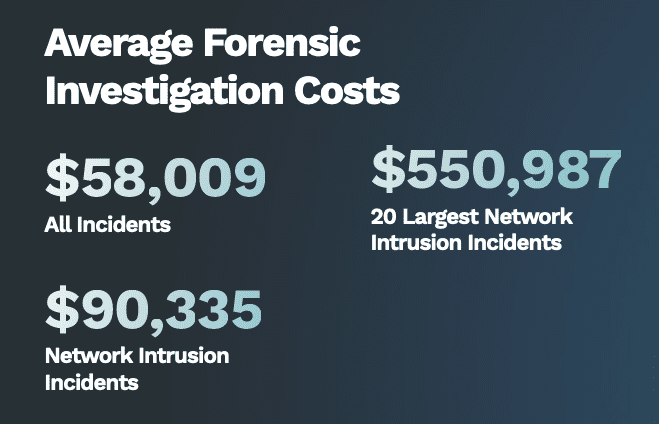
Source: www.darkreading.com – Author: Kelly Jackson Higgins, Editor-in-Chief, Dark Reading When more than a dozen Fortinet FortiGate firewalls mysteriously crashed and failed to properly reboot last...
Month: May 2023
Check Point Product Sales Slump as Customers Delay Purchases – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Network Firewalls, Network Access Control , Security Operations CEO Gil Shwed Pushes for More Productive Sales Force Amid Postponed Refresh Michael...
Killer Use Cases for AI Dominate RSA Conference Discussions – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Attack Surface Management , Cybercrime Use Cases: Cybersecurity Offense, Defense and Safeguarding AI Itself, Experts...
APAC Webinar | Putting Privileged Access Management, Just-in-Time Access, and Identity Security Together – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Thank you for registering with ISMG Complete your profile and stay up to date Need help registering? Contact Support Original Post...
Live Masterclass I 5 Things To Do When Your Organization Becomes the Victim of a Phishing Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 James McQuiggan Security Awareness Advocate, KnowBe4 James McQuiggan is a Security Awareness Advocate for KnowBe4. Prior to joining KnowBe4, McQuiggan worked...
How to Better Educate ‘Citizen Data Scientists’ on AI and ML – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Artificial Intelligence & Machine Learning , Events , Next-Generation Technologies & Secure Development Tom Scanlon of Carnegie Mellon University on New...
Apple’s first Rapid Security Response patch fails to install on iPhones – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Apple has launched the first Rapid Security Response (RSR) patches for iOS 16.4.1 and macOS 13.3.1 devices, with some users having...
Twitter outage logs you out and won’t let you back in – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams Update: The outage appears to be resolved and Twitter users can once again log into the desktop site. A Twitter...
New LOBSHOT malware gives hackers hidden VNC access to Windows devices – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Lawrence Abrams A new malware known as ‘LOBSHOT’ distributed using Google ads allows threat actors to stealthily take over infected Windows devices...
T-Mobile discloses second data breach since the start of 2023 – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan T-Mobile disclosed the second data breach of 2023 after discovering that attackers had access to the personal information of hundreds...
Registration Now Open: 2023 ICS Cybersecurity Conference | Atlanta – Source: www.securityweek.com
Source: www.securityweek.com – Author: Mike Lennon SecurityWeek’s ICS Cybersecurity Conference is back in Atlanta October 23-26, 2023. Registration is now open, and we hope you can join us...
New ‘Lobshot’ hVNC Malware Used by Russian Cybercriminals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Russian cybercrime group TA505 has been observed using new hVNC (Hidden Virtual Network Computing) malware in recent attacks, threat intelligence...
Reigning in ‘Out-of-Control’ Devices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Matt Wilson Endpoint detection and response (EDR) has demonstrated clear value in protecting endpoints, and in many ways provides unique visibility into...
Companies Increasingly Hit With Data Breach Lawsuits: Law Firm – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Lawsuits filed against companies that have suffered a data breach are increasingly common, with action being taken more frequently even...
CISA Asks for Public Opinion on Secure Software Attestation – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire The US Cybersecurity and Infrastructure Security Agency (CISA) has announced that proposed guidance for secure software development is now open...
‘BouldSpy’ Android Malware Used in Iranian Government Surveillance Operations – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Mobile security firm Lookout has analyzed a piece of Android spyware used by the Iranian government to surveil minority groups...
US Wellness Provides Notification of Data Security Incident – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 RALEIGH, N.C., HARRISBURG, Pa., and PHILADELPHIA, April 28, 2023 /PRNewswire/ — US Wellness has learned of a data security incident that may have involved personal...
Enterprise Strategy Group Research Reveals 75% of Organizations Change or Update APIs on a Daily or Weekly Basis – Source: www.darkreading.com
Source: www.darkreading.com – Author: 1 PALO ALTO, Calif., May 1, 2023 – Data Theorem, Inc., a leading provider of modern application security, today announced the “Securing...
FBI Focuses on Cybersecurity With $90M Budget Request – Source: www.darkreading.com
Source: www.darkreading.com – Author: Nate Nelson, Contributing Writer, Dark Reading The FBI is requesting more than $63 million in new funding to fight cyber threats in...
APT28 Employs Windows Update Lures to Trick Ukrainian Targets – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The Russia-linked APT28 hacking group targeted Ukrainian government bodies in a spear-phishing campaign that uses phony “Windows...
BlackCat Trolls Western Digital With Leaked Response Meeting Image – Source: www.darkreading.com
Source: www.darkreading.com – Author: Dark Reading Staff, Dark Reading The ransomware actor–threat hunter relationship just got extremely personal. The BlackCat gang decided to add the professional...
What the Cybersecurity Industry Can Learn From the SVB Crisis – Source: www.darkreading.com
Source: www.darkreading.com – Author: Sravish Sridhar, CEO & Founder, TrustCloud No one can be an expert on everything, which is why companies aren’t run by just...
Name That Edge Toon: Fare Thee Well – Source: www.darkreading.com
Source: www.darkreading.com – Author: John Klossner, Cartoonist You never know what you’ll come across in your travels. Your mission: Write a witty cybersecurity-related caption to explain...
Software Packages, Do We Even Need Them? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Prescott Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
Radware Report Sees Religion Fueling More DDoS Attacks – Source: securityboulevard.com
Source: securityboulevard.com – Author: Michael Vizard A report published by Radware found that, in two months alone, hacktivists claimed to launch more than 1,800 distributed denial-of-service...
RSA Conference 2023 Highlights: Power up your API Security – Source: securityboulevard.com
Source: securityboulevard.com – Author: Linda Sim This week the Cequence Security team hit the floor at RSAC 2023. We appreciate everyone who stopped by our booth...
Apache Superset RCE Vulnerability CVE-2023-27524 Highlights Ongoing Issues with Flask AppBuilder, Joining List of Previously Discovered CVEs – Source: securityboulevard.com
Source: securityboulevard.com – Author: Ofri Ouzan On Apr 24, 2023 Naveen Sunkavally, Chief Architect at Horizon3.ai, announced the discovery of a new vulnerability, CVE-2023-27524, in Apache...
Prevent financial leakage – transaction analytics – Source: securityboulevard.com
Source: securityboulevard.com – Author: Emma Kelly We live in a digital universe where an increasing number of businesses are adopting enterprise cloud applications unleashing new waves...
EV Charging Station Applications – a Growing Cyber Security Risk – Source: securityboulevard.com
Source: securityboulevard.com – Author: Uri Dorot EV applications usually interact with each other and third-party services and platforms via APIs or JavaScript plugins. These applications process...
RiskLens Data Scientist Justin Theriot Recognized by Zywave, SIRAcon – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeff B. Copeland Recognition for the industry-leading research our data science team generates to support cyber risk quantification software and services at...