The content you are trying to access is private only to member users of the site. You must have a free membership at CISO2CISO.COM to access...
Day: June 28, 2023
Stalkerware Vendor Hacked – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier The stalkerware company LetMeSpy has been hacked: TechCrunch reviewed the leaked data, which included years of victims’ call logs and...
Typing Incriminating Evidence in the Memo Field – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier Don’t do it: Recently, the manager of the Harvard Med School morgue was accused of stealing and selling human body...
Reduce Risk Efficiently & Save Time with Prioritized Actions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Tally Shea Reading Time: 7 minutes Let’s establish the problem: practitioners are experiencing alert fatigue – desensitized, overwhelmed, and unable to manage...
Ironic: LetMeSpy Spyware Hackers Were Hacked (by Hackers) – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Content warning: Abuse, stalking, controlling behavior. LetMeSpy is a hacking tool used for stalking and spying on spouses, although its...
BSidesSF 2023 – Reed Loden, Tom Alcock, Mike McBryde, Coleen Coolidge, Kevin Hanaford – First Security Hire: Building A Security Roadmap And Team From Scratch – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Hot Topics Reduce Risk Efficiently & Save Time with Prioritized Actions Ironic: LetMeSpy Spyware Hackers Were Hacked (by Hackers) BSidesSF...
Look Ma, G2 Awarded Us with a Giant Stack of Badges – Source: securityboulevard.com
Source: securityboulevard.com – Author: Robert Hilson We don’t like to toot our own horn here at Apptega. But when our customers do it for us –...
Sowing Chaos and Reaping Rewards in Confluence and Jira – Source: securityboulevard.com
Source: securityboulevard.com – Author: Craig Wright Introduction Let me paint a picture for you. You’re on a red team operation, operating from your favorite C2, and...
New Capabilities in Fairwinds Insights: Custom Fields and Issue Types – Source: securityboulevard.com
Source: securityboulevard.com – Author: Liz Coolman If you are managing development teams using Kubernetes, you need to be able to easily find, triage, and fix problems...
Seceon Hires Peter Christou to Drive UK and EU Expansion – Source: securityboulevard.com
Source: securityboulevard.com – Author: Pushpendra Mishra Seceon, the pioneer of the first cybersecurity platform that augments and automates security operations services for MSPs and MSSPs, with an AI...
How to Manage Security Risks in a Supply Chain – Source: securityboulevard.com
Source: securityboulevard.com – Author: Cavelo Blog As your business becomes increasingly reliant on vendors, suppliers and providers to support operations or deliver goods and services, managing...
Frontend Developers: Security Champions of the New Age – Source: securityboulevard.com
Source: securityboulevard.com – Author: Or Weis Web development has undergone dramatic changes since its inception. However, one pervasive problem still exists: Frontend developers are still required...
European Cyber Agency Remains Underfunded – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Cyberwarfare / Nation-State Attacks , Fraud Management & Cybercrime ENISA Chief Says Lack of Appropriate Funding Continues to Be...
Application Security Testing vs. API Security Testing – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 API Security How They Differ & How Noname Security Active Testing Helps Your Business Shift Left Shay Levi • June 27,...
Cisco XDR: Making Defenders’ Lives Better – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cisco connected the world; who better to defend it? This is the mindset Carlos Diaz brings to the new Cisco XDR...
Astrix Security Raises $25M to Protect Nonhuman Identities – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Identity & Access Management , Next-Generation Technologies & Secure Development , Security Operations Cash Will Allow Astrix to Bring Threat Detection,...
Ukraine Cracks Down on Investment Scams, Raids Call Centers – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management Cyber Police Raid More Than a Dozen Call Centers Staffed by...
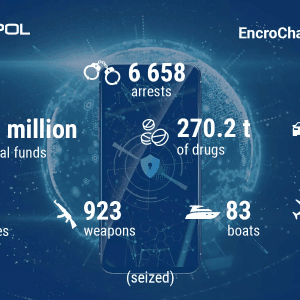
EncroChat Disruption Leads to Arrest of Over 6,000 Suspects – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Cybercrime , Fraud Management & Cybercrime , Government European Authorities Also Confiscated 900 Million Euros Plus Drugs and Weapons Akshaya Asokan...
Hackers Use PindOS Javascript Dropper to Deploy Bumblebee, IcedID Malware – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Threat actors use a new strain of JavaScript dropper that deploys malware like Bumblebee and IcedID and has a low...
New Mockingjay Process Injection Method Enables Malware Evade EDR Tools – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Livia Gyongyoși Researchers found a new process injection technique dubbed Mockingjay that enables hackers to bypass EDR solutions. The method allows threat...
Saudi Arabia’s Cyber Capabilities Ranked Second Globally – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The Kingdom of Saudi Arabia has secured second place in the Global Cybersecurity Index in the World...
Generative AI Projects Pose Major Cybersecurity Risk to Enterprises – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Organizations’ rush to embrace generative AI may be ignoring the significant security threats that large language model...
3 Strategies for Bringing Rigor to Software Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Chris Eng, Chief Research Officer, Veracode We’re in the midst of a transformational shift in software security. Companies will soon bear responsibility...
Open Source LLM Projects Likely Insecure, Risky to Use – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading There is a lot of interest in integrating generative AI and other artificial intelligence applications into existing...
Jscrambler Launches JavaScript Scanner for PCI DSS 4.0 Compliance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading Jscrambler has released a free tool to help companies check the JavaScript code running on their e-commerce...
Protecting Small Businesses From Ransomware on a Budget – Source: www.darkreading.com
Source: www.darkreading.com – Author: Sue Poremba, Contributing Writer If your organization is hit with a ransomware attack, it’s going to cost you. According to Verizon’s 2023...
Cequence Security Adds Generative AI to API Security – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading API security company Cequence Security has updated its API protection platform with generative AI and no-code security automation...
Experts warn of a spike in May and June of 8Base ransomware attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers warn of a massive spike in May and June 2023 of the activity associated with the ransomware group named 8Base....
Critical SQL Injection flaws in Gentoo Soko can lead to Remote Code Execution – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini SQL injection vulnerabilities in Gentoo Soko could lead to remote code execution (RCE) on impacted systems. SonarSource researchers discovered two...
EncroChat dismantling led to 6,558 arrests and the seizure of $979M in criminal funds – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Europol announced that the takedown of the EncroChat encrypted chat network has led to the arrest of 6,558 people and...