate of the General Staff...
Chinese hackers use DNS-over-HTTPS for Linux malware communication – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas The Chinese threat group ‘ChamelGang’ infects Linux devices with a previously unknown implant named ‘ChamelDoH,’ allowing DNS-over-HTTPS communications with attackers’...
CISA: LockBit ransomware extorted $91 million in 1,700 U.S. attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan U.S. and international cybersecurity authorities said in a joint LockBit ransomware advisory that the gang successfully extorted roughly $91 million...
Compliance Automation: Your Audit Experience Before and After – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sponsored by Drata Richard Stevenson, Manager of Cybersecurity Risk Management and Compliance at Drata Automation transforms the audit experience. What was once...
Fake zero-day PoC exploits on GitHub push Windows, Linux malware – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Hackers are impersonating cybersecurity researchers on Twitter and GitHub to publish fake proof-of-concept exploits for zero-day vulnerabilities that infect Windows...
The fascinating history of cyber security you never knew – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau Contributed by George Mack, Content Marketing Manager, Check Point Software Cyber security has evolved significantly throughout the years. Much of it...
Google introduces Secure AI Framework (SAIF) – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau EXECUTIVE SUMMARY: In the wake of ChatGPT’s debut on the world stage, interest in generative artificial intelligence (AI) exploded. Generative AI...
News alert: Cybersixgill introduces generative AI for Dark Web threat intelligence gathering – Source: www.lastwatchdog.com
Source: www.lastwatchdog.com – Author: bacohido Tel Aviv, Israel – June 14, 2023 – Cybersixgill, the global cyber threat intelligence data provider, announced today Cybersixgill IQ, its new generative AI, representing a...
Malicious Actors Exploit GitHub to Distribute Fake Exploits – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A series of malicious GitHub repositories masquerading as legitimate security research projects have been discovered. VulnCheck researcher Jacob Baines shared the...
PII Exposed: Unauthenticated IDOR in WooCommerce Stripe Plugin – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A critical security vulnerability has been discovered in the popular WooCommerce Stripe Gateway plugin, potentially exposing users’ personally identifiable information (PII). The...