Source: www.bleepingcomputer.com – Author: Sergiu Gatlan On Thursday, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added six more security flaws to its known exploited vulnerabilities...
Day: June 22, 2023
Mirai botnet targets 22 flaws in D-Link, Zyxel, Netgear devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas A variant of the Mirai botnet is targeting almost two dozen vulnerabilities aiming to take control of D-Link, Arris, Zyxel,...
Microsoft: Hackers hijack Linux systems using trojanized OpenSSH version – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft says Internet-exposed Linux and Internet of Things (IoT) devices are being hijacked in brute-force attacks as part of a...
VMware fixes vCenter Server bugs allowing code execution, auth bypass – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan VMware has addressed multiple high-severity security flaws in vCenter Server, which can let attackers gain code execution and bypass authentication...
Millions of GitHub repos likely vulnerable to RepoJacking, researchers say – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Millions of GitHub repositories may be vulnerable to dependency repository hijacking, also known as “RepoJacking,” which could help attackers deploy...
DuckDuckGo browser for Windows available for everyone as public beta – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas DuckDuckGo has released its privacy-centric browser for Windows to the general public. It is a beta version available for download...
What Is CIAM? – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Antonia Din CIAM stands for Customer Identity and Access Management. It refers to a system or set of processes and tools created...
North Korean APT37 Exploits New FadeStealer Malware – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian The hacking group known as APT37, also referred to as StarCruft, Reaper, or RedEyes, has employed a new malware called...
Threat Actors Claim International Finance Corporation (IFC) Attack – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian The International Finance Corporation (IFC), a member of the World Bank Group and the largest development institution in the world,...
RedClouds APT Deploys RDStealer Against Remote Desktop – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Mihaela Marian RedClouds is a recently uncovered cyberespionage and hacking campaign that uses RDStealer malware to steal data from drives shared over...
Maltego: Check how exposed you are online – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Sol González A primer on how to use this powerful tool for uncovering and connecting information from publicly available sources It’s a...
Going on vacation soon? Stay one step ahead of travel scammers – Source: www.welivesecurity.com
Source: www.welivesecurity.com – Author: Phil Muncaster From bogus free trips to fake rental homes, here are some of the most common online threats you should look...
Get three years of a powerful VPN plus 30 days of anti-virus protection for $30 – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: TechRepublic Academy on June 22, 2023, 5:33 AM EDT Get three years of a powerful VPN plus 30 days of anti-virus protection...
Remote work and the cloud create new endpoint security challenges – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Drew Robb Cybersecurity has always been challenging, but with the cloud becoming more complex, the Internet of Things more advanced and remote...
Safeguarding customer information policy – Source: www.techrepublic.com
Source: www.techrepublic.com – Author: Data breaches can cost companies tens of thousands of dollars or more and can pose a significant risk to company operations and...
Survey Surfaces Multiple Cloud Security Contradictions – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A survey of 500 security, IT and engineering professionals published today found that nearly half (49%) experienced a data breach...
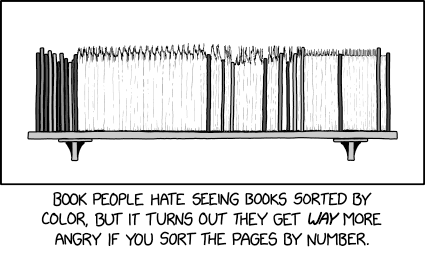
Randall Munroe’s XKCD ‘Bookshelf Sorting’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Web Application Security Vulnerabilities – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers Web applications have become a vital part of any business, especially as many businesses continue to realize their digital transformations....
AI as Sensemaking for Public Comments – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bruce Schneier It’s become fashionable to think of artificial intelligence as an inherently dehumanizing technology, a ruthless force of automation that has...
BSidesSF 2023 – Sal Olivares – How Segment Proactively Protects Customer’s API keys – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
PyPI Attackers Still At It: Malicious Packages Drop Trojans and Info-stealers – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ax Sharma Hot Topics Survey Surfaces Multiple Cloud Security Contradictions Randall Munroe’s XKCD ‘Bookshelf Sorting’ Web Application Security Vulnerabilities How to Delete...
News Alert: Cynomi launches first of its kind directory of virtual CISO providers – Source: securityboulevard.com
Source: securityboulevard.com – Author: bacohido Tel Aviv, Israel, June 23, 2023 — The industry’s first-ever directory of virtual Chief Information Security Officer service providers has gone...
Security Fixes Released for Node.js – Source: securityboulevard.com
Source: securityboulevard.com – Author: Flashpoint Intel Team Table Of Contents New releases of the popular Node.js JavaScript framework are available to address multiple vulnerabilities. The 16.x...
HYAS Protection for growing businesses – Source: securityboulevard.com
Source: securityboulevard.com – Author: HYAS Securing SMB Success: The Indispensable Role of Protective DNS Cyber attacks pose as much risk to small and medium-sized businesses (SMBs)...
LockBit Green and phishing that targets organizations – Source: securelist.com
Source: securelist.com – Author: GReAT Introduction In recent months, we published private reports on a broad range of subjects. We wrote about malware targeting Brazil, about...
Patch Now: Cisco AnyConnect Bug Exploit Released in the Wild – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading A security researcher has dropped a proof-of-concept (POC) exploit for a just-patched, high-severity security vulnerability in Cisco’s...
6 Attack Surfaces You Must Protect – Source: www.darkreading.com
Source: www.darkreading.com – Author: Microsoft Security, Microsoft Greater connectivity and enhanced digital operations can deliver a number of business benefits, but they also create a broader,...
USB Drives Spread Spyware as China’s Mustang Panda APT Goes Global – Source: www.darkreading.com
Source: www.darkreading.com – Author: Elizabeth Montalbano, Contributor, Dark Reading Espionage malware that spreads by self-propagating through infected USB drives is back, surfacing recently in an incident...
IT Staff Increasingly Saddled With Data Protection Compliance – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dan Raywood, Senior Editor, Dark Reading INFOSEC23 – London – Compliance with data-protection requirements remains one of the cornerstones of cybersecurity and risk...
Lessons From a Pen Tester: 3 Steps to Stay Safer – Source: www.darkreading.com
Source: www.darkreading.com – Author: Jim Broome, President & CTO, DirectDefense Having been in the cybersecurity industry since the early ’90s, I’ve witnessed its transformation over many...