Source: securityboulevard.com – Author: Digital Defense by HelpSystems Every release helps update and pave the way for additional features and improvements. Based off of user feedback,...
Month: May 2023
Cybersecurity Staffing Services: A Key to Protecting Your Business – Source: securityboulevard.com
Source: securityboulevard.com – Author: Geetha R In an increasingly interconnected world, where technology has become an integral part of our daily lives, ensuring the security of...
Who Owns Security in Multi-Cloud Operations? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jeff Wierer The best-kept secret is the one that is never shared. In today’s technology environment, that is even more true. Where...
Unleash the power of a CREST accredited penetration testing provider: A Comprehensive Guide – Source: securityboulevard.com
Source: securityboulevard.com – Author: Strobes Blog : Vulnerability Management, Penetration Testing, DevSecOps In today’s world, cyber threats are becoming more frequent and advanced, making it crucial...
Comparing Cloud Providers’ Shared Responsibility Models – Source: securityboulevard.com
Source: securityboulevard.com – Author: Bill Doerrfeld More and more enterprises are becoming multi-cloud. And when evaluating cloud service providers (CSPs) for different needs, one important factor...
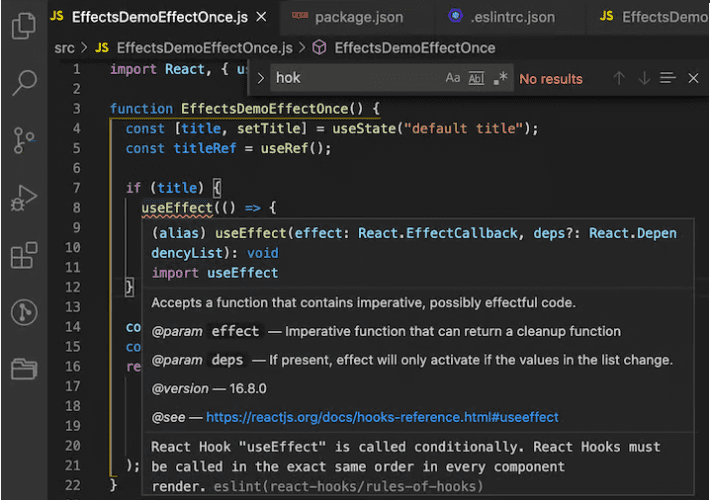
How Do You Handle Side Effects of ReactJS? – Source: securityboulevard.com
Source: securityboulevard.com – Author: UI Designer Using the useEffect To Handle React Side-Effect In ReactJS application development, using the useEffect hook is the most prominent way...
Cloud Computing The Prescription for Modern Healthcare Challenges – Source: securityboulevard.com
Source: securityboulevard.com – Author: seo-ccadmin Cloud computing has become a game-changer for many industries, and healthcare is no exception. Healthcare providers are starting to recognize the...
Android Fingerprint Biometrics Fall to ‘BrutePrint’ Attack – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Endpoint Security , Identity & Access Management , Security Operations Dictionary Attack Plus Neural Network Fools Security Checks, Researchers Find Mathew...
Facebook Ordered to Suspend Data Transfers to US From Europe – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 General Data Protection Regulation (GDPR) , Standards, Regulations & Compliance European Data Authorities Fine Social Media Giant 1.2 Billion Euros Akshaya...
Live Webinar | The Secret Sauce to Secrets Management – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Itzik Alvas CEO and Co-founder, Entro Security tzik has 15+ years of R&D and management experience. He started his career as...
Open-Source Info Stealer RAT Hides in Malicious npm Packages – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Next-Generation Technologies & Secure Development , Threat Intelligence TurkoRat Capable of Credential Harvesting, Contains Features Such as Wallet...
Google Is Not Deleting Old YouTube Videos – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier HomeBlog Google Is Not Deleting Old YouTube Videos Google has backtracked on its plan to delete inactive YouTube videos—at least...
GAO Tells Federal Agencies to Fully Implement Key Cloud Security Practices – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire A new US Government Accountability Office (GAO) report shows that the Departments of Agriculture, Homeland Security (DHS), Labor, and the...
Food Distributor Sysco Says Cyberattack Exposed 126,000 Individuals – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Food distributor Sysco Corporation is informing over 126,000 individuals that their personal information was compromised in a recent cyberattack. A...
Dish Ransomware Attack Impacted Nearly 300,000 People – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Satellite TV giant Dish Network has started notifying the individuals whose data was compromised in a recent ransomware attack. The...
Microsoft: BEC Scammers Use Residential IPs to Evade Detection – Source: www.securityweek.com
Source: www.securityweek.com – Author: Ionut Arghire Cybercriminals are using residential IP addresses in business email compromise (BEC) attacks to make them seem locally generated and evade...
Meta Fined Record $1.3 Billion and Ordered to Stop Sending European User Data to US – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press The European Union slapped Meta with a record $1.3 billion privacy fine Monday and ordered it to stop transferring user...
China Tells Tech Manufacturers to Stop Using Micron Chips, Stepping Up Feud With United States – Source: www.securityweek.com
Source: www.securityweek.com – Author: Associated Press Stepping up a feud with Washington over technology and security, China’s government on Sunday told users of computer equipment deemed...
Samsung Smartphone Users Warned of Actively Exploited Vulnerability – Source: www.securityweek.com
Source: www.securityweek.com – Author: Eduard Kovacs Samsung smartphone users have been warned by the vendor and the US Cybersecurity and Infrastructure Security Agency (CISA) about a...
Weekly Update 348 – Source: www.troyhunt.com
Source: www.troyhunt.com – Author: Troy Hunt I feel like the .zip TLD debate is one of those cases where it’s very easy for the purest security...
PyPI Repository temporarily suspends user sign-ups and package uploads due to ongoing attacks – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini The Python Package Index (PyPI) maintainers have temporarily disabled the sign up and package upload processes due to an ongoing...
Security Affairs newsletter Round 420 by Pierluigi Paganini – International edition – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Privacy Overview This website uses cookies to improve your experience while you navigate through the website. Out of these cookies,...
US government seizes 13 domains linked to DDoS attacks
The United States (US) federal government has seized 13 domains linked to ‘booter’ websites that offered distributed denial of service (DDoS)-attacks-for-hire services. So-called ‘booter’ sites allow...
Microsoft Edge is getting ‘Edge for Gamers’ mode – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Mayank Parmar Microsoft is doubling its efforts to court the gaming community with a new feature, “Edge for Gamers” mode, which promises...
Google will delete accounts inactive for more than 2 years – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Google has updated its policy for personal accounts across its services to allow a maximum period of inactivity of two...
Android phones are vulnerable to fingerprint brute-force attacks – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Bill Toulas Researchers at Tencent Labs and Zhejiang University have presented a new attack called ‘BrutePrint,’ which brute-forces fingerprints on modern smartphones...
BSidesSF 2023 – Abhinav SP – Making of the BSides SF Astronaut Badge – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-abhinav-sp-making-of-the-bsides-sf-astronaut-badge/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
BSidesSF 2023 – Rami McCarthy, Lea Snyder, Hasnain Lakhani, Kurt Boberg – Level Up Your Career: A Panel on Staff+ Engineering – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Bloggers Network Home » Security Bloggers Network » BSidesSF 2023 – Rami McCarthy, Lea Snyder, Hasnain Lakhani, Kurt Boberg...
Open-Source Infostealer RAT Hidden in Malicious NPM Packages – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Application Security , Next-Generation Technologies & Secure Development , Threat Intelligence TurkoRat Capable of Credential Harvesting, Possesses Features Like Wallet Grabber...
Google pushes .zip and .mov domains onto the Internet, and the Internet pushes back – Source: www.proofpoint.com
Source: www.proofpoint.com – Author: 1 WHAT COULD POSSIBLY GO WRONG? — Will new TLDs undo decades of work to stop malicious links? Dan Goodin – May...