Source: www.techrepublic.com – Author: TechRepublic Academy on May 30, 2023, 7:00 AM EDT Get 9 cybersecurity courses for just $46 Learn ethical hacking and other cybersecurity...
Day: May 30, 2023
Microsoft shares fix for cameras not working on Surface laptops – Source: www.bleepingcomputer.com
Source: www.bleepingcomputer.com – Author: Sergiu Gatlan Microsoft has shared a temporary fix for a widespread issue triggered by a buggy driver that causes built-in cameras on...
Randall Munroe’s XKCD ‘The Six Platonic Solids’ – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Community Chats Webinars Library Home Cybersecurity News Features Industry Spotlight News...
‘Predator’ — Nasty Android Spyware Revealed – Source: securityboulevard.com
Source: securityboulevard.com – Author: Richi Jennings Intellexa’s ‘mercenary spyware’ chains five unpatched bugs. Malware used by nation-states to target journalists, activists and opposition pols has been...
Crypto Scams – Source: securityboulevard.com
Source: securityboulevard.com – Author: Jenn Jeffers Crypto Scams: How Arkose MatchKey Bankrupted the Efforts of a Russian Hacker “My partners and I lost time and money...
BSidesSF 2023 – Breanne Boland – New Apps, Good Snacks: Effective Threat Modeling for New Territory – Source: securityboulevard.com
Source: securityboulevard.com – Author: Marc Handelman Security Boulevard The Home of the Security Bloggers Network Original Post URL: https://securityboulevard.com/2023/05/bsidessf-2023-breanne-boland-new-apps-good-snacks-effective-threat-modeling-for-new-territory/ Category & Tags: Security Bloggers Network,appsec education,BsidesSF,BSidesSF...
Is Your Cybersecurity Vendor Built to Thrive or Struggling to Survive? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Kelsey Gast The last several years were an incredible run for the cybersecurity industry. Even as the pandemic put pressure on many...
Invoice and CEO Scams Dominate Fraud Affecting Businesses – Source: www.databreachtoday.com
Source: www.databreachtoday.com – Author: 1 Card Not Present Fraud , Finance & Banking , Fraud Management & Cybercrime UK Financial Services Firms Record $1.5 Billion in...
Ransomware: A Predictable Response to Market Forces – Source: securityboulevard.com
Source: securityboulevard.com – Author: Lauren Yacono Considering that most cybercrime is financially motivated, tactics will evolve that streamline the route from compromise to cashout. Reselling stolen...
Weighing the Pros and Cons of Open-Source Software to Support Critical Infrastructure – Source: securityboulevard.com
Source: securityboulevard.com – Author: Eric Mizell Fifteen years ago, I had a colleague say to me, “Open-source software is not free; it means access to the...
Failure to Pay Ransom: Negligence? – Source: securityboulevard.com
Source: securityboulevard.com – Author: Mark Rasch Lehigh Valley Health Network is a health care network based in Allentown, Pennsylvania that serves the eastern and northeastern part...
Understanding the Progression of a Ransomware Attack – Source: securityboulevard.com
Source: securityboulevard.com – Author: Sue Poremba Everyone should be familiar with ransomware and its impact on businesses by now. But while you may understand the very...
Brute-Forcing a Fingerprint Reader – Source: www.schneier.com
Source: www.schneier.com – Author: Bruce Schneier It’s neither hard nor expensive: Unlike password authentication, which requires a direct match between what is inputted and what’s stored...
Ransomware Gangs Adopting Business-like Practices to Boost Profits – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Ransomware gangs are using a variety of business-like practices to boost profits, making it more difficult for defenders to differentiate various...
Dark Web Data Leak Exposes RaidForums Members – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Nearly half a million members of a notorious cybercrime forum have had their details publicly exposed after a key database was...
Retailer Database Error Leaks Over One Million Customer Records – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 A database configuration error at a popular automotive retailer led to the exposure of 1TB of records, including customers’ personal information,...
Nine Million MCNA Dental Customers Hit by Breach – Source: www.infosecurity-magazine.com
Source: www.infosecurity-magazine.com – Author: 1 Millions of customers of one of America’s largest dental health insurers have had their personal information compromised after a ransomware breach....
Hackers Win $105,000 for Reporting Critical Security Flaws in Sonos One Speakers – Source:thehackernews.com
Source: thehackernews.com – Author: . May 30, 2023Ravie LakshmananZero Day / Vulnerability Multiple security flaws uncovered in Sonos One wireless speakers could be potentially exploited to...
CAPTCHA-Breaking Services with Human Solvers Helping Cybercriminals Defeat Security – Source:thehackernews.com
Source: thehackernews.com – Author: . May 30, 2023Ravie Lakshmanan Cybersecurity researchers are warning about CAPTCHA-breaking services that are being offered for sale to bypass systems designed...
Implementing Risk-Based Vulnerability Discovery and Remediation – Source:thehackernews.com
Source: thehackernews.com – Author: . In this day and age, vulnerabilities in software and systems pose a considerable danger to businesses, which is why it is...
Sneaky DogeRAT Trojan Poses as Popular Apps, Targets Indian Android Users – Source:thehackernews.com
Source: thehackernews.com – Author: . A new open source remote access trojan (RAT) called DogeRAT targets Android users primarily located in India as part of a...
RaidForums Members Data Leaked on New Hacking Forum – Source: heimdalsecurity.com
Source: heimdalsecurity.com – Author: Cristian Neagu Threat actors and security researchers now have access to a database for the notorious RaidForums hacking forums, giving them insight...
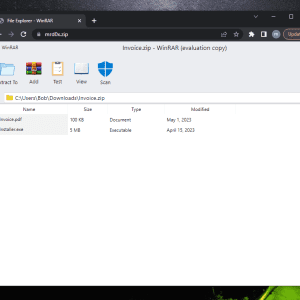
Beware of the new phishing technique “file archiver in the browser” that exploits zip domains – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini “file archiver in the browser” is a new phishing technique that can be exploited by phishers when victims visit a...
BrutePrint Attack allows to unlock smartphones with brute-forcing fingerprint – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Researchers devised an attack technique, dubbed BrutePrint Attack, that allows brute-forcing fingerprints on smartphones to bypass authentication. Researchers have devised...
Lockbit ransomware attack on MCNA Dental impacts 8.9M individuals – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Managed Care of North America (MCNA) Dental disclosed a data breach that impacted more than 8.9 million individuals. Managed Care...
New Go-written GobRAT RAT targets Linux Routers in Japan – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini A new Golang remote access trojan (RAT), tracked as GobRAT, is targeting Linux routers in Japan, the JPCERT Coordination Center warns....
Researchers analyzed the PREDATOR spyware and its loader Alien – Source: securityaffairs.com
Source: securityaffairs.com – Author: Pierluigi Paganini Cisco Talos and the Citizen Lab researchers have published a technical analysis of the powerful Android spyware Predator. Security researchers...
Upskilling the non-technical: finding cyber certification and training for internal hires – Source: www.csoonline.com
Source: www.csoonline.com – Author: Andrey Popov / Shutterstock Finding qualified staff to replace vacancies or build out an expanding team can be a nightmare for already...
Prevention-first: Protecting cities from ransomware – Source: www.cybertalk.org
Source: www.cybertalk.org – Author: slandau By Pete Nicoletti, Check Point Field CISO, Americas In recent months, several American cities were hit by debilitating and disruptive ransomware...
Invoice and CEO Scams Dominate Fraud Impacting Businesses – Source: www.govinfosecurity.com
Source: www.govinfosecurity.com – Author: 1 Card Not Present Fraud , Finance & Banking , Fraud Management & Cybercrime UK Financial Services Firms Record $1.5 Billion in...